Become an Active Directory Red Team Specialist: Inside the AD-RTS Course

Overview
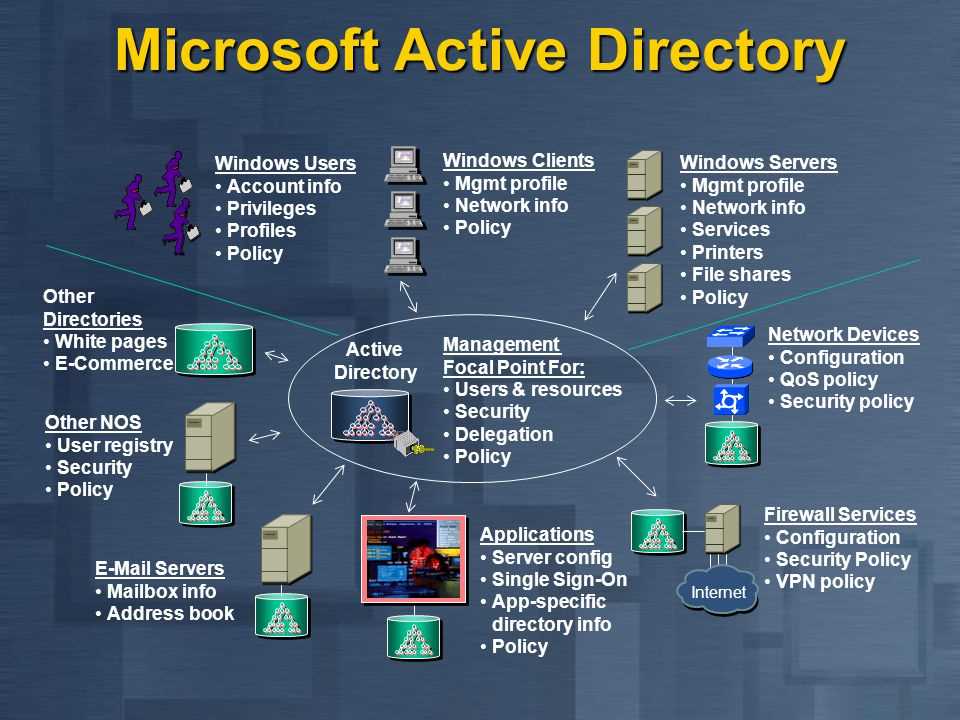
Active Directory powers identity, authentication and authorization across most enterprises and if attackers take control of it, they often gain access to the whole network. The Active Directory Red Team Specialist course is a hands-on, lab‑driven program that teaches offensive practitioners how real adversaries attack AD and its supporting services and how defenders can stop them.
Through a mix of concise theory, live demonstrations, and full cyber‑range exercises, you’ll practice both unauthenticated and authenticated attack techniques. The course shows you how to weaponize common misconfigurations, exploit weakly defended services, and run complete red‑team operations from reconnaissance and initial access to privilege escalation, lateral movement, persistence and data exfiltration.
Prerequisites
To follow the labs confidently you should have:
- Basic web and network penetration-testing knowledge.
- Comfortable using a command-line environment (Linux terminal and PowerShell basics helpful).
- An attacker virtual machine (Kali Linux or Parrot) to run tools and exercises.
What you will learn
Core Active Directory concepts
- AD architecture and core components: Schema, Global Catalog and the NTDS.dit database
- AD objects and Group Policy fundamentals
- Authentication and authorization flows used in AD
Certificate Services (AD CS)
- AD CS architecture, Certificate Authorities, templates and web enrollment
- Certificate Revocation Lists and Certificate Distribution Points
- Common misconfigurations and abuse cases leading to impersonation and privilege escalation
Exchange Server attack surfaces
- Exchange core components: Outlook Web Access, Exchange Web Services, MAPI and Autodiscover
- Targeted privileges such as ApplicationImpersonate and Exchange admin roles
- Real-world attacks: mailbox delegation persistence, import/export mailbox abuse, transport rule backdoors
ESXi and hypervisor risks in AD-integrated environments
- Why ESXi hosts are domain-joined and how that creates risk
- Attack scenarios against ESXi when integrated with AD and demo-driven exploitation
IIS, DNS and web-facing services
- Code injection, VIEWSTATE abuse, and key pillaging from Internet-facing IIS servers
- DNS abuse for unauthenticated initial access and anonymous LDAP reconnaissance
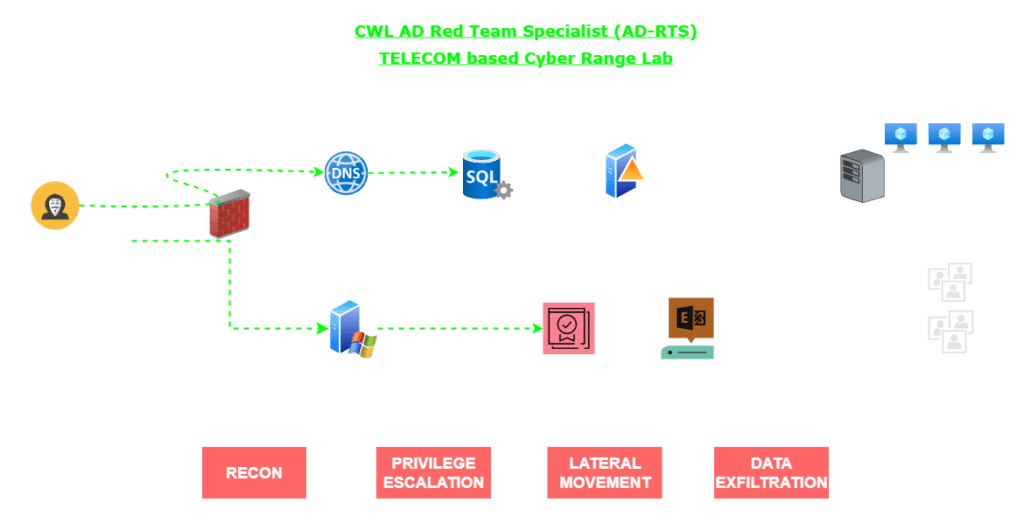
Complete Red Team Operations
- Reconnaissance: DNS abuse, anonymous recon via LDAP, Kerberos PREAUTH and ACL abuse
- Privilege escalation: from service compromise to SYSTEM, SQL Server pivoting, DPAPI decryption, and certificate impersonation
- Lateral movement: Exchange and ESXi-based pivots to Domain Controller and guest VMs
- Data exfiltration: stealthy compression and exfiltration across encrypted channels
Course Structure and Labs
Below is a practical, hands-on breakdown of the course modules. Each module mixes short theory with real demos and lab exercises you can run yourself.
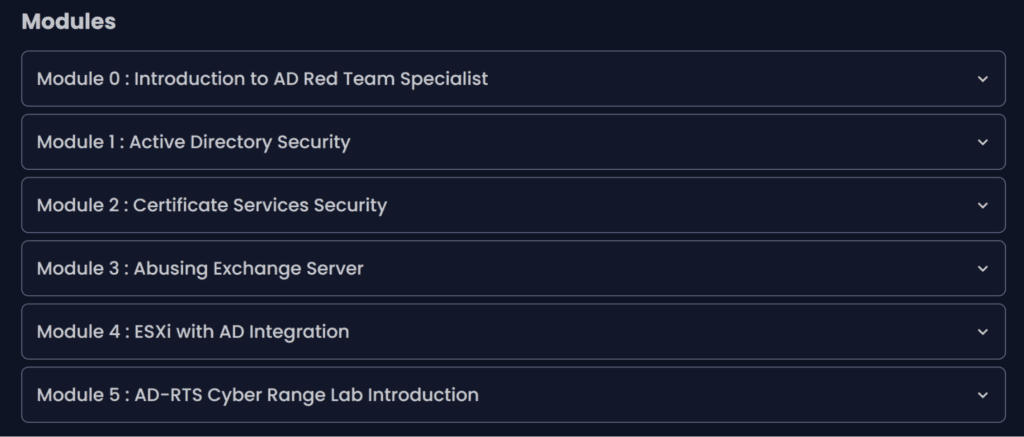
Module 1
Active Directory Security
A friendly introduction to Entra ID and on-prem AD, followed by a clear walkthrough of schema, the Global Catalog, and the NTDS.dit database. You’ll learn how Group Policy and common AD objects shape daily operations and how authentication and authorization flows actually work in practice.
Module 2
Certificate Services Security
We’ll demystify AD Certificate Services: how Certificate Authorities, templates, and web enrollment function, where CRLs and distribution points fit in and the configuration mistakes that let attackers impersonate identities.
Module 3
Abusing Exchange Server Roles
Learn the components that make Exchange a high-value target (OWA, EWS, MAPI,Autodiscover). We’ll show how specific roles are abused for persistence and demo real techniques like mailbox delegation, transport-rule backdoors and ApplicationImpersonate misuse.
Module 4
ESXi Integrated with AD
Understand why organizations domain‑join ESXi hosts and what that means for risk. This module features hands-on demos showing command execution in guest VMs, hypervisor abuse scenarios and concrete administrator-role case studies with mitigation advice.
Module 5
Cyber Range: AD-RTS Lab Part 1 (Unauthenticated Adversary)
A focused lab simulating an unauthenticated attacker: DNS abuse, anonymous LDAP reconnaissance, Kerberos PREAUTH and ACL abuse and classic privilege-escalation chains leading to credential dumping.
Module 6
Cyber Range: AD-RTS Lab Part 2 (Authenticated Adversary)
This lab simulates a logged-in adversary who exploits internet-facing services (IIS, VIEWSTATE) to extract keys, decrypt DPAPI blobs, impersonate certificates and pivot to Domain Administrator.
The full red-team flow is covered: Recon → Escalation → Lateral movement → Data Exfiltration.
Demos and Hands-on Exercises
This course emphasizes learning by doing. Each technical concept is paired with a live demo that demonstrates both exploitation techniques and the practical mitigations defenders should apply.
- Live, side-by-side demos — see attacks executed in a controlled lab and immediately learn how to detect and remediate them.
- Reproducible scripts — ready-to-run tooling for DNS enumeration, Exchange mailbox analysis and abuse, ESXi command execution and other lab activities.
- Realistic scenarios — hands-on exercises such as extracting keys from IIS, abusing Exchange ApplicationImpersonate, creating stealthy mailbox backdoors and exfiltrating sensitive data safely from the lab environment.
Who should attend
This program is intended for:
- Freshers and intermediate penetration testers aiming to specialize in Active Directory offensive techniques.
- Red team and offensive security analysts who need field-tested tradecraft for enterprise environments.
- Security engineers and defenders who want to understand attacker techniques in order to implement stronger controls.
- Anyone interested in practical offensive information security, including SOC analysts and incident responders who want to see attack chains end-to-end.
Why this course is different
- Adversary-focused: The curriculum mirrors real attacker tradecraft against AD, Exchange, Certificate Services and hypervisors.
- Hands-on cyber range: Two multi-stage labs simulate both unauthenticated and authenticated adversaries so you practice the full kill chain.
- End-to-end red team operations: You’ll learn recon, initial access, escalation, lateral movement, persistence and stealthy exfiltration not just isolated tricks.
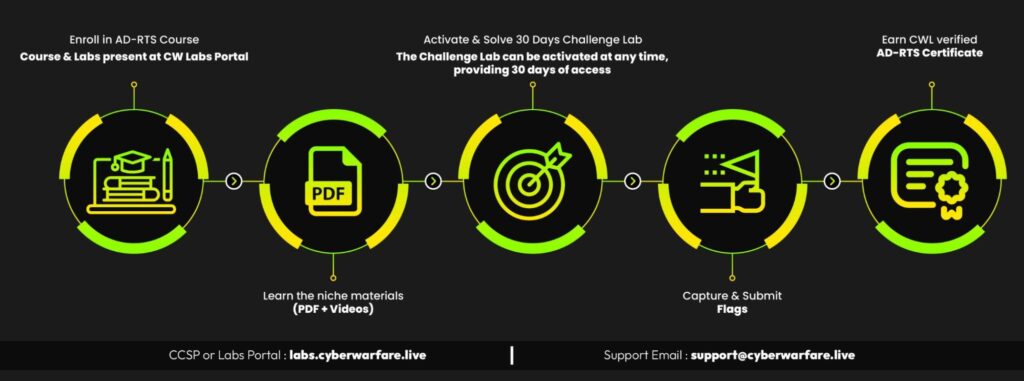
Certification
Complete the course labs and assessments to earn the Active Directory Red Team Specialist (AD‑RTS) certificate. The certification proves you can perform realistic AD-focused red team operations and recommend effective defensive controls.
Conclusion
The Active Directory Red Team Specialist (AD‑RTS) course is a one‑of‑a‑kind, fully practical program that bridges the gap between theory and real‑world attack simulation. Learners gain direct, hands-on experience reproducing and mitigating modern Active Directory, Exchange and Certificate Services exploitation methods in a safe, guided lab environment.
Whether you’re new to red teaming or looking to elevate your offensive and defensive AD skills, this course delivers clear instruction, realistic labs and certification-backed proof of your capabilities. By the end, you’ll be equipped with the mindset, methods and tools to perform advanced red team operations confidently within enterprise networks.



































