Active Directory Red Team Specialist (AD-RTS)
- 100% Practical Active Directory (AD) Red Teaming
- Study Materials (Videos + Write-ups), 30 Days Challenge lab
- Break & learn Active Directory, Certificate Services, Exchange, Hypervisors (ESXi) security
- Course is for anyone who are interested in Red Teaming, Offensive Information Security
- For Red Team Enthusiasts: Turn Your Curiosity Into a Core Skill
The course content is divided across 6 sections listed below:
Active Directory Security
- Introduction
- Entra ID & On-Premise AD
- Core Components of AD
-
- Schema
- Global Catalog
- Database (NTDS.dit)
- Group Policy
- AD Objects
- Authentication & Authorization in AD
- Highly abused roles
Certificate Services Security
- Introduction
- Core Components
-
- Authority
- Templates
- Web Enrollment
- Certificate Revocation List
- Certificate Distribution Point
- Common Attacks & Mis-configuration
Abusing Exchange Server Roles
- Introduction
- Core Components
-
- Outlook Web Access
- Exchange Web Services
- MAPI & Autodiscover
- Targeted Exchange Admin Roles
- DEMO
-
- Persistence via Mailbox Delegation
- ApplicationImpersonate Role
- Import/Export Mailbox Role
- Backdoor Transport Rule
Attack Surface of ESXi integrated with AD
- Introduction
- Why ESXi are domain joined
- Attack Scenarios in AD integrated ESXi
- [DEMO] Administrator Role
AD-RTS Cyber Range Lab Part 1
- Case Studies
-
- Code Injection Attacks using publicly disclosed IIS machine Keys
- Exchange “ApplicationImpersonation” Role Abuse
- Command Execution to Guest VMs in ESXi Hypervisor
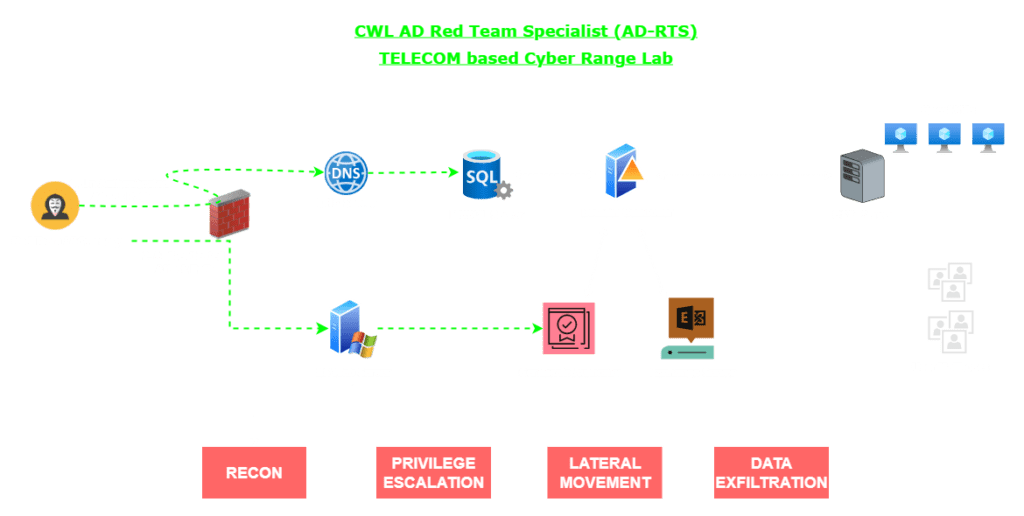
- Introduction to CyberWarFare Labs AD-RTS Cyber Range Lab
- Simulating Unauthenticated Adversary
-
- Initial Access: DNS Abuse, Anonymous Recon (LDAP), Kerberos PREAUTH & ACL abuse.
- Privilege Escalation: Compromise SQL Server → SYSTEM → Credential Dumping.
- Lateral Movement: Exploit ESC misconfigurations in Certificate Server → Impersonation → RCE on Domain Controller.
- Data Exfiltration: Discover/Execute commands on ESXi Host and Guest VMs.
AD-RTS Cyber Range Lab - Part 2
- Emulating Authenticated Adversary
-
- Initial Access: Exploit Internet-facing IIS Server (Pillaging keys, VIEWSTATE abuse) → Command Execution.
- Privilege Escalation: Decrypt DPAPI blobs → Certificate Impersonation → Domain Administrator.
- Lateral Movement:
- Domain Controller: Direct pivot.
- Exchange Server: Enumerate/Abuse "AppImpersonate" privileges → Access & pillage mailboxes.
- Data Exfiltration: Stealthy compression and exfiltration via encrypted channels.
- Hack into simulated TELECOM sector
- 2 unique attack approaches with Authenticated & UnAuthenticated Adversary
- Real world Adversary Simulations in following technologies/roles
-
- Active Directory
- Certificate Services
- Exchange Server
- Hypervisors (ESXi)
- IIS, DNS Roles Abuse
- Customized scripts with respective to labs are included for
-
- DNS Enumeration & Abuse
- Data exfiltration from Exchange Servers
- Command Execution in ESXi VMs
- Complete Red Team Operations from Recon / Initial Access to Impact (Data Exfil)
Pre-requisites
Following are the requirements:
- Basic Web & Network Penetration Testing Knowledge
- Familiarity with Command Line environment
- Setup Attacker VM (kali/parrot) to perform Red Team Operations
Target Audience
AD Red Team Practical course is designed for :
- Freshers / Intermediate level Penetration Testers
- Red Team Analysts or Penetration Testers / Offensive Cyber Analysts
- Anyone interested in upskilling in offensive information security knowledge
NOTE: The AD-RTS Challenge Lab is flag-based only, No report submission is required.
Premium Version
Active Directory Red Team Specialist (AD-RTS)
$49
Top features:
- 4+ hours of HD video content.
- Course Content (PDF) + 2 Attack Paths Write-ups
- Learn Practical AD Red Team Operations
- 30 Days Flag based Challenge Lab
- CWL Verified AD-RTS Certificate
Choose your journey and earn the CWL Verified AD-RTS Certification today
F.A.Q
Please check your Spam/Junk folder for an email from [email protected]. If not found, contact [email protected].
Login at https://labs.cyberwarfare.live using either:
- Google OAuth, or
- The Forgot Password option to generate a reset email.
All materials and labs are hosted on the CWL Cyber Security Playground (CCSP) at labs.cyberwarfare.live.
- 4+ Hours of HD videos
- Course PDFs + 2 attack path write‑ups
- 30 Days Flag-based Challenge Lab (no report submission required)
- Customized lab scripts and demos
- Email-based technical support
- CWL Verified AD-RTS Certificate
- Yes. Course materials (videos + PDFs) come with lifetime access. The challenge lab has 30 days access per activation (extendable upon request).
It’s self‑paced. On average, learners finish in 15–30 days, but there’s no deadline for course materials.
- Complete study materials (videos + PDFs).
- Activate the 30‑day challenge lab.
- Capture & submit all flags.
Once completed, you’ll receive a CWL verified AD-RTS Certificate.
No, certification is flag-based only.
Yes, email [email protected] with your purchase details.
Reach out via our Discord channel (shared after enrollment) or email [email protected].
Refunds are not provided unless cleared by our sales team. Please email [email protected] for eligibility.




































