Diving into the World of Adversary Simulation with Certified Red Team Analyst
The Red Team Analyst [CRTA] course is designed to train individuals who want to breakthrough in Offensive Information Security, empowering them to adopt the mindset of a malicious actor and think like a hacker. With simulating real-world cyber attacks through our well researched labs, through hands-on experience you will gain insights into the techniques and methodologies used by malicious adversaries to infiltrate and compromise systems in the real world.
About CRTA
The course is designed with well researched topics and in a way which includes many techniques used in Modern times by threat actors. Here is some glimpse of the content that will be covered by the Red Team Analyst (CRTA) Course.
Module 1 : Introduction to Red Teaming
In Module 1, we’re getting started with the basics of Red Teaming, where it is defined what Red Teaming is all about. Then, we’ll dive into the Red Team Attack Lifecycle, which breaks down the different stages of a cyber attack. Next, we’ll take a look at the infrastructure red teaming courses use, like the tools and systems they need to do their job. We’ll also check out the big picture of how companies are set up digitally, and finally, we’ll explore the different kinds of technologies that Red Teams exploit, from web and network stuff to cloud systems, physical setups, and even wireless networks.
Module 2 : Red Team Lab Setup
Here in this module first off we will set up a virtual environment where we can test out different scenarios demonstrated in the Red Team Analyst [CRTA] course.
Then we will understand how the lab works and get our virtual machines up and running. We will also install a couple of vulnerable machines here like Metasploitable, and a vulnerable employee machine, which is like a regular computer on a company network.
Next, we will get into the specifics of creating an Active Directory environment – basically, a network setup commonly used by organisations.
Module 3 : Red Teaming in External Environment
Now in Module 3, we are going to explore how Red Teaming works in an external environment. Basically, when we’re looking at attacking from outside a company’s network.
First, we will get an overview of what the external infrastructure looks like, then we will explore how we exploit services that are exposed to the outside world. This involves a few steps, like gathering information about the target, scanning and figuring out what services are there, assessing any vulnerabilities we find, and then exploiting them to gain access. We will also cover both web-based attacks, and network-based attacks.
Lastly, we will learn what to do Post-exploitation for data exfiltration, persistence and lateral movement.
Module 4 : Red Teaming in Internal Environment
In Module 4, we’ll be focusing on Red Teaming within the internal environment. First up, getting an overview of what the internal infrastructure looks like is kind of like understanding the layout of the inside of a network before we start exploitation.
Next, we will get into infrastructure enumeration, where we will be figuring out what’s inside the network. This includes things like mapping out the internal network and understanding the setup of the Active Directory environment.
Then, comes the fun part – exploiting the Active Directory environment. We will break down the different phases of this process, from gaining initial access to escalating privileges and moving laterally within the network. It’s all about understanding how attackers move once they’re inside a network
Module 5 : Case Study
In this module, we’re going to cover a few key topics to tie everything together.
Here we will take a closer look at the lab architecture, giving a better understanding of how everything is set up.
After that, we will learn about mapping the lab with the MITRE ATT&CK Framework. This helps us to categorise different types of attacks and understand how they fit into the executive understanding of cybersecurity.
Next, we will explore both external and internal Red Teaming exercises – basically, putting everything we’ve learned into practice by simulating attacks from both outside and inside the network.
We will also explore utilisation of LOLBAS (Living Off The Land Binaries and Scripts) for stealth persistence and data exfiltration.
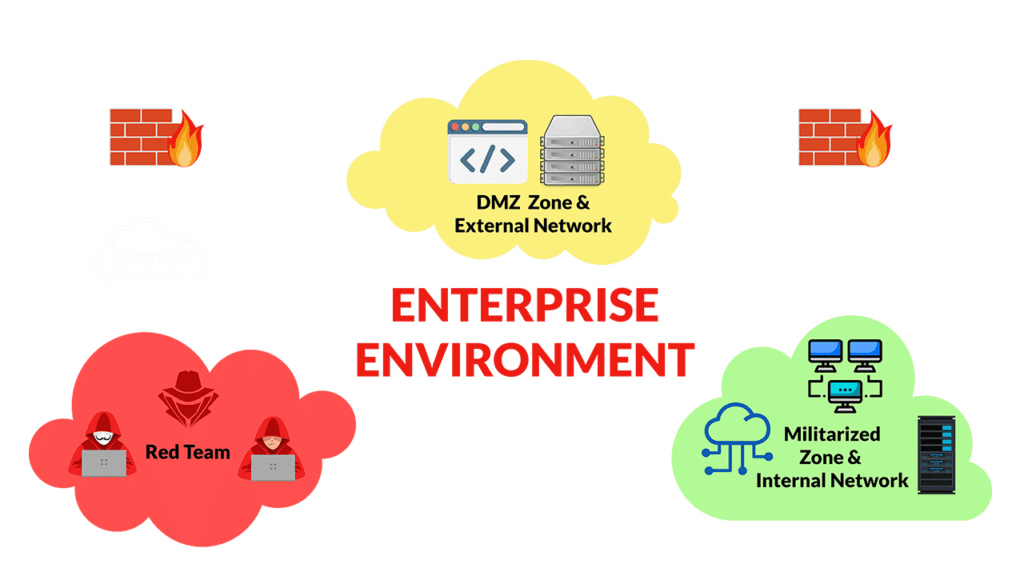
The practice lab includes multiple segregated networks with Linux and Windows workstations. It allows for hands-on offensive operations in both external and internal environments, enabling us to abuse web and network attacks and manually perform pivoting/lateral movement.
Experience under Red Team Analyst (CRTA) Practice Labs
Connecting to the practical cyber security labs requires a VPN connection. The lab was set up in a delineate way which allows us to explore a mimic of real life systems which has both External as well as internal networks.
The practice lab helped me explore different domains of attack in Red teaming like Web Application Attacks, Reverse Shells, Post exploitation reconnaissance, Lateral Movement, Privilege Escalation, Active Directory Enumeration as well as attack vectors.
Additionally, the lab also had scenarios requiring Kerberos-based attacks like Golden ticket that facilitates the complete Red Team cycle in an enterprise environment.
Please find the testimonials for the CRTA Course: CRTA Testimonials




































