Cloud Sleuthing: Decoding AWS Infrastructure

OVERVIEW
AWS a.k.a Amazon Web Services is one of the oldest and most widely used cloud service providers. At the time of writing this blog, AWS has over 200 services across different domains (Compute, Machine Learning, Security, etc).
AWS services can be managed via two ways:
- AWS Console (Web Interface)
- AWS CLI (CLI-based access)
Most commonly used, public-facing AWS services are as follows:-
- Simple Storage Service (S3)
- Elastic Load Balancer (ELB)
- CloudFront
- Cognito
SIMPLE STORAGE SERVICE (S3)
Simple Storage Service a.k.a S3 is a cloud object storage service providing secure and scalable storage capacity to the customers. S3 stores the data in the form of objects inside storage units known as buckets. These buckets contain the data object, metadata, and a unique identifier. It’s important to note that the S3 bucket names are unique across all buckets in a region, thus no two buckets can have the exact same name. While mainly used for storing data, an interesting feature of these buckets include hosting static websites.
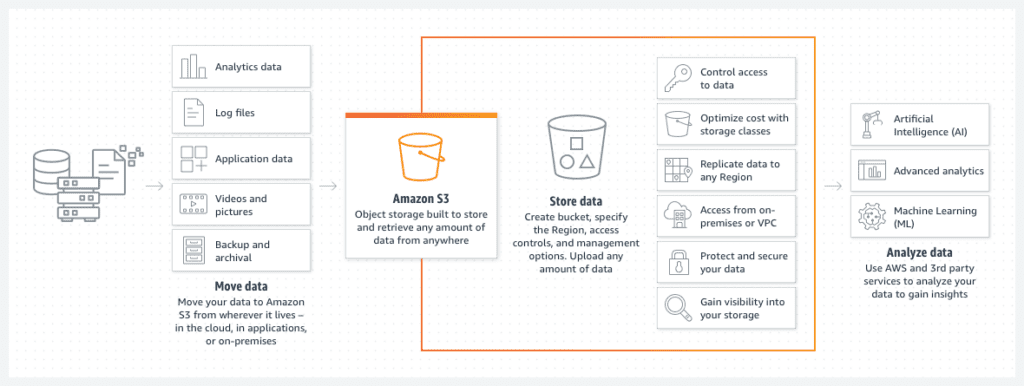
Image Source: https://aws.amazon.com/s3/
URL format
S3 currently provides two naming conventions for the buckets.
- Where bucket name is prepended:
[BUCKET_NAME].s3.amazonaws.com/
For e.g: example.s3.amazonaws.com/
2. Where bucket name is appended:
s3.amazonaws.com/[BUCKET_NAME]/
For e.g: s3.amazonaws.com/example
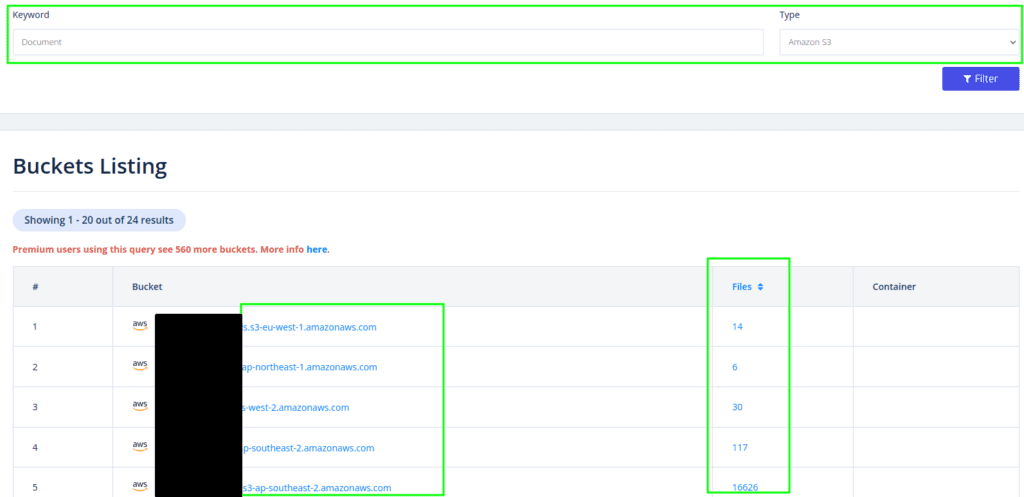
Recon via publicly available Buckets
A large number of buckets are publicly available and accessible to the general public. This ranges the buckets belonging to an individual freelancer to multinational companies. In case we discover a bucket that is misconfigured, it can either yield important information or allow us to gain access to the AWS environment.
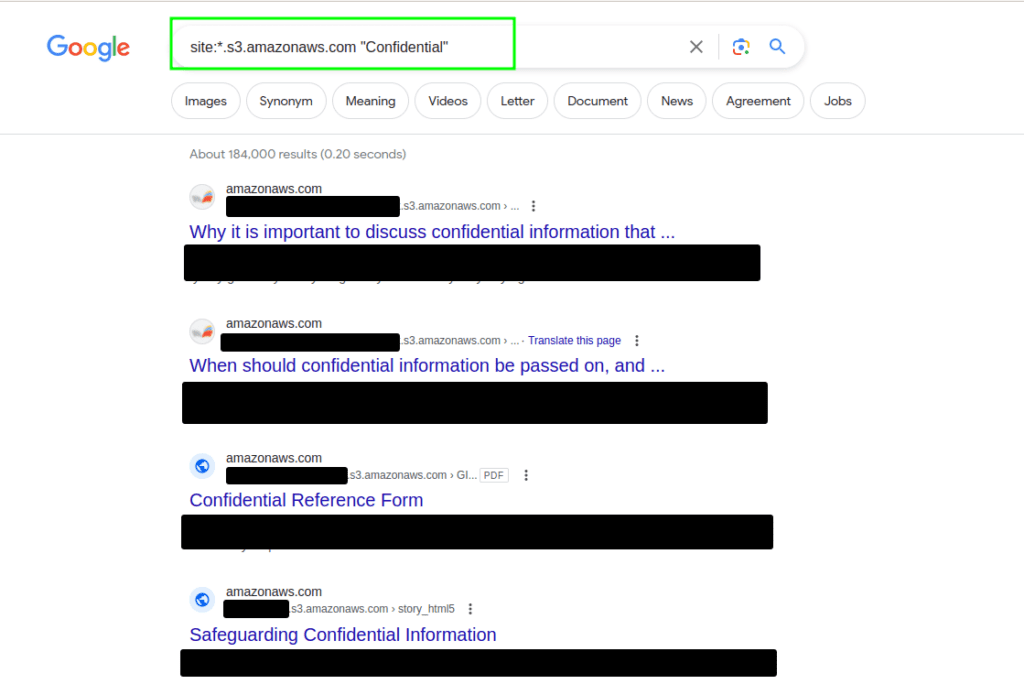
Recon via Google Dorks
- Query 1:
site:*.s3.amazonaws.com "Confidential"
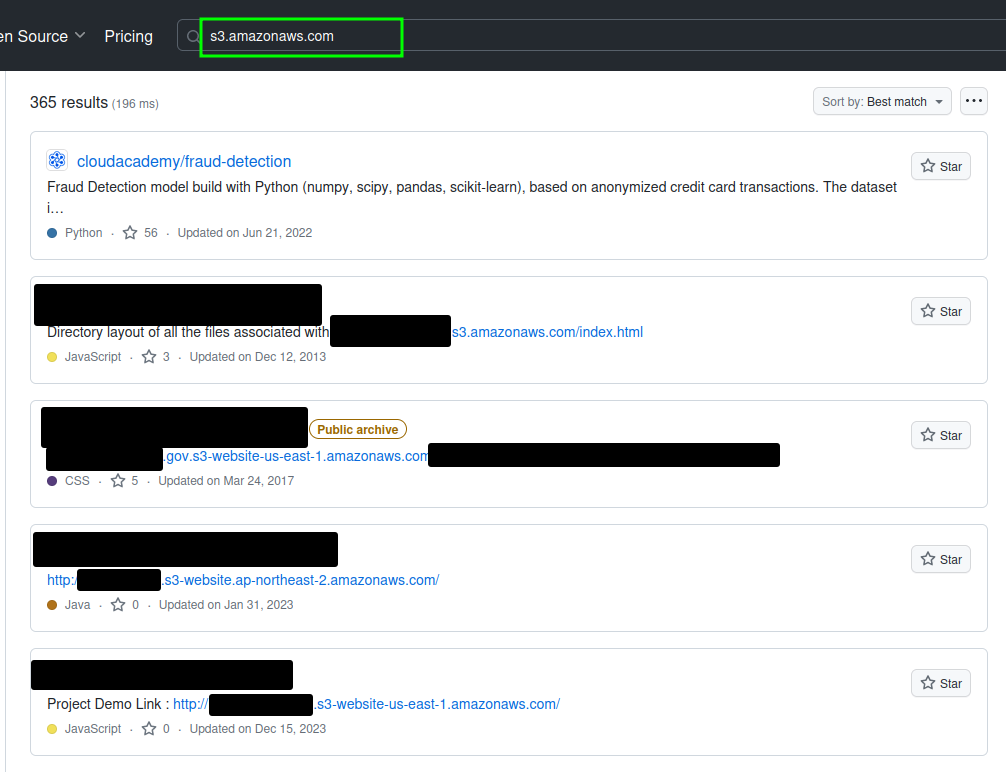
Recon via Github Dorks
- Query 1:
s3.amazonaws.com
ELASTIC LOAD BALANCER (ELB)
Elastic Load Balancer a.k.a ELB is a load balancing service which distributes incoming traffic to different AWS services (IP address, EC2 Instance, Lambda function, etc) based on pre-configured rules across various availability zones.
At the time of writing this blog, AWS provides four different types of ELB’s as follows:
- Application Load Balancer (ALB) – Operates on layer 7 with support for HTTP, HTTPS, and gRPC
- Classic Load Balancer (CLB) – Operates on layer 4 & layer 7 with support for TCP, SSL/TLS, HTTP, and HTTPS
- Gateway Load Balancer (GLB) – Operates on layer 3 & layer 4 with support for IP
- Network Load Balancer (NLB) – Operates on layer 4 with support for TCP, UDP, and TLS
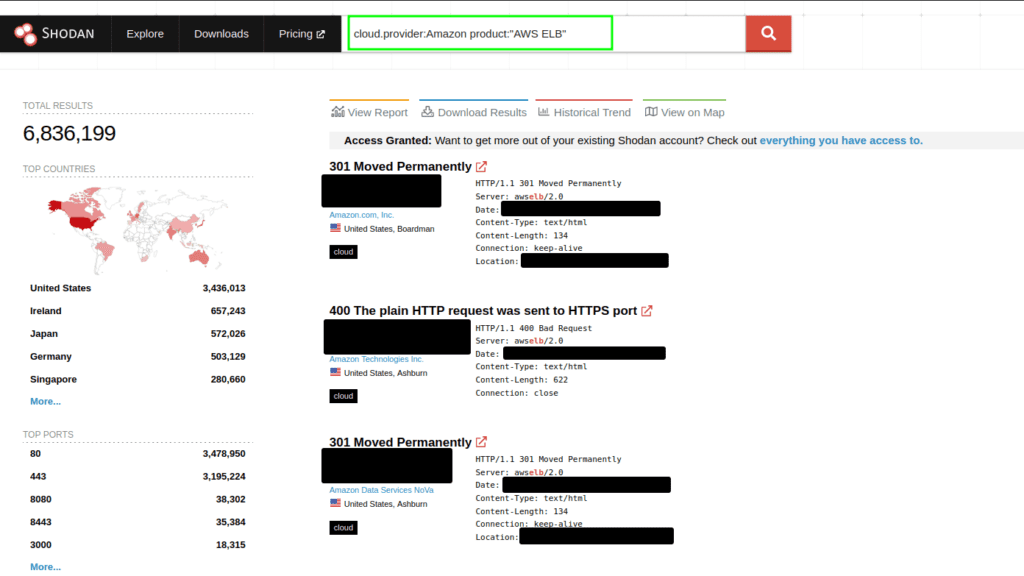
Recon via Shodan
- Query 1:
cloud.provider:Amazon product:"AWS ELB"
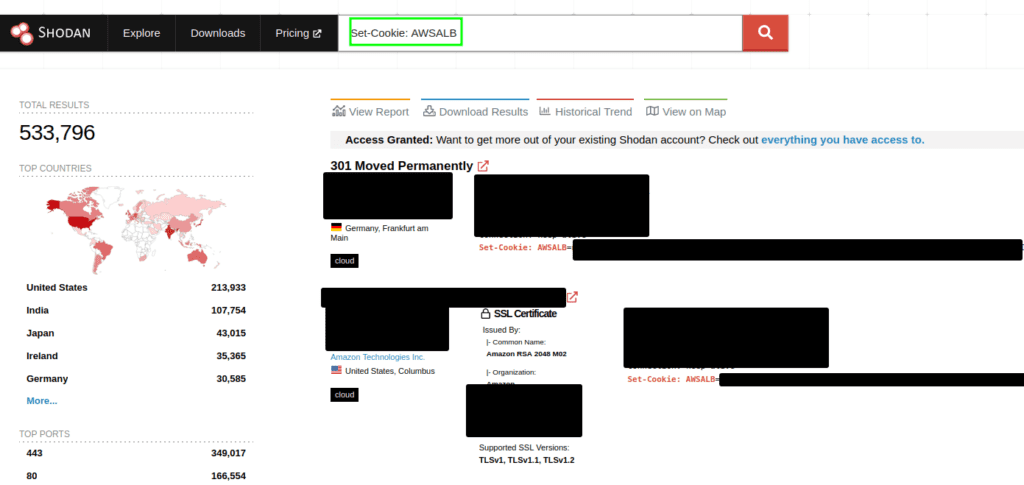
2. Query 2:
Set-Cookie: AWSALB
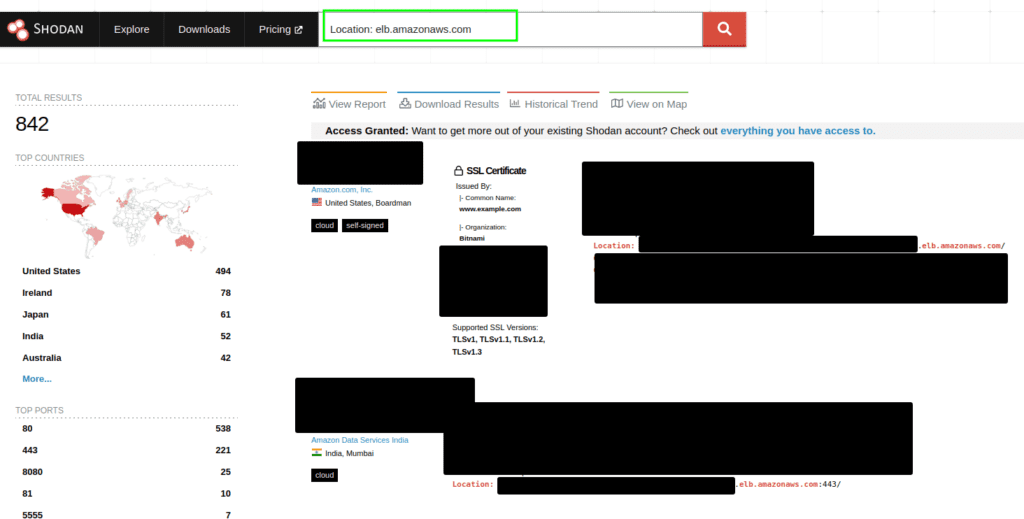
3. Query 3:
Location: elb.amazonaws.com
Recon via Censys
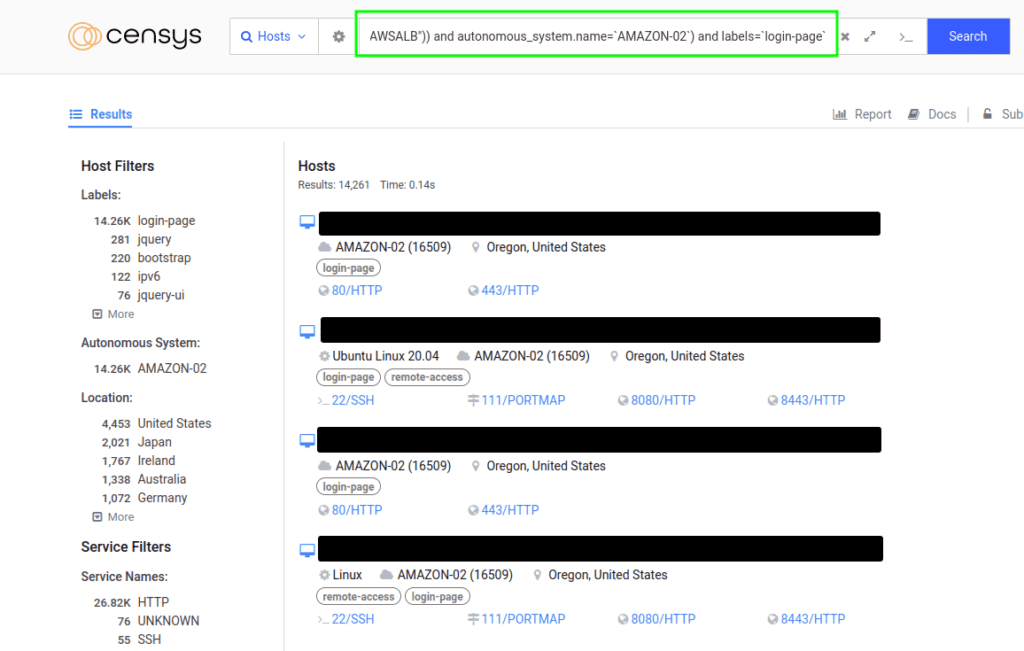
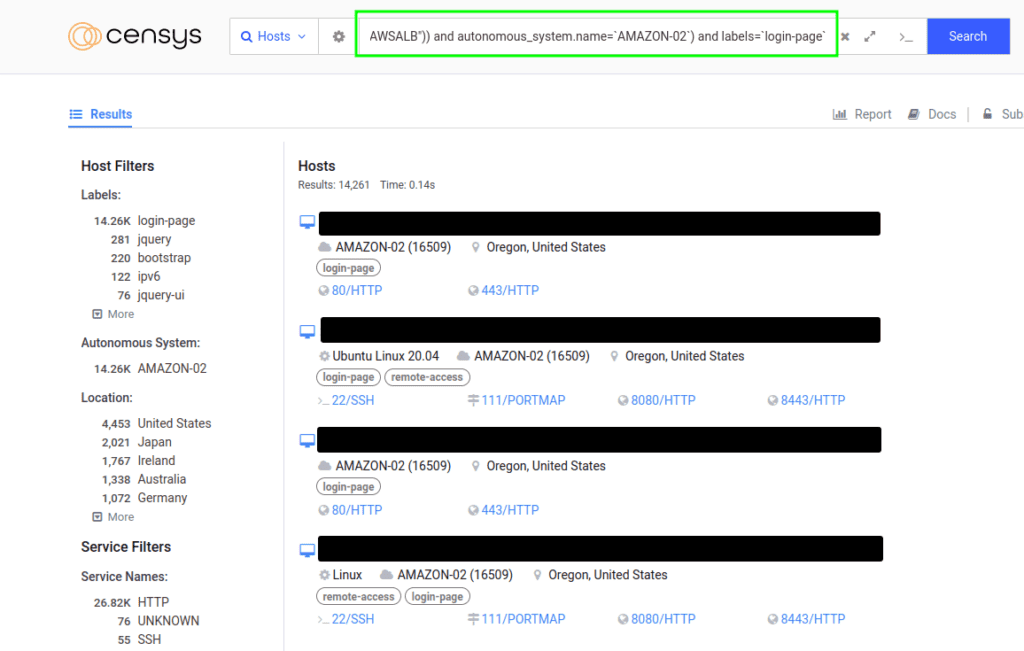
- Query 1:
((services.http.response.headers: (key: "Set-Cookie" and value.headers: "AWSALB")) and autonomous_system.name=`AMAZON-02`) and labels=`login-page`\
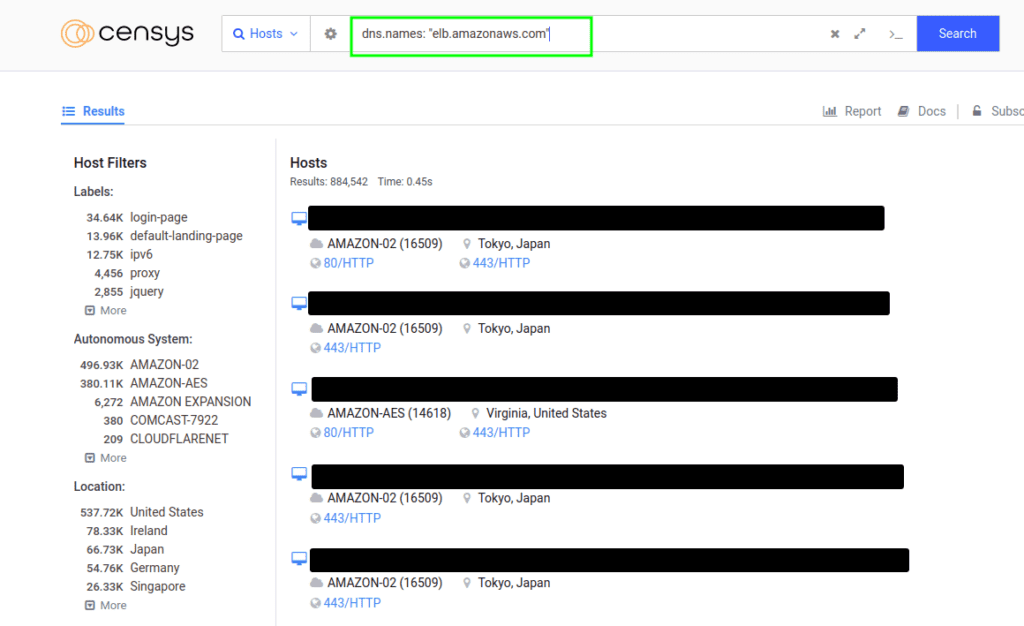
2. Query 2:
dns.names: "elb.amazonaws.com"
CLOUDFRONT
CloudFront is a globally distributed, content delivery network providing low-latency network connectivity across the globe. CloudFront supports the delivery of data (including audio/video), applications, and API among other formats. Additionally, it supports EC2, ELB, and custom origins as the backend (data host).
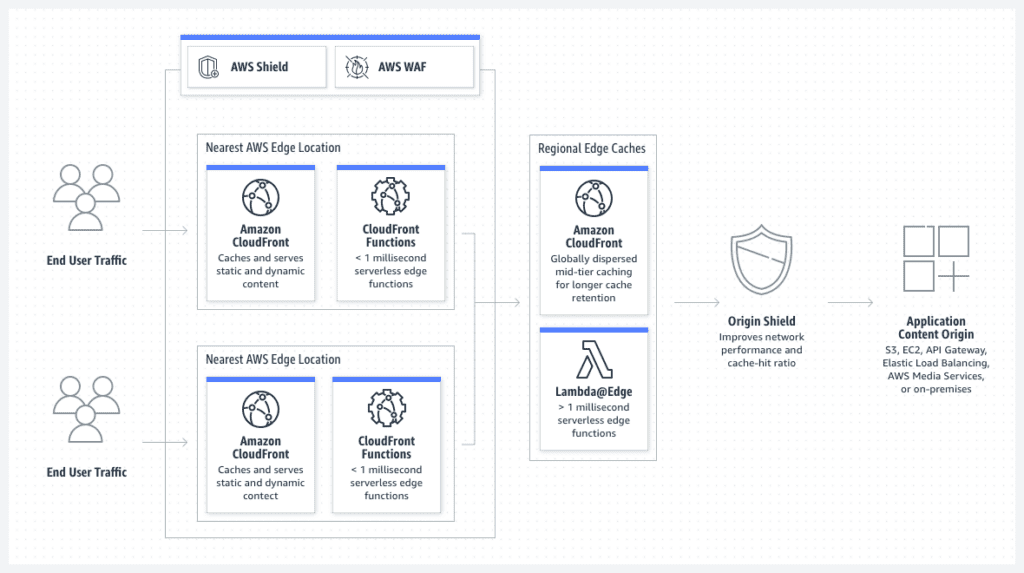
Image Source: https://aws.amazon.com/cloudfront/
Recon via Shodan
- Query 1:
User-Agent: Amazon Cloudfront

Recon via Censys
- Query 1:
(services.http.response.headers.key: "X-Amz-Cf-Id") and labels=`remote-access`
COGNITO
Cognito is a Customer Identity & Access Management (CIAM) service which offers IAM services applications (WebApp, Mobile App, etc).
Cognito provides two kinds of offerings as follows:
- User Pool: Signup/Login based on user directories
- Identity Pool: Access other AWS services through Cognito elements
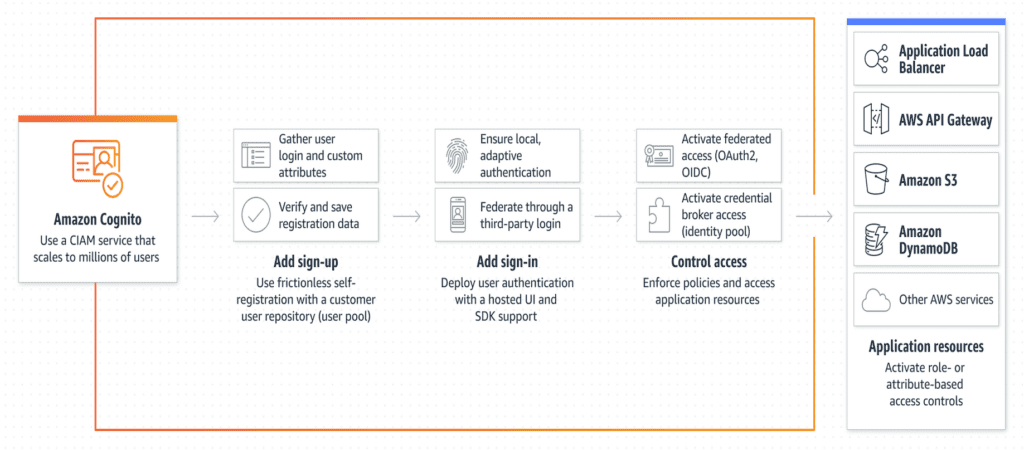
Image Source: https://aws.amazon.com/cognito/
Recon via Shodan
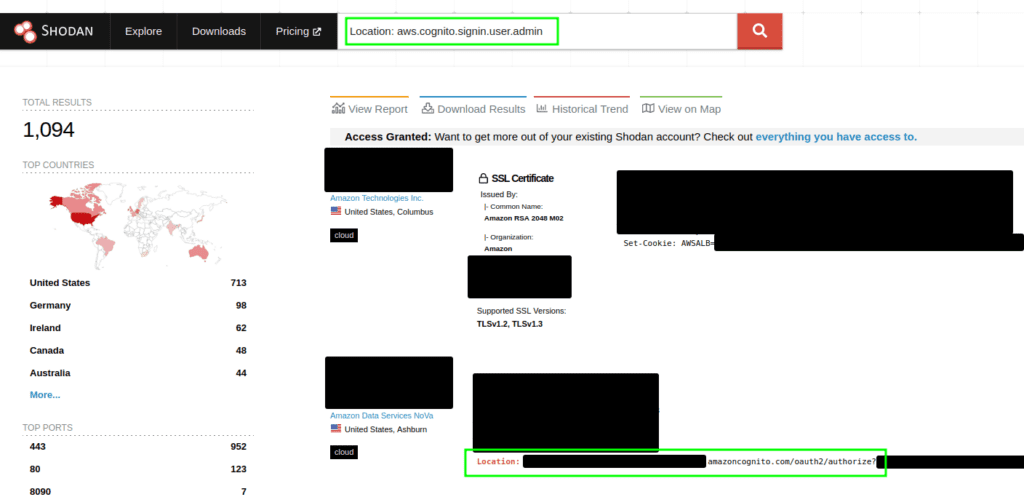
- Query 1:
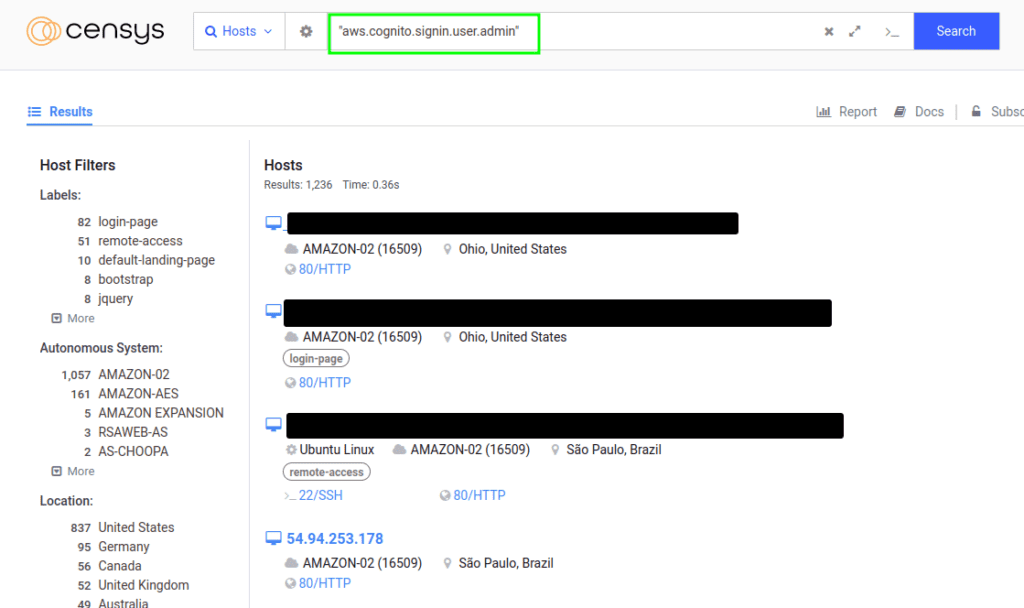
Location: aws.cognito.signin.user.admin
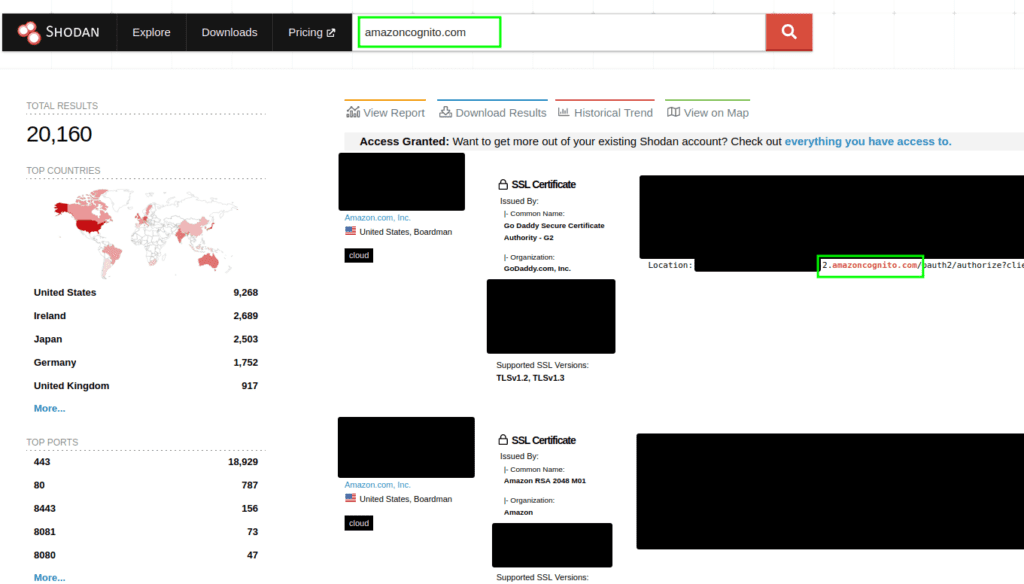
2. Query 2:
amazoncognito.com
Recon via Censys
- Query 1:
"aws.cognito.signin.user.admin"