The Anatomy of QR Code Phishing: A Tactic So Powerful, it's Like a Sith Lord in Your Pocket

INTRODUCTION TO QR CODES
In today’s fast-paced digital age, QR (Quick Response) codes have emerged as a powerful tool for businesses and organizations to facilitate services with their customers and stakeholders. Introduced in 1994 by Denso Wave, these QR codes are a two-dimensional barcode which can store a vast amount of information (up-to 7,089 numerals), including text, URLs, and other data. They can be read quickly and easily by smartphones and other mobile devices, making them an ideal solution for a wide range of use cases including fast payments, file transfer, information sharing, marketing, or user authentication (for e.g, Web login feature of WhatsApp or Telegram).
ALONG CAME QUISHING (QR BASED PHISHING)
As a red team analyst, our goal is to simulate real-world attack scenarios to test the security posture of our clients. Given that the QR codes are used almost everywhere and often ignored as a potential security risk, leveraging them to gain initial access or pivot to the client’s mobile device(s) is a very interesting attack vector. This technique commonly known as Quishing involves creating an image file (QR code) that redirects users to a red team controlled resource (payload server/website) and then gaining access to their mobile device(s). One thing that makes Quishing powerful is that the delivery can be done via a number of approaches like emails, messages, or even flyers in the client’s premises.
That being said, given the lucrative advantages Quishing gives over the other phishing techniques, real world threat actors have also been leveraging it for their campaigns. Tracked under ID T1660 of MITRE ATT&CK, this technique has been exploited greatly by threat actors due to the widespread usage of the QR codes in the daily life of an average individual.
SCENARIOS
Now that we’ve talked about the theory behind quishing, let’s see it in action. In this demonstration, we’ll look into three types of Quishing attacks which could be used to gain access to a user’s mobile device(s)/online account.
URL BASED ATTACKS
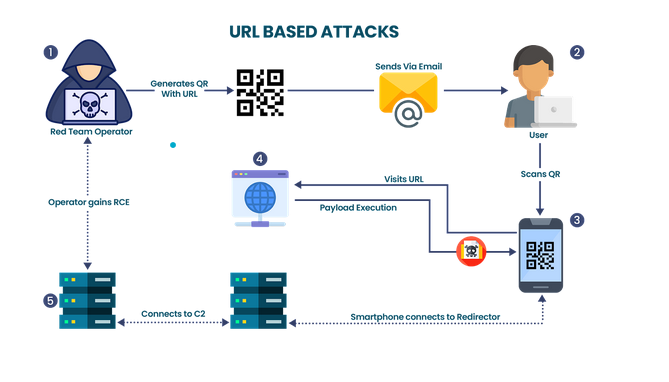
- Step 1: After performing the initial recon, the red team operator identifies the usage of BYOD (Bring Your Own Device) devices and crafts a QR code pointing to the payload website. the red team operator then includes this QR code into an email and sends it to the user.
- Step 2: The User opens the email on their Laptop and reads it.
- Step 3: The User then utilizes their Smartphone to scan the QR code and visits the payload website.
- Step 4: Payload website executes the payload upon visit and infects the user’s smartphone.
- Step 5: Smartphone then connects to the Redirector which in turn forwards the traffic to the C2 server. Red team operator has now access to the user’s device.
PAYLOAD BASED ATTACKS
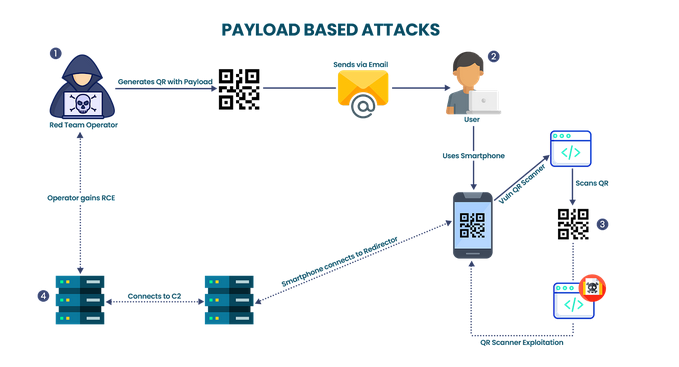
- Step 1: The red team operator learns that the client’s organization uses a particular application for QR code scanning. Upon reverse engineering the said application, a critical vulnerability was identified. The attacker then creates a QR code with the shellcode as data and sends it to the user.
- Step 2: User opens the email on the Laptop, and after seeing the attached QR code uses the said application on their smartphone to scan it.
- Step 3: Once the QR code is scanned by the application and shellcode is interpreted, the vulnerability is exploited.
- Step 4: Smartphone now connects to the Redirector server which forwards the traffic to the C2 server. Now the red team operator has RCE access to the user’s smartphone.
AiTM (ADVERSARY IN THE MIDDLE)
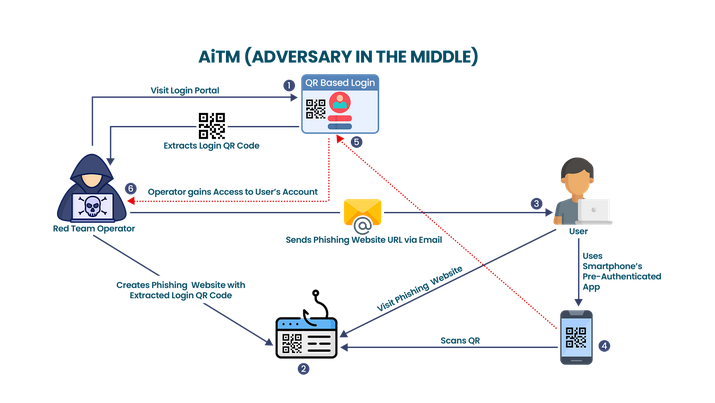
- Step 1: In this case, the red team operator learns that the client’s organization uses a specific employee portal which also accepts QR codes as authentication protocol. This is however done only if the session is logged in on the user’s smartphone. The red team operator extracts the QR code from the login portal and starts preparing for the further process.
- Step 2: The red team operator creates a phishing website mimicking the real portal
- Step 3: The phishing website’s link is then sent to the user via email.
- Step 4: The user falls for the phish and uses their authenticated mobile application to scan the QR code and approves the authentication request of the operator’s session with the real login portal.
- Step 5: The authentication request is passed to the real login portal which grants access to the red team operator.
- Step 6: Red team operator now has full access to the user’s account.
ENDING NOTE
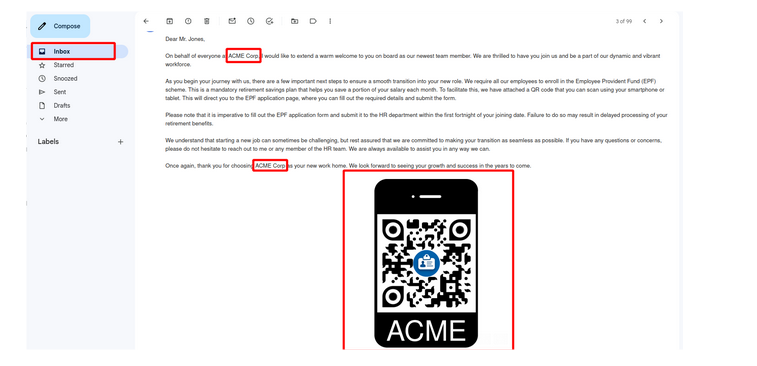
Given below is a very obvious phishing email which we managed to land in the Inbox of a very large email services provider twice with a recently registered domain. This demonstrates the efficiency of Quishing as a powerful weapon in the arsenal of a red teamer/pentester. That being said, it should be noted that email scanning services can pick up on this type of attacks if proper OpSec is not followed while designing the phish. In our case, the payload was hidden behind a redirector with limited access to only a selected pool of IPs. Additionally, the QR codes were embedded in the email body instead of as an attachment.