Enterprise Security Controls Attack Specialist [CESC-AS]
- Advanced Penetration Testing Certification
- Offensive C# Trade-Craft & Windows API Abuse
- Advanced Active Directory Attacks
- Health Care Themed Cyber Range Lab
The courses contents are divided across 5 sections listed below:
Hands-on of Enterprise Security Controls
- Anti-Virus & End-Point Detection and Response (EDR)
- End-Point Defender Features & EDR Introduction)
- Directory-Level Controls & Linux Environment
- Enterprise Environment Overview
- Technologies Exploitation in Red Teaming
Implementation of Security Controls
- Virtual Environment Setup & configuration
- Host-Level Controls Setup
- Network-Level Controls Setup
- Linux Environment Setup
Offensive C# Tradecraft
- Virtual Environment Setup & configuration
- CSharp Essentials & CSharp Beginner
- Offensive C# Trade-Craft
Abusing Windows API
- Windows API Components
- Windows API Essentials
- Utilizing Windows API for Red Team Profit
- Advanced AV Bypass Scenario
Abusing/Evading Host & Network based security controls
- Host-Level Security Controls
- Network-Level Security Controls
- Enterprise Grade Lab Environment
- Scope of Engagement
- Lab Solution / walk-through in Video + PDF format
- Preparing for Examination
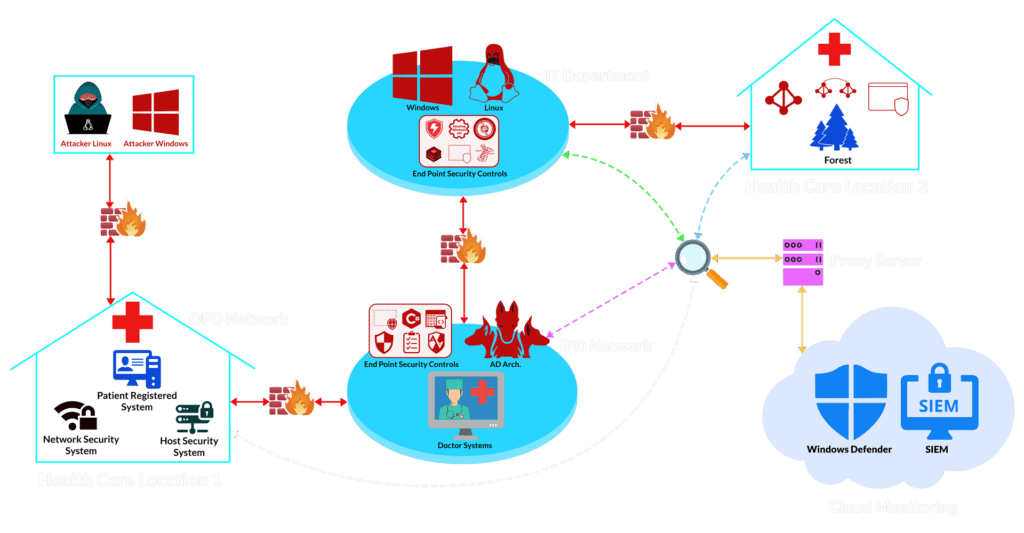
- Healthcare Simulation Lab with multiple attack paths
- Understand security controls architecture
- Follow MITRE ATT&CK to evade monitoring / detection applications
- Create & use custom tools in different scenarios
- Windows & Linux based Active directory scenario
- Learn advanced ways of Initial Access
Pre-requisites
Following are the requirements:
- Understanding of OS, Web & Network based attacks
- Understanding of Red Team Methodology
- Familiarity with Command line basics
Target Audience
Targeted Audience may include the following:
- Penetration Testers
- Security Engineers / Consultants
- Malware Developers (Beginner)
CWL Recommended
Enterprise Security Controls Attack Specialist [CESC-AS]
$299
Top Features:
- 30 Days Lab [Walk-through included]
- Health Care themed Cyber Range Lab
- Lifetime Course Access
- 250+ Pages PDF
- 12+ hours HD videos
- Instructions to Setup Controls Locally
- 2 Examination Attempts + Accredible Badge
Note: If you want to extend the days for lab access please drop a mail at:
[email protected]
Choose your journey and earn the Certified Enterprise Security Controls Attack Specialist Certification today
F.A.Q
- 250+ Pages PDF
- 12+ hours HD videos
- 30 Days Lab [Walk-through included]
- Health Care themed Cyber Range Lab
- Lifetime Course Access
- Instructions to Setup Controls Locally
- 2 Examination Attempts + Accredible Badge
Yes, whether you are on community plan or premium subscription, our support team is there for you 🙂
The course is delivered on -demand with a combination of online lectures, practical hands-on exercises, and virtual labs.
The duration of the Enterprise Security Controls Attack Specialist course may vary based on individual learning pace, but it typically takes around 2-4 months to complete.
Yes, After purchase you will get the life-time access.
The CESC-AS exam is a on-demand online practical hands-on assessment that evaluates the student’s ability to perform real-world red teaming engagements. Students are given specific scenarios and objectives to accomplish within a specified timeframe.
No, we only activate lab access upon request, which will be provided within 48 hours.
A: After completing the course, individuals can explore career opportunities such as:
-Security Controls Analyst
-Penetration Tester
-Vulnerability Analyst
-Security Consultant, or Security Engineer.
Refunds for premium subscription will NOT be provided until and unless cleared by our sales team.
Please email [email protected] for detailed clarification


































