Uncovering APT Strategies for Cloud Initial Access

OVERVIEW
As enterprises increasingly adopt hybrid or multi-cloud environments, adversaries have begun targeting these infrastructures using a variety of sophisticated techniques. In this context, it’s essential to uncover the most commonly used strategies employed by APTs for cloud initial access, along with effective detection approaches to counter these threats.
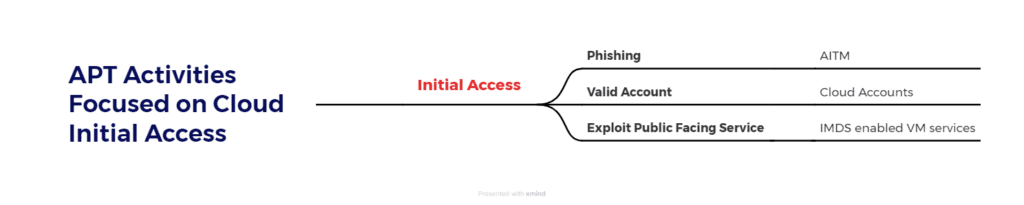
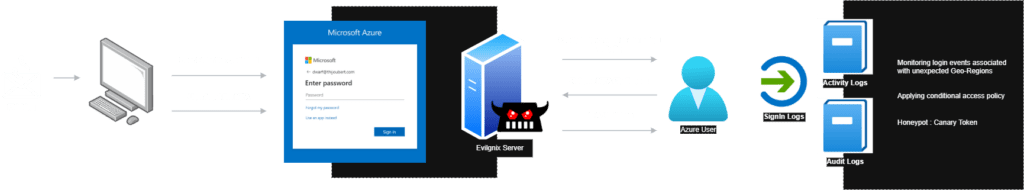
Phishing AITM
Unlike traditional phishing attacks, adversaries now leverage Adversary-in-the-Middle (AITM) techniques to bypass Multi-Factor Authentication (MFA) and gain unauthorized access to cloud infrastructure. Detecting and identifying AITM attacks can be particularly challenging.
Rather than relying on static phishing pages, attackers have adopted proxy phishing servers or techniques like server-less phishing. Once they obtain a valid session token, they can bypass MFA protections and authenticate as legitimate users, effectively nullifying MFA security measures.
One of the most effective ways to detect AITM attacks is by monitoring geo-location-based anomalies. By correlating IP addresses with unusual login locations, security teams can establish detection rules to flag suspicious login attempts from unauthorized or unexpected geographic regions.
FROM filebeat*
| WHERE event.action == "Sign-in activity" and event.outcome == "success"
| WHERE NOT CIDR_MATCH(source.ip,"<IP Subnet>/24")
| WHERE NOT source.geo.country_name IN ("India", "USA", "UK")
| KEEP user.name, @timestamp, event.action , source.ip, source.geo.country_name, event.outcome
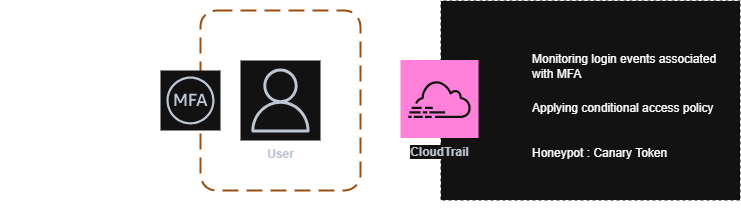
Valid Accounts
Identifying and detecting activities associated with Valid Account abuse can be highly challenging. In some cases, the activity may indicate an ongoing attack, while in others, it could be legitimate. Distinguishing between malicious and legitimate behavior requires advanced correlation techniques and User Behavior Analytics (UBA) to accurately determine potential threats.
Here are some key recommendations to help detect Valid Account compromise:
- Monitoring Unusual Login Patterns
- Detecting Multi-Factor Authentication (MFA) Bypass Attempts
- Tracking Privilege Escalation Activities
Monitoring Unusual Login Patterns
Monitoring unusual login patterns is crucial for identifying suspicious Valid Account activity. By prioritizing events such as multiple failed login attempts and password spraying attacks, security teams can effectively detect potential threats related to account compromise.
The following query helps in identifying password spraying attacks, focusing on login attempts initiated via Python requests, which can be an indicator of automated attacks. Prioritizing such events allows for better detection and response to malicious Valid Account activity.
event.dataset : "azure.signinlogs" and event.outcome : "success" and user_agent.name: "Python Requests"
Multi-Factor Authentication (MFA) Bypass Detection
Monitoring and investigating MFA failure events can help identify suspicious activities and assist in root cause analysis. While MFA bypass attempts are complex and have a low success rate, tracking failed attempts provides valuable insights into attack patterns and techniques used by adversaries.
The following query helps prioritize events related to failed MFA attempts within a 30-minute timeframe, allowing for better detection and analysis of potential threats.
FROM filebeat-*
| WHERE event.action == "ConsoleLogin" and event.outcome == "failure"
| EVAL sample = ENDS_WITH(aws.cloudtrail.additional_eventdata, "MFAUsed=Yes")
| KEEP user.name , @timestamp, source.ip
| STATS COUNT_DISTINCT(@timestamp) BY DATE_TRUNC(30 minutes, @timestamp), user.name, source.ip
Monitoring Privilege Escalation Attempts [Assume Role : CreateAccessKey]
Investigating privilege escalation activities, particularly around role assumption and access key credential creation, is crucial for prioritizing events that are commonly targeted by adversaries to escalate privileges through the abuse of valid accounts.
Attackers often exploit legitimate cloud functionalities to gain elevated privileges. In cloud environments, this is typically seen when a user in one AWS account assumes a role in another account to gain unauthorized access to its resources, potentially leading to privilege escalation.
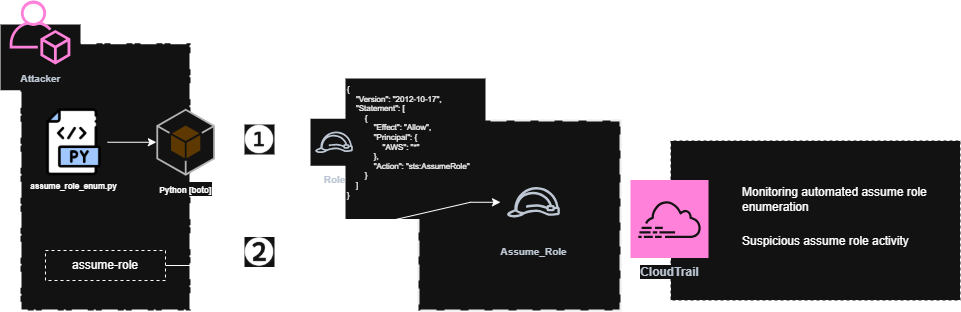
To assume a role, attackers often enumerate and identify roles with the sts:AssumeRole permission. By executing the query below, we can prioritize enumeration events specifically targeted by automated tools for the AssumeRole activity.
event.dataset: "aws.cloudtrail" and aws.cloudtrail.error_code : "AccessDenied" and user_agent.name : "Boto3" and event.action: "AssumeRole"
Another critical step is prioritizing events related to access key credential creation. If a user account with elevated privileges creates an access key, it becomes a commonly abused technique by adversaries using valid accounts. This behavior is often exploited to maintain unauthorized access to cloud resources, making it essential to monitor and flag such events.
FROM filebeat-*
| WHERE event.action IN ("CreatePolicyVersion", "CreateAccessKey", "UpdateLoginProfile") and user.name != "ELK" and event.outcome == "success"
| WHERE CIDR_MATCH(source.ip,"<IP Subnet>/24")
| KEEP user.name, @timestamp, event.action, user.target.name
Exploit Public Facing Application
IMDS enabled VM services
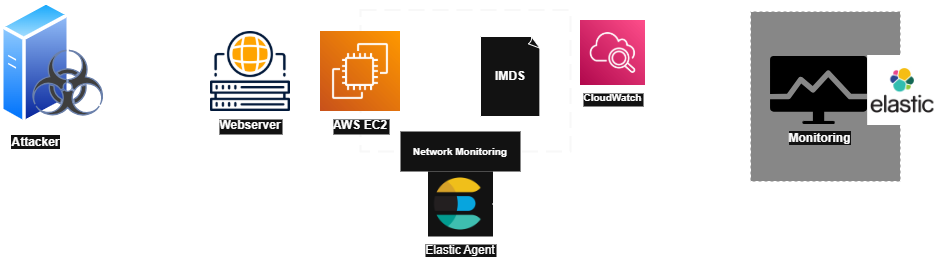
A significant security concern for VM instances is the Instance Metadata Service (IMDS). IMDS provides metadata and user data to VM instances, such as instance ID, IP addresses, region, and more, without requiring credentials or permission checks. This service is accessible via HTTP requests from within the instance.
In a scenario where a web application hosted on an EC2 instance is vulnerable to Server-Side Request Forgery (SSRF) or command execution, an attacker could exploit the vulnerability to craft HTTP requests on their behalf. In an AWS environment, the IMDS (accessible at http://169.254.169.254/latest/meta-data/) contains sensitive, instance-specific information, including IAM role credentials. By exploiting the SSRF vulnerability, an attacker could manipulate the application into querying the Metadata Service, exposing this sensitive data and potentially gaining unauthorized access to AWS resources.
Identifying and investigating VM-targeted metadata can be challenging, as it involves correlating network monitoring directly on the VM instance.
By correlating network traffic, we can prioritize activities associated with metadata retrieval, helping to identify and flag potentially malicious actions targeting the VM’s metadata.
data_stream.dataset: network_traffic.http and server.ip : 169.254.169.254 and http.request.method: "GET" and url.path : /latest/meta-data/*
The following URI paths are commonly observed in suspicious Metadata requests:
- /latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance
- /latest/meta-data/ami-id
- /latest/meta-data/hostname
- /latest/meta-data/public-ipv4
As APT threats evolve in cloud environments, mastering multi-cloud defense is essential. The Multi-Cloud Blue Team Analyst (MCBTA) course by Cyberwarfare Labs offers hands-on training in securing AWS, Azure, and GCP, with real-world investigations and gamified challenges. Take advantage of the CWL Anniversary Sale 2025 to enroll at a huge discount : Click here to checkout



































