Enumerating AWS IAM Identity Center

Identity Center

AWS IAM Identity Center (formerly known as AWS Single Sign-On) is a cloud service that enables organisations to manage access to AWS accounts and applications securely. It is the solution for linking your workforce users to AWS-managed applications like Amazon Q Developer and Amazon QuickSight, as well as other AWS resources. You can integrate your current identity provider to synchronise users and groups from your directory, or you can create and manage users directly within IAM Identity Center.
It can be used for:
- User access to applications
- User access to AWS accounts
Key Features:
- Centralised User Management: IAM Identity Center allows you to create and manage user identities directly within the service or integrate it with your existing identity provider (IdP) to synchronise users and groups from your directory.
- Single Sign-On (SSO): Users can access multiple AWS accounts and business applications using a single set of credentials, simplifying the login process.
- Access Control: It provides fine-grained access control, allowing you to define permissions based on roles, groups, or attributes, ensuring users have the appropriate level of access to resources.
- Integration with AWS Services: IAM Identity Center integrates seamlessly with various AWS services, such as Amazon QuickSight, Amazon Q, and others, making it easier to manage user access across your AWS environment.
- Multi-Factor Authentication (MFA): It supports MFA, enhancing the security of user accounts by requiring an additional verification step during login.
- Audit and Compliance: AWS IAM Identity Center offers logging and monitoring capabilities, enabling organisations to track user access and meet compliance requirements.
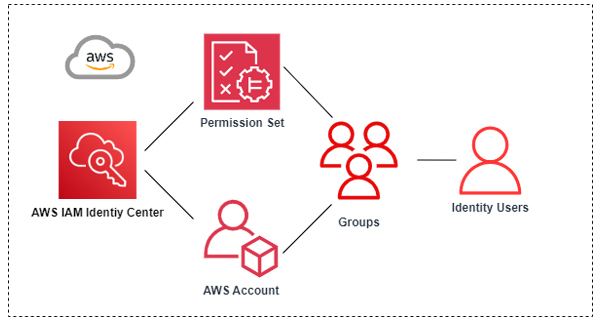
Gathering and enumerating information related to AWS Identity Center can provide attackers with valuable insights into an organisation’s Single Sign-On (SSO) configuration. AWS Identity Center acts as a centralised service that simplifies SSO across various AWS accounts, cloud applications, and on-premises systems, allowing users to log in once and access multiple resources with a single identity. By identifying and mapping out identities, roles, and configurations within AWS Identity Center, attackers could exploit this information to craft targeted phishing campaigns or other methods to compromise credentials, potentially gaining unauthorised access to critical systems.
Listed below are some permissions that attackers can use to enumerate additional information:
sso:List* | identitystore:List* |
sso:Describe* | identitystore:Describe* |
By utilizing these privileges, attackers can collect a thorough range of information related to AWS Identity Center, assisting them in strategizing subsequent actions like privilege escalation or lateral movement within the compromised environment. This information could allow attackers to take advantage of vulnerabilities, elevate their access levels, and navigate throughout the infrastructure, thereby intensifying the impact of the breach.
Enumeration Mind Map
The image below provides better visibility and understanding of how enumeration typically occurs when targeting a Identity Center
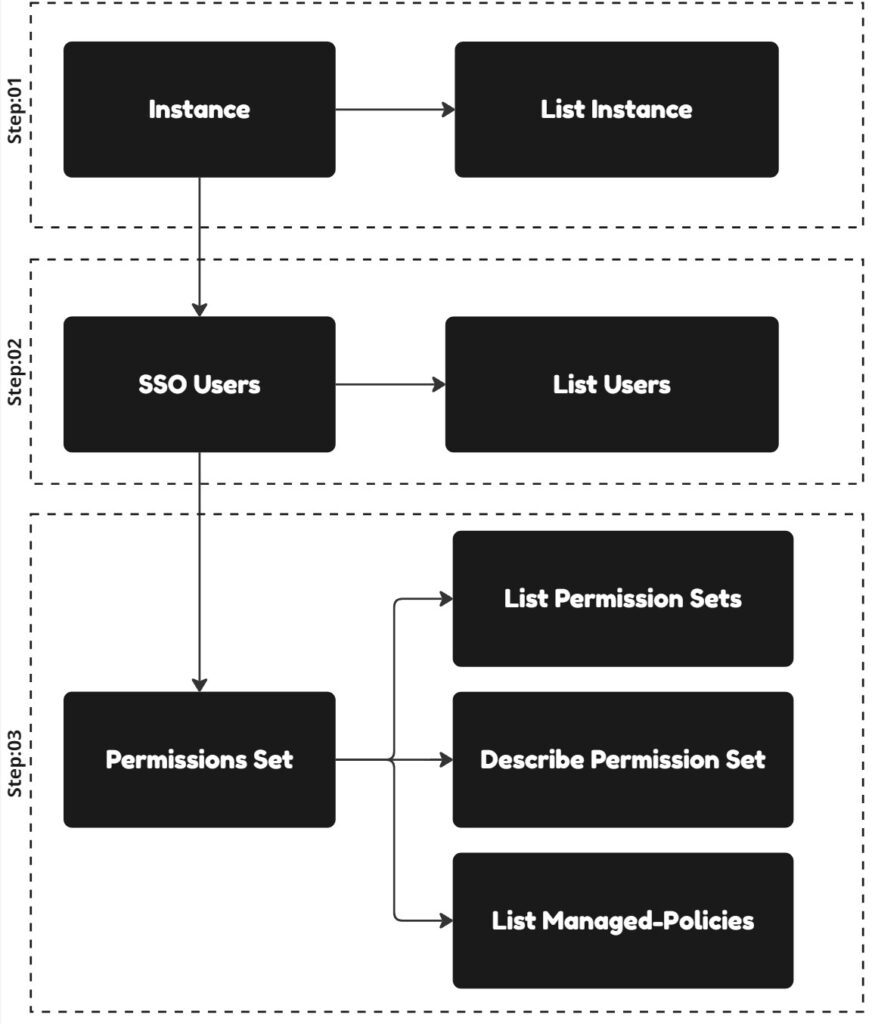
The enumeration process starts by listing instances associated with AWS Identity Center. Once the identity is enumerated, it reveals the identity-store-id. Using this, further enumeration can target SSO users linked to the identity store, including details such as user email addresses involved in identity management. With these results, attackers can focus on the email addresses to execute various attacks aimed at gaining access. Ultimately, the gathered information can include details about permission sets, along with inline and attached policies, providing insight into the permissions associated with users or roles for further exploitation.
Below listed are the list of enumeration command associated with an investigative queries,
Identity Center Enumeration
Listing the instance associated with AWS Identity Center
aws sso-admin list-instances --region us-east-1 --profile emp01
This command is used to list all AWS IAM Identity Center (formerly AWS Single Sign-On) instances in the specified AWS region.
Enumerating users associated with AWS Identity Center
aws identitystore list-users --identity-store-id <store-id> --region us-east-1
This command is used to list all users within a specified identity store in AWS Identity Store.
Enumeration Permission Sets
aws sso-admin list-permission-sets --instance-arn <Arn>
This command is used to list all permission sets associated with a specified AWS IAM Identity Center (formerly AWS Single Sign-On) instance.
Describing Permission Sets
aws sso-admin describe-permission-set --instance-arn <INS_ARN> --permission-set-arn <PER_ARN>
This command is used to retrieve detailed information about a specific permission set in AWS IAM Identity Center (formerly AWS Single Sign-On).
List Accounts for a Permission Set:
.
aws sso-admin list-accounts-for-provisioned-permission-set --instance-arn <instance-arn> --permission-set-arn <permission-set-arn>
This command is used to list all AWS accounts that have the specified permission set provisioned.
Enumeration Managed Policies with AWS Identity Center
aws sso-admin list-managed-policies-in-permission-set --instance-arn <instance-arn> --permission-set-arn <perm-set-arn>
This command is used to list all managed policies associated with a specific permission set in AWS IAM Identity Center (formerly AWS Single Sign-On).
The techniques outlined above are typical enumeration methods that attackers might employ. Although the commands themselves are legitimate, they can be misused by attackers to collect detailed information about cloud infrastructure. By closely monitoring high volumes of listing and retrieval activities and identifying suspicious or malicious IP addresses linked to these queries, investigations can become more precise and effective. Instead of tracking every listing and retrieval activity, concentrating on specific criteria will enhance correlation and improve overall security monitoring.
- Prioritise activities where an external or malicious IP is performing multiple LIST and GET operations.
- Additionally, monitor unusual AWS user accounts engaging in LIST and GET operations.
- Tracking the User-Agent in these requests can also significantly aid in correlation and detection of suspicious behaviour.



































