Strategies to Defend Against IAM targeted Attacks

OVERVIEW
AWS Identity and Access Management (IAM) serves as both a user management system and a resource management console for AWS. In the realm of cybersecurity, the significance of Identity and Access Management and the associated risks are well recognized. Therefore, developing strategies to defend against IAM-targeted attacks is a top priority.
In this blog, we will discuss proactive approaches for detecting and securing Amazon IAM services in detail. Securing IAM requires a comprehensive strategy for monitoring and detection. By adopting various security measures such as Enable Multi-Factor Authentication (MFA, Apply the Principle of Least Privilege, Use Roles for Applications, Regularly Rotate Credentials, Implement Strong Password Policies, Monitor and Audit IAM Activity and continuously improving your processes, you can significantly enhance the security of your AWS IAM service and protect your valuable data from cyber threats.
List of Commonly Targeted IAM Bases attacks
Misconfiguration on IAM often leads to various security risks including compromising of user account or AWS resources
We will explore commonly observed attack investigations, including login brute forcing, MFA failed login activity, and investigating suspicious activities of users granted full privileges. We will outline their attack execution flow and proactive approaches for identifying and detecting these attacks.
Login brute forcing
As we know, IAM serves as a centralized AWS service for authorization and access control, making it a target for adversaries seeking initial access. Adversaries often employ brute forcing techniques, including brute forcing MFA, to bypass login restrictions.
NOTE: AWS authentication can be performed through various methods such as console login, login using access key and secret key, or accessing resources using session tokens.
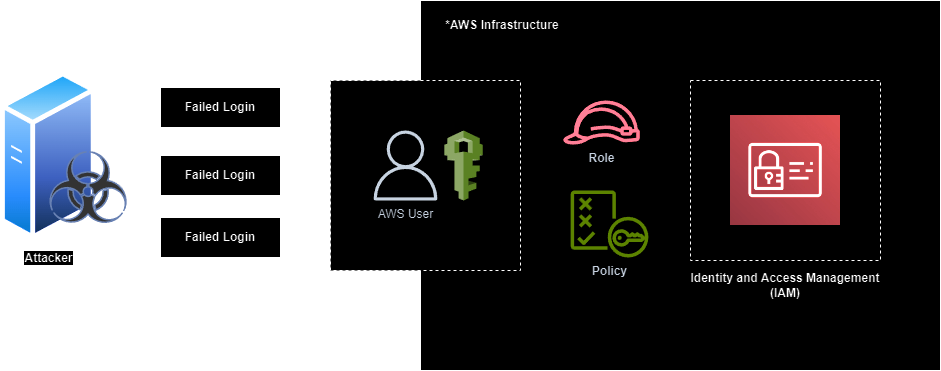
Identifying and detecting Login brute forcing
To detect and secure such activities, it is advisable to implement security measures such as enabling and configuring AWS Security Hub, or activating CloudTrail and CloudWatch logging. These logs should be forwarded to a SIEM service for in-depth analysis and investigation.
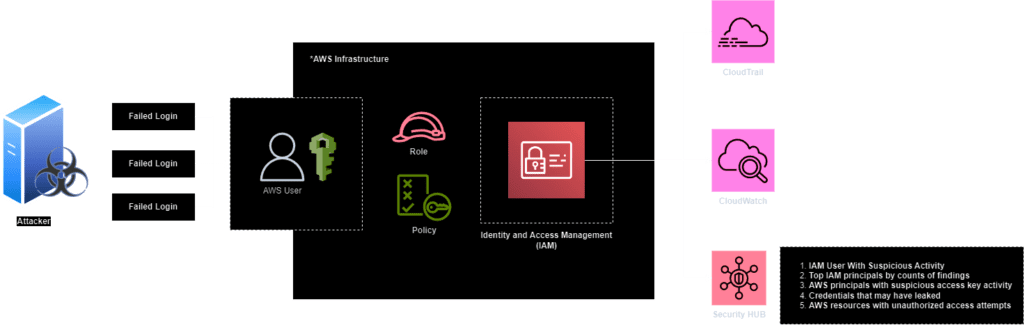
It’s been recommended to monitor the below mentioned API call for suspicious login activity
aws:signin | Used for AWS Management Console sign-in events. |
sts:AssumeRole | Used when a user assumes an IAM role, generating temporary security credentials. |
sts:GetSessionToken | Used to request temporary security credentials for AWS resources. |
iam:CreateLoginProfile | Used to create a password for an IAM user for AWS Management Console access. |
iam:CreateAccessKey | Used to create an access key for an IAM user. |
The logs for the above-mentioned API calls can be collected by AWS CloudTrail and simultaneously streamed to a centralized log monitoring SIEM for investigation and analysis purposes.
Overly Permissive Policies
The majority of cloud compromises occur due to overly permissive IAM policies. If a user with the privilege to assign and create policies is compromised, it often results in the creation of a new user with excessive privileges or the assignment of excessive privileges to existing users.
Most attacks exploiting overly permissive IAM policies appear to be initiated by insider threats or occur when user credentials are compromised or exposed. In such cases, attackers log in using the stolen credentials to perform various malicious operations
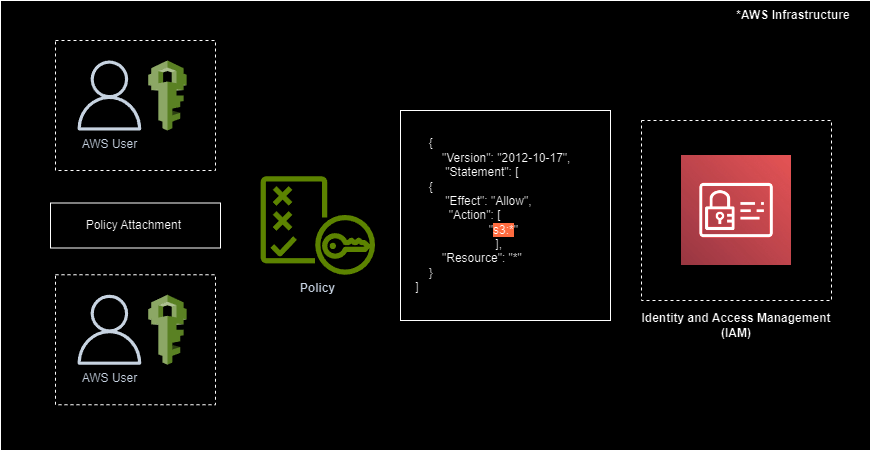
Identifying and detecting
To detect and secure overly permissive IAM policies, it is crucial to enable monitoring through CloudTrail logs. It is advisable to deploy security measures such as configuring AWS Config or accessing with IAM Policy Analyser. Forward these logs to a SIEM service for in-depth analysis and investigation.
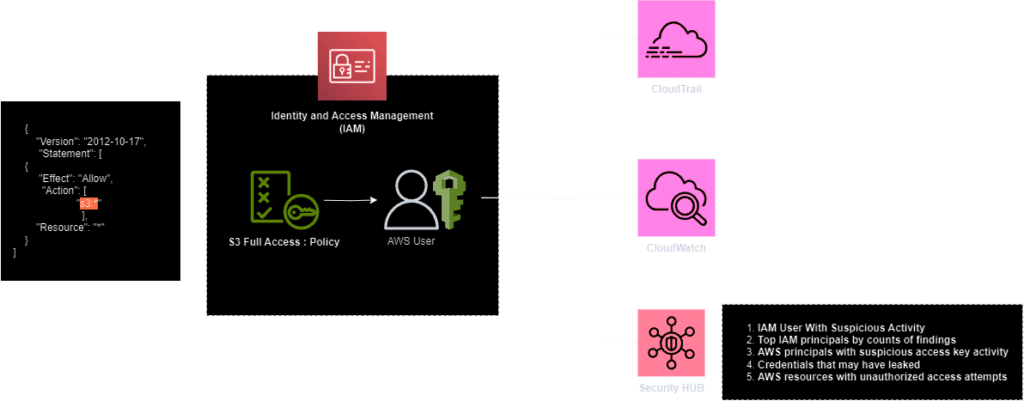
It’s been recommended to monitor the below mentioned API call for suspicious user policy updation activity
iam:CreatePolicy | Used to create a new IAM policy. |
iam:AttachUserPolicy | Used to attach a managed policy to a user |
iam:AttachGroupPolicy | Used to attach a managed policy to a group. |
iam:AttachRolePolicy | Used to attach a managed policy to a role. |
iam:PutUserPolicy | Used to attach an inline policy to a user |
The logs for the above-mentioned API calls can be collected by AWS CloudTrail and simultaneously streamed to a centralized log monitoring SIEM for investigation and analysis purposes.



































