The Fine Line: Walking the Nmap Tightrope as a Purple Teamer

INTRODUCTION
Nmap a.k.a Network mapper is one of the prominent tools used in scanning networks. In addition to scanning capabilities, it also has functionalities for running scripts written in Lua language through a custom implementation known as Nmap Scripting Engine (NSE).
For the purpose of this blog, we’ll be pairing Nmap with Capinfos, tcpdump, and TShark. Our goal is to run couple Nmap scans and then use CLI based tools to detect these scans.
ATTACK & DETECTION
Capturing Packets
To capture the packets, we can use either tcpdump or TShark. Below is an example using tcpdump. Please note that throughout the blog, we’ll be using the same command to capture the packets while only changing the file names according to the scan type used.
sudo tcpdump -i lo -nn -s0 -v -Al -w nmap-all-ports.pcap –print
Let’s decode the flags used in above command:
-i is for the interface from which to capture packets
-nn is for disabling hostname & port resolution
-s0 is for capturing the entire packet content as by default it only captures limited bytes
-v is for verbosity
-Al is to print buffered output in ASCII format (in terminal)
-w is for writing capture to file
–print is for printing the output to the terminal
Running Nmap
We’ll be running a very simple scan of Nmap & without enabling any defence evasion methods. Additionally, since this is a demo scenario, we’ll be scanning the localhost only.
nmap 127.0.0.1 -sC -sT
Let’s decode the flags used:
-sC runs the default NSE scripts
-sT runs the full TCP scan
Which will give us the following output.
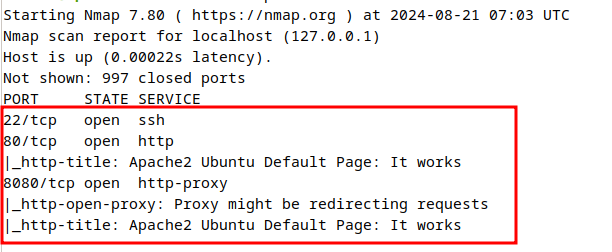
From this output, 3 services are running (out of top 1000 ports) including SSH, Apache2, and a proxy server along with some of the details like running services & page titles.
Reading PCAP metadata
Now that we have captured the Packets, the next step would be to view the metadata and view some attributes related to the captured traffic.
We’ll be using Capinfos for this purpose.
capinfos nmap-all-ports.pcap
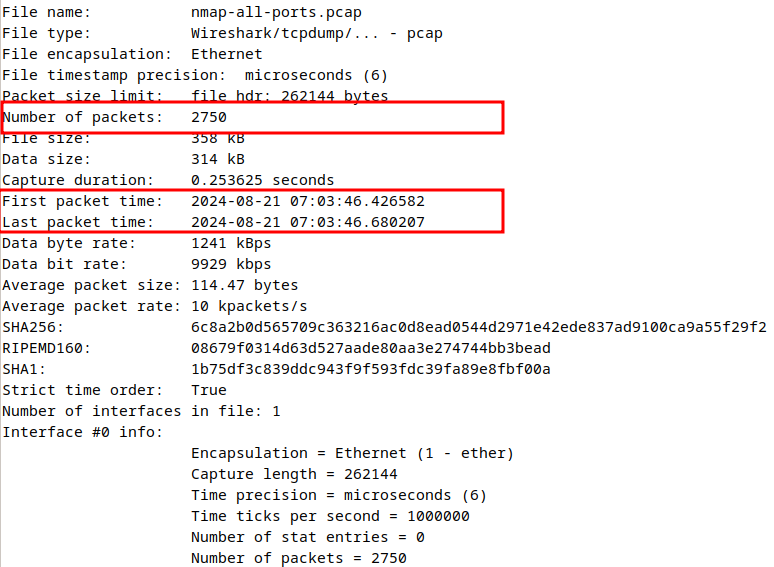
Now if we look into the Capinfos output, we can see some of the attributes like the total number of packets & the packet flow timing (first & last packets).
Detecting User Agent (UA) Header
By default, Nmap sends a pre-configured UA header with NSE requests. This is set to Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html) unless configured otherwise.
For detecting the default UA of NSE, we’ll use TShark as follows:
tshark -r nmap-all-ports.pcap -Y http.request -Tfields -e http.user_agent
Before looking into the output, let’s take a moment to decode the flags we used.
-r is for reading from a capture file
-Y is used for display filter (in our case, we’re filtering HTTP packets)
-Tfields is to extract fields
-e is to specify which fields to extract
Now if all went good, we’ll see output similar to below image with the NSE UA
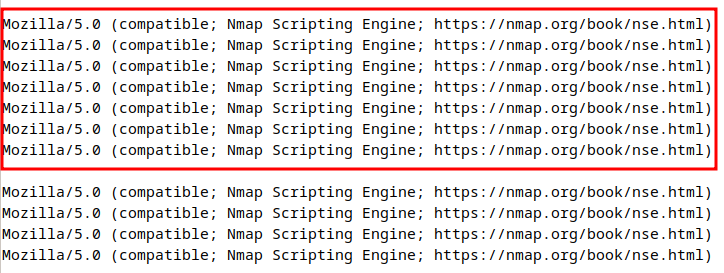
Detecting Stealth Scan
Now one of the defence evasion features included in Nmap is the SYN scan (Stealth Scan/half-open scan) which runs by default if Nmap is executed with admin privileges. Here Nmap initiates the TCP 3-way handshake and drops the connection once it receives the SYN/ACK back from the server. SInce the handshake is never completed this scan can sometimes fly through the radar (although can be detected easily by well configured network defences).
We can run the SYN scan using the following command:-
sudo nmap -sS 127.0.0.1
Now since we know the logic behind the SYN scan, we can filter the traffic where the 3-way handshake was not completed. We’ll use the following command to filter the packets where the aforementioned condition occurred.
tshark -r nmap-stealth-scan.pcap -Y "tcp.flags.syn==1 and tcp.flags.ack==0 and tcp.window_size<=1024"
Let’s decode the flags used:
tcp.flags.syn==1 and tcp.flags.ack==0 to filter packets where SYN flag is set without an accompanying ACK flag
tcp.window_size<=1024 to filter packets with size less than 1024 bytes
Please note that since we’re using the and operator in the above command, the displayed output will be of packets where all three conditions are true.
The above command will give an output similar as shown below.
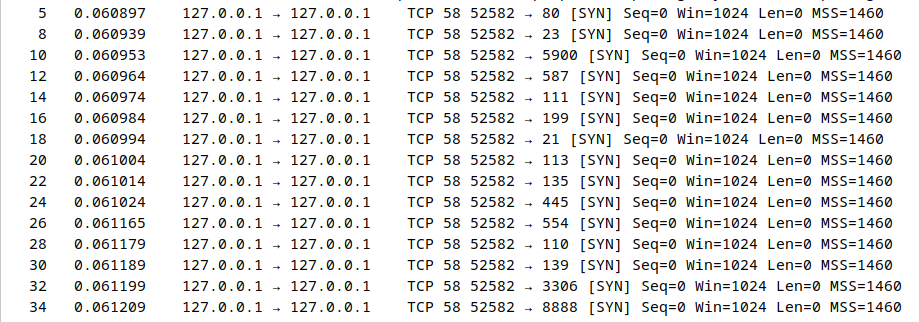
Here we can see that a lot of handshake attempts were made but not completed. If we look into the first field, there is 1 packet gap between the entries indicating that the server sent the SYN/ACK and then the next port scan activity took place.
Ending Note
While we explored couple Nmap scans, there are many more out there employing different tactics. Below are some of the commands for detecting few of those and some materials for light reading. In case you wanna try these out yourselves, just setup the packet capture and run Nmap scans and analyse the packets using below commands.
1. TCP FIN scan:
- Attack:
sudo nmap -sF 127.0.0.1
- Detection:
tshark -r nmap-fin-scan.pcap -Y "tcp.flags==0x001"
2. TCP Null scan:
- Attack:
nmap -sN 127.0.0.1
- Detection:
tshark -r nmap-null-scan -Y "tcp.flags==0"
3. TCP Xmass scan:
- Attack:
nmap -sX 127.0.0.1
- Detection:
tshark -r nmap-xmas-scan.pcap -Y "tcp.flags.fin==1 && tcp.flags.push==1 && tcp.flags.urg==1"
4. UDP port scan:
- Attack:
nmap -sU 127.0.0.1
- Detection:
tshark -r nmap-udp-scan.pcap -Y "icmp.type==3 and icmp.code==3"



































