Server less Siege: Defend, Detect, Defeat

Serverless computing creates new security challenges while revolutionizing cloud applications. Through practical examples, defenses, and real-world attack scenarios, we examine both offensive and defensive strategies for protecting serverless systems in this blog.
Understanding Serverless Computing
Serverless computing is a cloud-native execution model where cloud providers manage the servers. Examples include:
- AWS Lambda
- Azure Functions
- Google Cloud Functions
Cost-effectiveness, auto-scaling, and lower maintenance are among the advantages. These characteristics, however, produce a dynamic attack surface that calls for certain security solutions.
Attack Scenarios in Server-less Computing
1. Denial of Wallet (DoW)
- Attack: An attacker floods the system with excessive invocations, causing unexpected and significant cost increases.
Denial-of-Wallet (DoW) exploits are similar to traditional denial-of-service (DoS) attacks in the sense that both are carried with the intent to cause disruption.
- Example: Sending a high volume of requests to trigger AWS Lambda functions.
Demo:
- Set up: Deploy an AWS Lambda function triggered by an HTTP API Gateway.
- Attack: Use tools like hey or ab to simulate high traffic to the endpoint.
- Outcome: Observe billing metrics and invocation logs in AWS CloudWatch.
Mitigation Steps:
- Implement rate limiting in API Gateway.
- Configure AWS Budgets to detect cost anomalies.
- Use AWS WAF to block abusive traffic patterns.
2. Event Injection
- Attack: Crafting malicious events to manipulate the behavior of serverless functions.
- Example: Modifying S3 bucket triggers to execute unauthorized code in AWS Lambda.
Demo:
- Set up: Deploy an AWS Lambda function triggered by S3 uploads.
- Attack: Upload a crafted file containing malicious input.
- Outcome: Exploit input validation flaws to manipulate function behavior.
Mitigation Steps:
- Apply JSON schema validation.
- Restrict event triggers to trusted sources using IAM conditions.
3. Privilege Escalation
- Attack: Leveraging overly permissive IAM roles assigned to serverless functions to gain unauthorized access to resources.
- Example: Using an AWS Lambda function to assume an IAM role with administrative privileges.
Demo:
- Set up: Assign an overly permissive role to a Lambda function.
- Attack: Use tools like awscli to list and access unauthorized resources.
- Outcome: Gain unauthorized access to sensitive cloud resources.
Mitigation Steps:
- Audit IAM roles using AWS IAM Access Analyzer.
- Apply least privilege to all roles and policies.
Solutions for Attack Scenarios
Challenge 1: Protect Against Denial of Wallet (DoW)
Objective: Limit excessive function invocations to prevent unexpected cost spikes.
Setup Instructions:
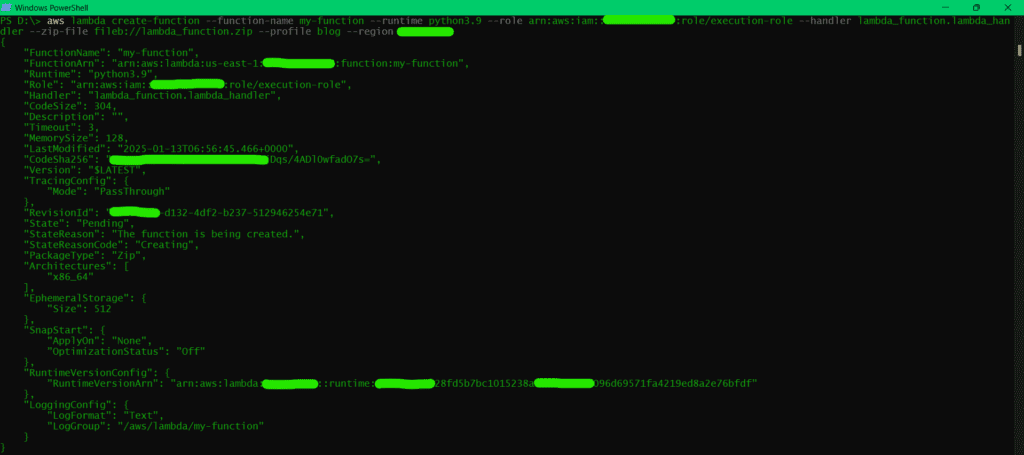
- Create a Serverless Function:
AWS Lambda:
aws lambda create-function \
--function-name my-function \
--runtime python3.9 \
--role arn:aws:iam::account-id:role/execution-role \
--handler lambda_function.lambda_handler \
--zip-file fileb://function.zip
2. Configure API Gateway:
- Use API Gateway to invoke the Lambda function.
- Set rate limits using Usage Plans:
- Go to API Gateway Console → Select API.
- Click Usage Plans → Create Usage Plan.
- Define request quotas (e.g., 100 requests per minute).
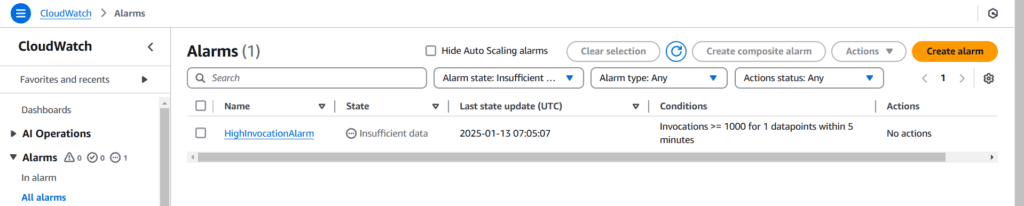
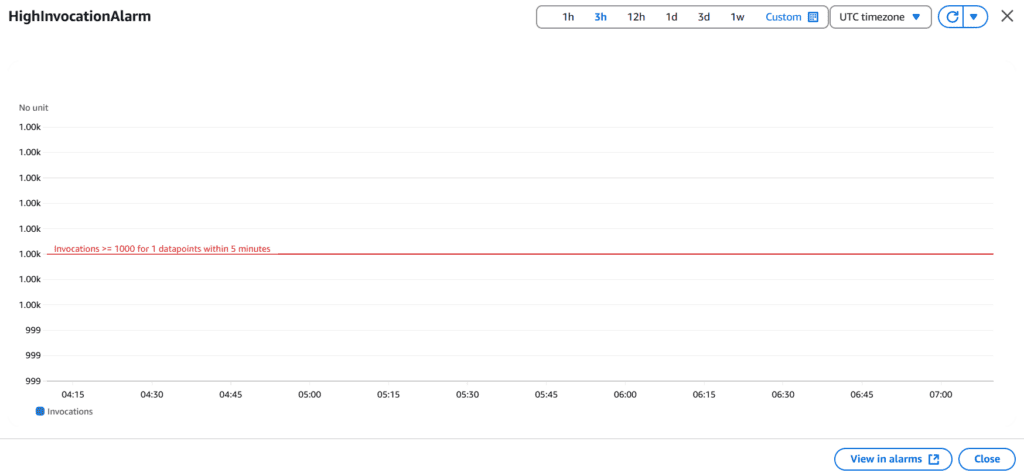
3. Enable Monitoring and Alerts:
- Go to CloudWatch:
- Create an Alarm for high invocation counts.
- Use this metric:
- Go to CloudWatch:
aws cloudwatch put-metric-alarm \
--alarm-name "HighInvocationAlarm" \
--metric-name Invocations \
--namespace AWS/Lambda \
--statistic Sum \
--period 300 \
--threshold 1000 \
--comparison-operator GreaterThanOrEqualToThreshold \
--dimensions Name=FunctionName,Value=my-function \
--evaluation-periods 1
4. Deploy WAF Rules (Optional):
- Create a WAF to block excessive IP requests.
Challenge Completion:
- Test by sending bulk requests using a tool like Apache JMeter or wrk and verify rate-limiting behavior.
Challenge 2: Prevent Event Injection
Objective: Ensure only valid events can trigger the function.
Setup Instructions:
- Deploy Lambda Function:
Use this basic example:
import jsonschema
schema = {
"type": "object",
"properties": {
"userId": {"type": "string"},
"action": {"type": "string"}
},
"required": ["userId", "action"]
}
def lambda_handler(event, context):
jsonschema.validate(instance=event, schema=schema)
return {"status": "success"}
2. Create Event Sources:
- For S3:
- Configure an S3 Event to trigger the function for PUT events.
- For S3:
Use this AWS CLI command:
aws s3api put-bucket-notification-configuration \
--bucket your-bucket-name \
--notification-configuration file://notification.json
3. Restrict Event Sources Using IAM Policies:
Example policy for an S3 trigger:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "lambda:InvokeFunction",
"Resource": "arn:aws:lambda:region:account-id:function:function-name",
"Condition": {
"ArnLike": {
"AWS:SourceArn": "arn:aws:s3:::your-bucket-name"
}
}
}
]
}
4. Test Validation:
- Create valid and invalid S3 events to observe Lambda’s response.
Challenge 3: Detect Privilege Escalation
Objective: Limit IAM role misuse.
Setup Instructions:
- Create IAM Roles for Lambda:
Use least privilege principles:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::secure-bucket/*"
]
}
]
}
2. Monitor Role Usage:
Enable CloudTrail to track API calls:
aws cloudtrail create-trail --name my-trail --s3-bucket-name log-bucket
aws cloudtrail start-logging --name my-trail
3. Set Alerts for Privilege Escalation:
- Use Amazon GuardDuty to detect suspicious activity.
4. Test Scenario:
- Attempt to access unauthorized resources using the Lambda function.
Conclusion
Although serverless computing makes infrastructure administration easier, it also presents new security risks. The necessity of strong defenses is highlighted by attack scenarios such as DoW, event injection, and privilege escalation. Organizations may create safe serverless environments and acquire important knowledge about practical attack and defense tactics by addressing these issues through demonstrations and practical labs.



































