The courses contents are divided across 4 sections listed below:
Attack Simulation
- Extensive OSINT Enumeration
- Exploit Remote Access Services (VDI, RDS etc)
- Realistic Initial Access Scenarios
- Custom Web & Escalation Scenarios
- Port Forwarding, various proxies etc
Abusing MS
- MS Exchange
- Active Directory Certificate Services
- Group Managed Service Account (gMSA)
- Linux Based KDC
- Cross-Forest Abuse Scenarios
Lateral Movement
- SSH over Kerberos (SSO)
- Multi-Factor Authentication Evasion
- Across Workstations (Windows & Linux)
- Abuse Internal Remote Services in Multi-OS environment
- Certificate Based Lateral Movement
Abuse Enterprise Grade Software
- Abuse Automation Software
- Weaponizing Visual Studio & Zoom
- Bastion Hosts
- Git Personal Access Tokens
- Understand & Exploit CI/CD Pipeline
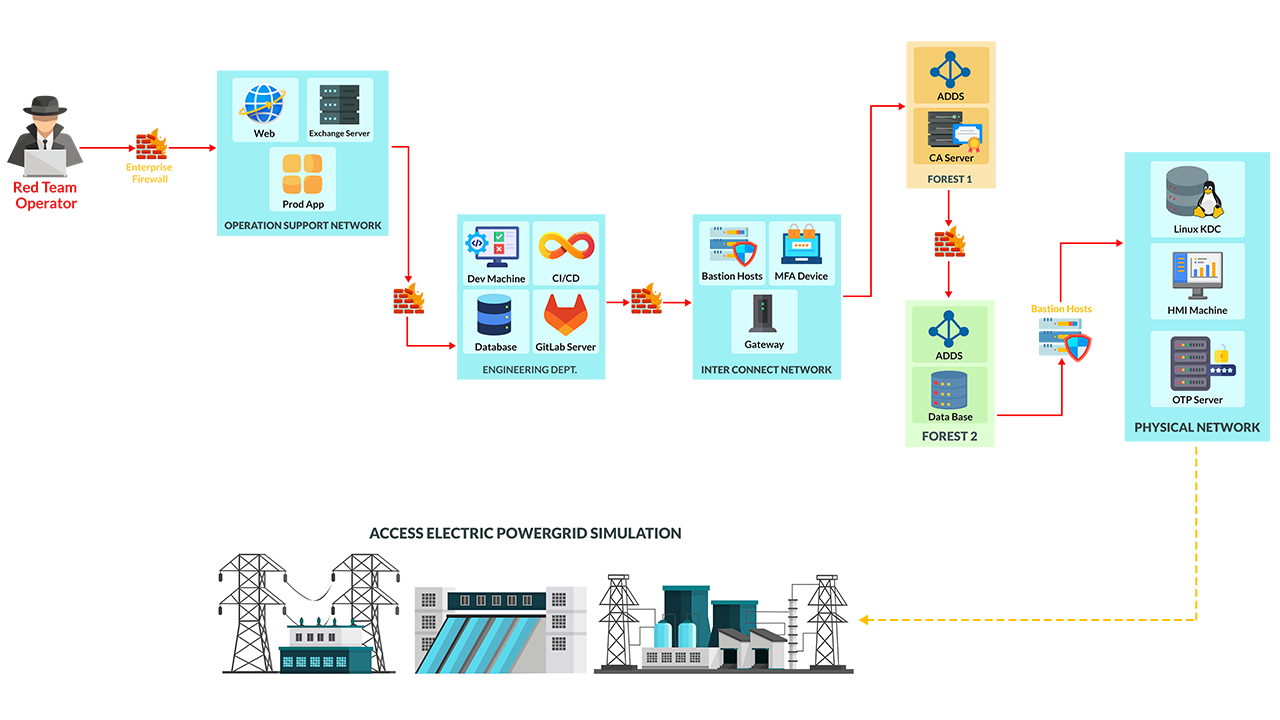
Cyber Range Lab Highlights
- Adversary Simulation in Electric PowerGrid
- 2 Unique Attack Paths
- Abuse Enterprise Grade Software
- Custom Initial Access Scenarios
- Compromising an Isolated (air-gapped type) Network
Pre-requisites
Following are the requirements:
- Understanding of Web & Network Pentesting
- Basics of Active Directory
- CLI
Target Audience
Designed specifically for intermediate to advanced professionals having interest in:
- Red Teaming
- Seasoned professionals
- Experienced in Offensive Information Security
Premium Version
Red Team Specialist [CRTS]
$199
Top features:
- 140+ Pages Premium Material
- 30 Days Challenge Lab
- 2 Unique Paths + 90+ Pages Walkthrough
- Electric PowerPlant Themed Lab
- 2 Exam Attempts + Accredible Badge
Note: If you want to extend the days for lab access please drop a mail at:
[email protected]
































