Proactive approach for Securing S3 Buckets

OVERVIEW
Among all AWS services, S3 is the most targeted by attacks due to its availability and accessibility. This makes it challenging for organizations to implement and deploy various security measures for the S3 service. Traditional detection get failed over these evolved attacks scenarios.
In this blog, we will discuss proactive approaches for detecting and securing Amazon S3 services in detail. Securing S3 buckets requires a comprehensive strategy for monitoring and detection. By adopting various security measures such as regular audits, enabling robust logging and monitoring, implementing encryption, utilizing IAM roles and policies, automating responses, enabling multi-factor authentication (MFA), conducting security drills, establishing a communication plan, and continuously improving your processes, you can significantly enhance the security of your S3 buckets and protect your valuable data from cyber warfare.
List of service which get often used to protect S3 targeted attacks
AWS generally offers various security services by default to monitor and prevent cyber threats. Alternatively, organizations can opt for traditional monitoring methods by collecting logs from various services and investigating them using a centralized SIEM. Below is a list of commonly used services for monitoring and identifying cyber threats targeting S3 buckets.
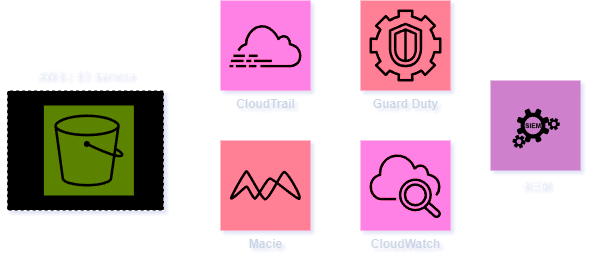
CloudTrail: It generally records API calls and events made by or on behalf of your AWS account, capturing vital information related to S3 bucket access and activity. This includes details on Bucket Access, Bucket Policy Changes, and Data Events.
Macie: It is specifically tailored to secure data stored in Amazon S3 buckets, leveraging machine learning algorithms to identify anomalous behavior. Furthermore, it continuously monitors data access and usage within S3 buckets, ensuring ongoing visibility into security risks and compliance status.
Guard Duty: Guard Duties S3 Protection feature detects anomalies in access patterns and behavior within S3 buckets. It also offers a centralized dashboard and console for managing and viewing security findings.
CloudWatch: Typically, a monitoring service is utilized to gather and retain access logs containing details such as the IP address of the requester, the type of request made, and the response status. These accumulated logs are then employed for diverse analyses and investigative tasks.
SIEM: A conventional approach to central monitoring services is both cost-effective and efficient, as it allows integration with various logs, including CloudTrail, CloudWatch, etc.
Misconfigured Access Controls
Misconfiguration on S3 bucket often leads to various security risks including compromising or exposing sensitive information or exfiltrating sensitive information from the S3 bucket.
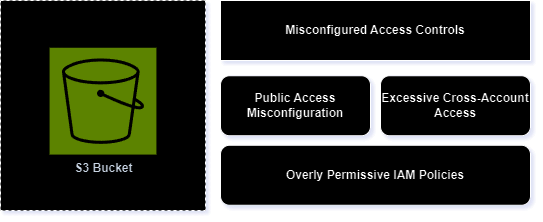
We will delve into commonly observed misconfigurations, such as Public access misconfiguration, Overly Permissive IAM Policy, and Excessive Cross-Account Access. In this discussion, we’ll outline their attack execution flow and proactive approaches to identifying and detecting them.
Public access misconfiguration
According to the statistics, out of the 100,000 buckets discovered, 14 percent were publicly accessible. Publicly accessible buckets can result in enumeration, data exfiltration, or even encryption of sensitive data followed by ransom demands.
Attackers commonly engage in enumeration techniques to identify and assess sensitive and confidential information.
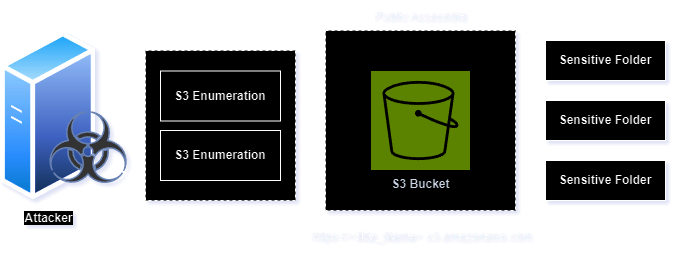
Identifying and detecting
To detect and secure such activities, it’s advisable to deploy security measures like enabling and configuring AWS Macie, Enabling S3 Protection on GuardDuty, or activating access logging for publicly hosted S3 buckets and forwarding those logs to a SIEM service for in-depth analysis and investigation.
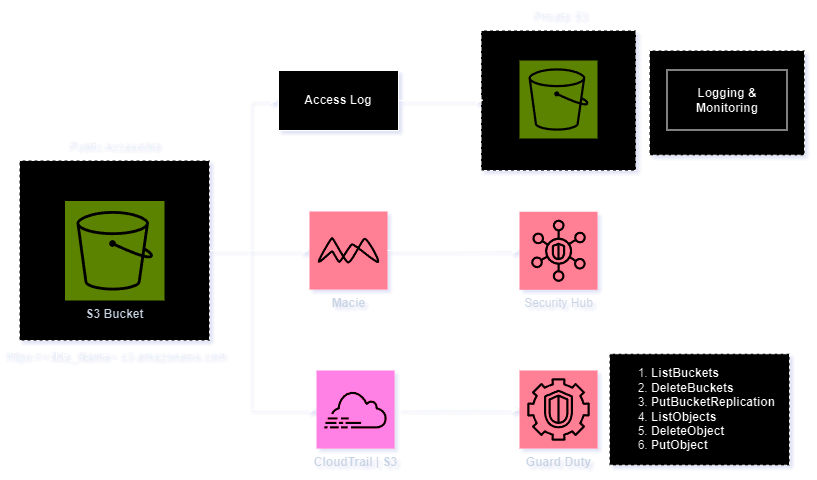
Overly Permissive IAM Policies
The majority of cloud compromises are targeted and exploited through overly permissive IAM policies assigned to users or services. Attackers constantly search for excessively privileged accounts to carry out various malicious activities, such as deleting sensitive buckets, uploading malware and malicious binaries used as delivery mediums, and exfiltrating sensitive information.
Most attacks exploiting overly permissive IAM policies appear to be initiated by insider threats or occur when user credentials are compromised or exposed. In such cases, attackers log in using the stolen credentials to perform various malicious operations.
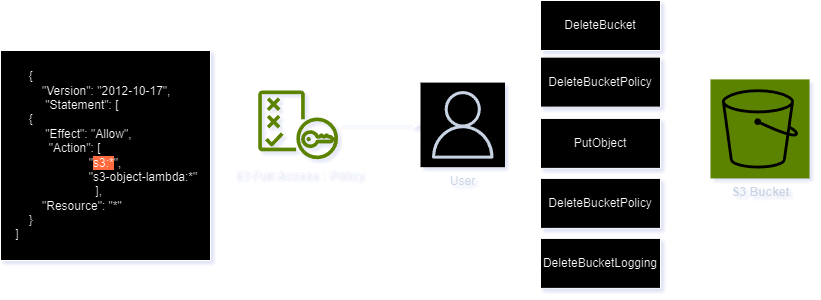
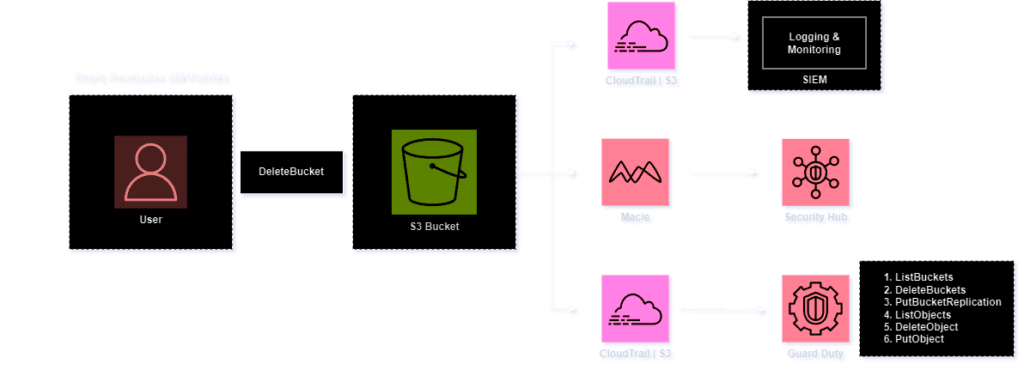
Identifying and detecting
To detect and secure overly permissive IAM policies, it is crucial to enable monitoring through CloudTrail logs. It is advisable to deploy security measures such as configuring AWS Macie, enabling S3 protection on GuardDuty, and activating CloudTrail logging for hosted S3 buckets. Forward these logs to a SIEM service for in-depth analysis and investigation.
Excessive Cross-Account Access
Many small and mid-sized companies often outsource a majority of tasks to external companies to perform various business operations. In these situations, it is mandatory to assign specific privileges to carry out these activities. Organizations typically allocate a dedicated account to the client for these tasks. However, if access is not restricted to specific actions or objects, this approach poses a high risk of potential data misuse.
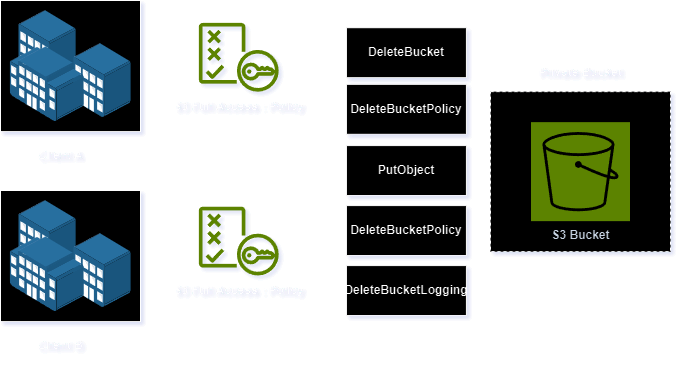
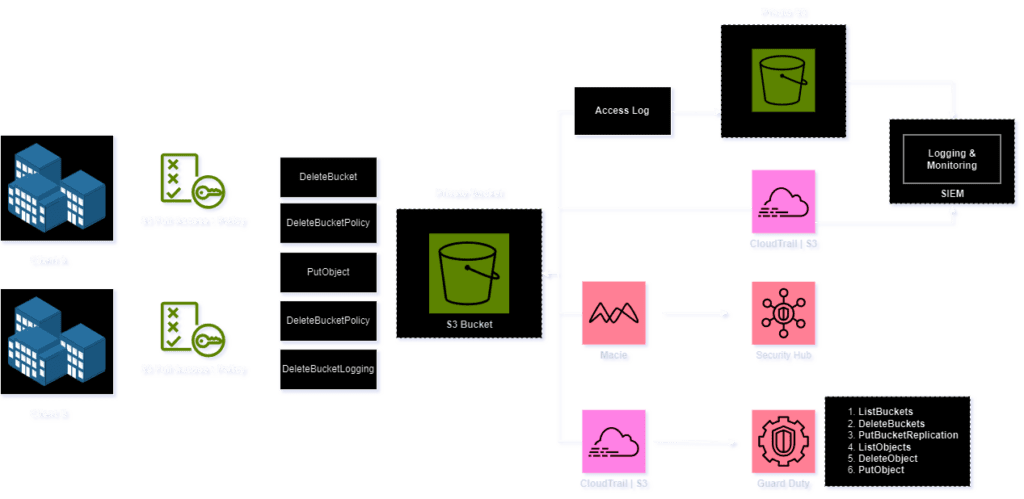
Identifying and detecting
Detecting and securing excessive cross-account access requires a higher level of monitoring compared to other attacks, as the access provided is intentionally assigned to the clients and cannot be easily revoked. Balancing business operations and security is crucial. Effective monitoring can be achieved through CloudTrail logs. It is advisable to deploy security measures such as configuring AWS Macie, enabling S3 protection on GuardDuty, and activating CloudTrail logging for hosted S3 buckets and access logs. Forward these logs to a SIEM service for in-depth analysis and investigation.
 USA Independence Day Sale is LIVE; Get Flat 90% OFF on CRTA, Use Code: “USA90"
USA Independence Day Sale is LIVE; Get Flat 90% OFF on CRTA, Use Code: “USA90"
































