Deploying DOTL: Turning Deception into Detection | Part-1

Introduction: From Concept to Implementation
In our first blog, we talked about how attackers stay hideen by using trusted system tools and how Defending Off the Land (DOTL) strategies can reveal them. We also explained how decoys and monitoring unusual behavior can help us detect threats in their early stage.
In this second blog, we will move from understanding the ideas to implementing them. We will look at how to set up traps and use built-in system features to find hidden threats.
Building a strong IT infrastructure isn’t just about depending on security solutions to find threats, it’s about creating an environment where attackers can’t hide themselves as few attacks like Living off the Land (LOTL) can bypass security solutions by taking advantage of applications which are already present in the system. Creating such an environment can be possible by using deception and monitoring techniques which can be used by defenders to detect threats in their early stage.
Deployment Prerequisites
Recommended Lab Setup:-
- Virtual Machine (VM) Platform:VirtualBox, VMware or Hyper-V
- Guest OS: Windows 10 (64-bit)
- RAM: 2 GB recommended (configured with 4 GB for smoother performance)
- Storage: Minimum 60 GB
- Network: Bridged or NAT
With the lab environment ready, the next step is to set up deception artifacts that will help us reveal hidden threats and alert us about any suspicious activity. These artifacts are designed to silently detect malicious behavior and give warnings to defenders.
To create these deception artifacts, we’ll use scripts from the DOTL project by Thinkst.
Defending Off the Land (DOTL) Project Overview
The “Defending Off the Land” (DOTL) project by Thinkst is a collection of scripts that help defenders detect attacks using built-in Windows features. Without the need of additional security solutions, DOTL takes advantage of the system’s own tools to detect suspicious activities.
In this blog, we will focus on two specific tools from the project: registry_monitor, and task_token.
You can explore the full project here- https://github.com/thinkst/defending-off-the-land.
Before we start deploying these tools, let’s go through the common setup steps required to deploy these deception components in the Windows machine.
Common Setup Steps –
- Start Windows powershell as an Administrator, this is required to successfully deploy DOTL components, which requires administrative privileges.
- Download the DOTL Github repository-GitHub Link in your Windows 10 Machine.
a.) Generate Canary tokens by visiting Canarytoken and choose the Web Bug option for the task_token, and registry_token deception deployment.
Note- Create a separate canary token for each deception. This allows you to identify exactly which trap was triggered if an attacker interacts with it.
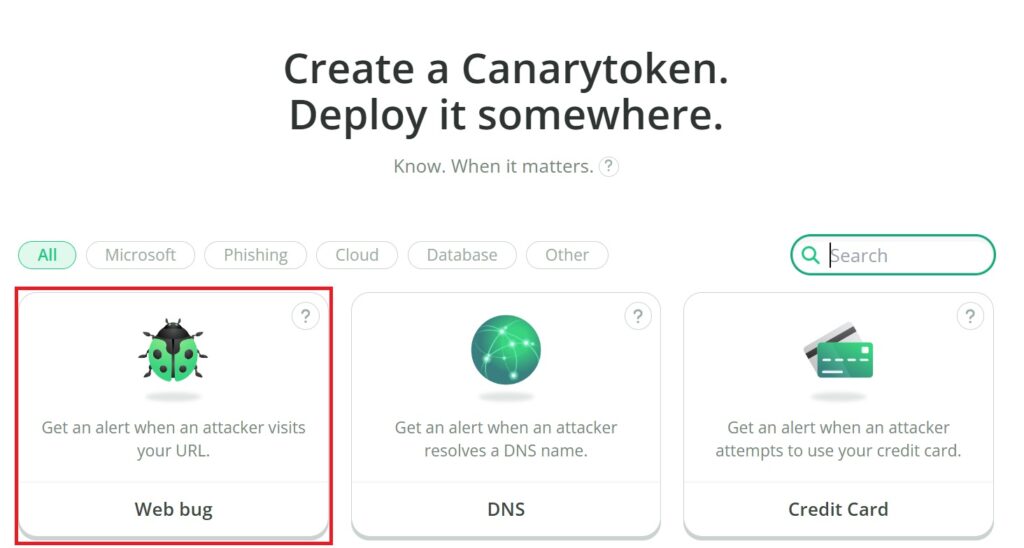
b.) Fill in the necessary information to create a Web Bug token such as the email address where you want the alert to be sent and a name for that alert to identify which decoy was triggered.
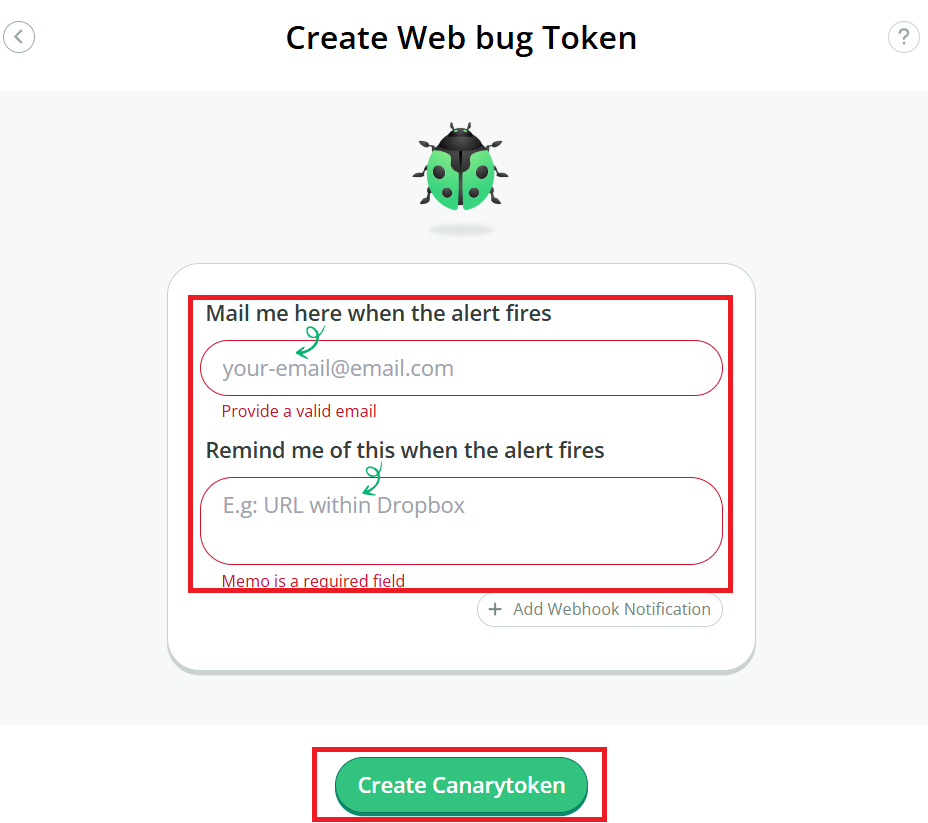
c.) After completing, you will receive a Canarytoken URL for Web Bug.
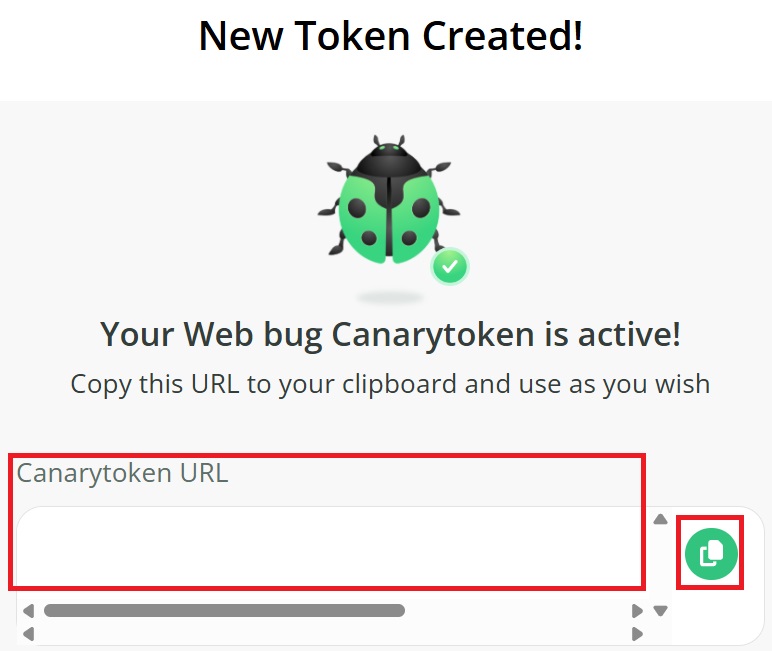
d.) Copy and save the url, as they will be used during the deployment of the deception artifacts.
Now we will deploy the deception components of task_token, and registry_token.
1.) Scheduled Task
- Purpose- Scheduled tasks is a built-in Windows feature (schtasks.exe or Task Scheduler) which is used to automate routine operations such as-
- running scripts (e.g., database backups, service restarts, log cleanup)
- performing backups (files, databases, or system images)
- applying updates (OS patches, software upgrades) and conducting
- tasks maintenance (disk cleanup, temp file removal, security scans).
- LOTL abuse- Since schtasks.exe is a legitimate Windows binary, attackers often misuse it to stay hidden and carry out their malicious activities, such as: Persistence, Evasion and Command Execution.
- DOTL Defense- DOTL deploys a PowerShell script that configures an alerting system for scheduled tasks. If an attacker tries to create, modify, or interact with a scheduled task, an alert will be triggered, giving defenders a warning.
Deployment Steps-
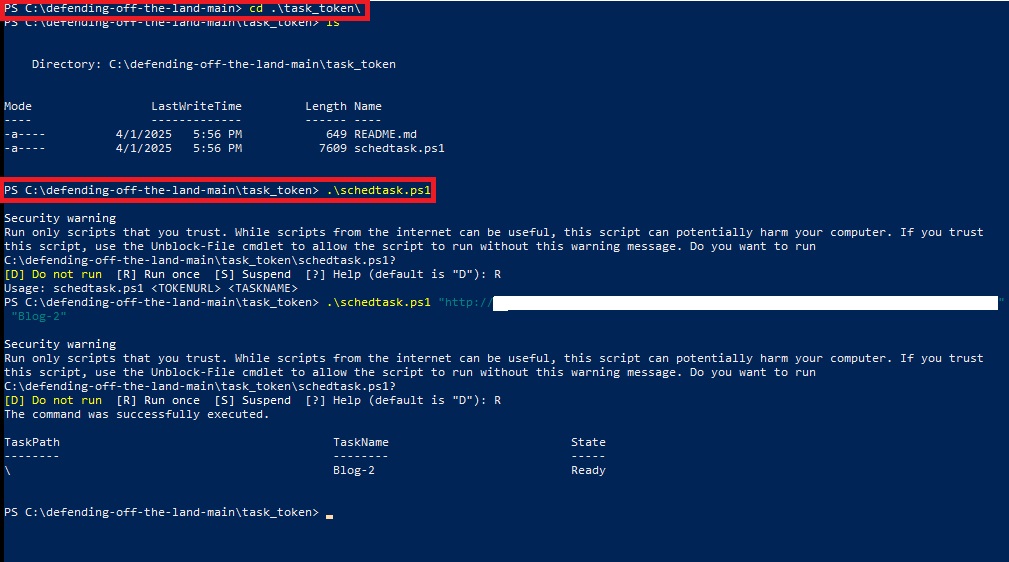
- Use Powershell to navigate to the task_token folder.
- Inside task_token folder, you will find powerShell script named schedtask.ps1.
- Run the powershell script using by the following command-
Command- .\schedtask.ps1 <WebCanaryTokenURL> <token_name>
Replace the mentioned section with custom data:
- <WebCanaryTokenURL>: The URL linked to your web canary token.
- <token_name>: A custom name you choose for the scheduled task.
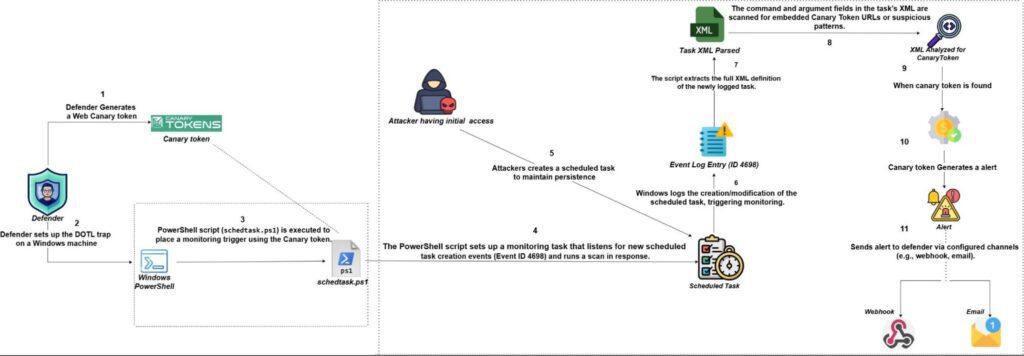
Workflow of the Scheduled Task Deception-
1.) Canary Token Setup & Script Configuration-
Defender generates a Web bug Canary token to act as a trigger to alert a suspicious activity related to scheduled task creation. The schedtask.ps1 script is executed to install a monitoring task on the Windows machine. This task monitors for new scheduled task creation events (Event ID 4698) and runs a scan whenever such an event gets triggered.
2.) Attacker Activity & Scheduled Task Creation-
After gaining initial access, the attacker tries to create a scheduled task to maintain his persistence in the system. Windows logs the task creation, which activates the monitoring script.
3.) Task Scanning & Canary Token Detection-
The script extracts the XML content of the newly created scheduled task and scans the Command and Arguments fields for Canary token URLs. If the script detects a token, it treats it as a malicious task.
4.) Alert Generation & Notification-
Then the script generates an alert and sends it to the defender through a configured communication channel (e.g., webhook or email) to notify them of potential malicious activity.
- Windows Registry
- Purpose- The Windows Registry is a hierarchical database that stores critical system, application, and user configuration data, including-
- System-wide settings (e.g., boot configurations, driver settings)
- Application configurations (e.g., startup programs, license keys)
- User-specific preferences (e.g., desktop settings, file associations).
- LOTL Abuse – Attackers can modify or add registry keys to automatically run malicious programs during system boot or user login, helping them maintain persistence.
- DOTL Defense – DOTL monitors a predefined list of sensitive registry keys (mentioned in keys.json). It periodically checks these keys for any unauthorized access, modification, or deletion. If any changes are detected, it triggers a local balloon notification and sends an alert.
Deployment Steps-
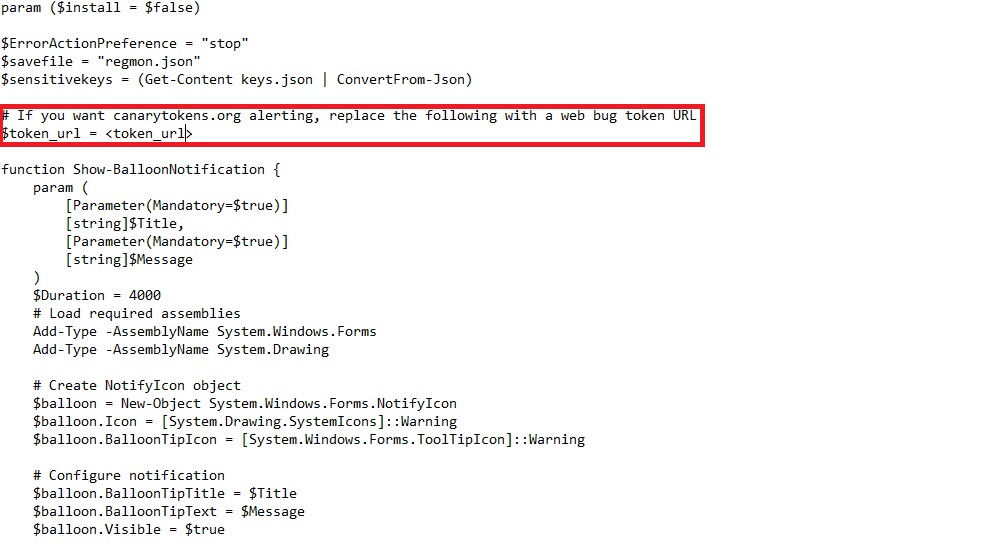
- Go to the defending-off-the-land folder using File Explorer.
- Next, open the registry_monitor folder. Right-click on reg-check.ps1, select Notepad, paste your canary token into the $token_url section, and save the file.
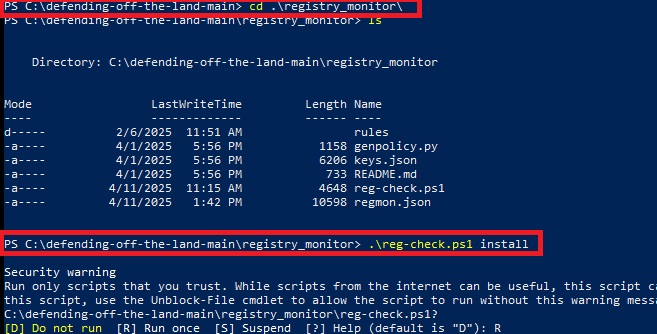
- After that, navigate to the registry_monitor folder in PowerShell and run the following,
Command: .\reg-check.ps1 install
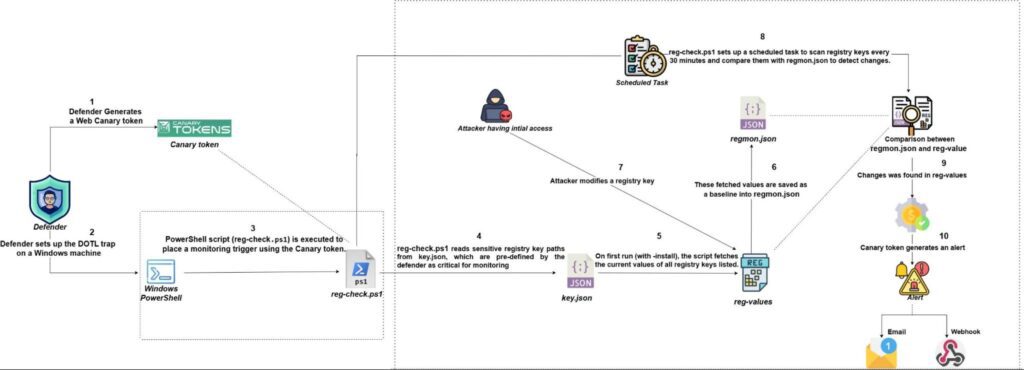
Workflow of the Windows Registry Deception-
1.) Canary Token Setup & Script Configuration-
- The defender generates a Canary token to act as a trigger for alerting on suspicious registry changes.
- The reg-check.ps1 PowerShell script is deployed on a Windows machine to monitor sensitive or critical registry keys. It reads these keys from the keys.json file and sets up regular checks for any change.
2.) Baseline Snapshot Creation-
The script reads the registry values for critical or sensitive keys (listed in keys.json), gets their current values from the Windows Registry, and saves this data as a baseline in regmon.json. This baseline serves as the refernce state for future comparisons.
3.) Scheduled Task for Periodic Checks-
A scheduled task runs the script every 30 minutes, triggering a comparison between the current registry values and the reference state in regmon.json. The script uses Compare-Object to detect any changes.
4.) Change Detection & Canary Token Trigger:
When a change is found, the script triggers the Canary token. This sends an alert through email or webhook to notify the defender of the suspicious registry changes.
Conclusion: Turning Concepts into Action
In this part of the blog, we explored how DOTL takes advantage of built-in Windows features to detect and respond to threats without the help of any security solutions. We went through the deployment and functioning of two key deception components: task_token, which monitors for unauthorized scheduled tasks, and registry_monitor, which detects suspicious registry changes.
In Part 2, we will continue this blog by exploring additional DOTL deception modules like service_token, file_access_token, and techniques for monitoring remote access through RDP/WinRM.


































